What is AES encryption?

When it comes to encryption, AES, or Advanced Encryption Standard, is king. It’s the leading form of encryption in use today, trusted by the likes of the U.S. government and renowned for its speed, strength, and efficiency.
You’ve likely heard of it, and you’ve inevitably used and benefitted from it, since it’s an integral element of secure Wi-Fi connections, email platforms, instant messaging apps, cloud storage services, virtual private networks (VPNs), and more. However, you might not know exactly how AES works and what separates it from other forms of encryption.
This guide is here to fill in the blanks, exploring what AES encryption is, how it works, where it’s used, and what the future holds for it.
A quick overview of AES
As stated above, AES stands for Advanced Encryption Standard. It’s a symmetric block cipher encryption algorithm, used for transforming plaintext into ciphertext and securing data, both at rest and in transit.
AES is based on the Rijndael cipher, which was created by a pair of Belgian cryptographers named Joan Daemen and Vincent Rijmen. They published their work in 1998, and it was officially established by the U.S. National Institute of Standards and Technology (NIST) in 2001.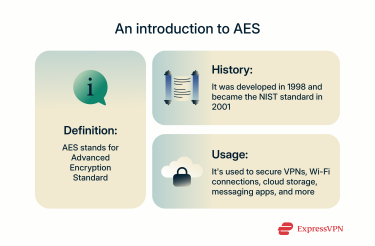 Since then, AES has become the go-to encryption standard of choice for governments, businesses, and cybersecurity specialists the world over. In the process, it replaced older standards, like Data Encryption Standard (DES), due to its superior cryptographic strength and flexibility, which allows it to be used in various technological fields.
Since then, AES has become the go-to encryption standard of choice for governments, businesses, and cybersecurity specialists the world over. In the process, it replaced older standards, like Data Encryption Standard (DES), due to its superior cryptographic strength and flexibility, which allows it to be used in various technological fields.
How AES encryption works
Put simply, AES takes blocks of plaintext and applies multiple rounds of substitution and permutation using a secret key (it’s worth noting that in AES, the key doesn’t come from the algorithm itself; it’s something you or a system choose or generate separately, for example, by using a random number generator). The key is expanded into round keys that drive the encryption, and the same key is needed to decrypt the ciphertext and recover the original data.
Here’s a closer look at some of the key features and aspects of the AES encryption process:
Symmetric key structure
Encryption algorithms can be divided into two categories: symmetric and asymmetric. Symmetric encryption systems use the same encryption key to both encrypt and decrypt data, while asymmetric methods use two separate keys: one public key for encryption and a secondary private key for decryption.
AES is a symmetric algorithm, meaning that the same key is used at both ends of the encryption process.
Block size and key lengths
AES is a block cipher algorithm, meaning it divides data into blocks of 128 bits and encrypts each block independently, albeit with the same encryption key. Each 128-bit block of data is arranged in a four-by-four grid, and each square of that grid contains eight bits, or one byte, of data.
While the block size is always the same, the length of the encryption key used in AES can vary. To be more precise, there are three different key sizes:
- 128-bit: This is the smallest key size and involves 10 rounds of encryption. Despite being the smallest and technically least secure of the three key lengths, it’s still exceptionally difficult to crack, with more than 340 undecillion possible key combinations. (For context: that’s a billion trillion trillion times the number of grains of sand on Earth).
- 192-bit: 192-bit keys involve 12 rounds of encryption and even more possible key combinations, making them stronger than 128-bit keys. They provide a balanced compromise between the security of 256-bit keys and the speed of 128-bit keys.
- 256-bit: 256-bit keys are the most secure of all, used in applications that demand the highest standards of security. These keys involve 14 encryption rounds in total and are generally considered as secure against future quantum threats as 128-bit AES keys are against conventional threats.
Key schedule and rounds explained
As touched on earlier, AES involves putting plaintext data through multiple stages, or “rounds,” of encryption. Each round involves four transformations:
- SubBytes: Each byte in the block is replaced with a corresponding byte in a preset substitution box, or S-box. This is an example of substitution encryption.
- ShiftRows: The bytes in each row are shifted to the left. This is an example of permutation encryption, since it involves moving data around, rather than replacing it.
- MixColumns: The columns of the four-by-four grid are mixed around again, with a mathematical operation applied to each column in another example of permutation.
- AddRoundKey: Lastly, the new data block is combined with a round key, which is derived from the key schedule.
Each round requires a unique round key, all derived from the single master encryption key. The key schedule is the part of the AES algorithm that essentially generates the necessary round keys.
What is AES encryption used for?
AES is the global standard when it comes to encrypting sensitive digital data across numerous applications and industries. Some of its many applications include:
- Wi-Fi security: AES is the de facto encryption algorithm used in modern Wi-Fi security protocols such as Wi-Fi Protected Access 2 (WPA2) and WPA3 to protect data transmitted over Wi-Fi networks. It keeps unauthorized users from being able to view and access your traffic when accessing the web via Wi-Fi.
- Email and instant messaging apps: Many popular email providers and messaging apps, such as Gmail, WhatsApp, and Signal, use AES encryption to protect your messages, so only you and the person you communicate with can read the contents.
- Secure site and application logins: AES is used within Transport Layer Security (TLS) to encrypt login credentials and other sensitive data when connecting to online services like banking platforms or social media sites.
- VPN connections: Many of the most popular and effective VPN protocols, including ExpressVPN’s Lightway, rely on AES encryption, often using 256-bit keys to provide users with the safest and most private online experiences.
- Cloud storage: Cloud storage platforms generally use AES encryption to secure the various files and pieces of data users store on them, helping to keep data safe even when it’s stored outside of private devices.
- Password managers: Password managers, like ExpressVPN Keys, use AES encryption to secure the vault where all of your passwords and other pieces of sensitive information, like credit card numbers, are kept.
AES modes of operation: CBC vs. GCM
AES can be implemented through various modes of operation, each of which has its own way to apply the cipher and encrypt or decrypt data. Two of the most common modes of operation are CBC and GCM. Here’s a closer look at how they compare.
What is AES-CBC?
CBC stands for “cipher block chaining.” It involves running a process called “exclusive or,” or XOR, on each block of data prior to encryption. CBC also requires a random Initialization Vector (IV) to ensure the first block is unique. This introduces an element of dependency between blocks and ensures that even identical plaintext blocks produce different and distinct ciphertext blocks.
However, the CBC system has some issues. Notably, encryption has to occur sequentially, since each block depends on the previous one. That means that this process can be slower and consume more resources than more efficient methods. In addition, CBC lacks any built-in authentication system.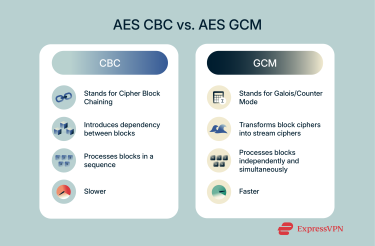
What is AES-GCM?
GCM stands for Galois/Counter Mode. It works quite differently from CBC, using Galois field multiplication and the counter method of operation, which basically turns block ciphers into stream ciphers. Because of this, it’s able to process blocks in parallel and encrypt multiple at the same time, which is faster.
The GCM method also has a built-in authentication system, so it’s not just able to scramble data but also verify its integrity and authenticity and spot any signs of tampering.
Which mode is more secure?
CBC is still considered secure when used with a random IV and paired with an authentication method like Hash-Based Message Authentication Code (HMAC). However, GCM is the modern default: it’s faster, provides built-in authentication, and is more resilient to common attacks such as padding oracle exploits.
Is AES still considered secure?
In a word, yes. AES is considered highly secure, which is why it’s still used far and wide as the leading standard for data encryption. It has been tested and proven to withstand a range of cryptographic attacks.
However, it’s not perfect. As touched on earlier, the security of AES often comes down to the security of the encryption key. If the key is compromised somehow, the whole system falls apart, and certain cyberattacks, such as side-channel attacks and social engineering, can expose weaknesses in the AES algorithm.
Brute force and known attacks
A brute force attack basically involves trying every possible key combination of an encryption cipher, with the aim of eventually landing on the right one. While brute force attacks can theoretically figure out AES encryption keys eventually, there are so many different possibilities, especially with 256-bit AES, that it would take even supercomputers trillions of years to try every single one.
Thanks to this, brute force strikes pose only minimal threat to AES, and the same goes for most other known attack methods. Various theoretical key attacks have been proposed and published by cryptographers over the years, for example, but are either unworkable or would still take billions of years to crack the encryption key.
Side-channel attacks, however, pose a slightly bigger risk. These attacks focus on gleaning clues from the computer as it carries out the encryption in order to reduce the time needed for a successful brute force attack. However, when implemented properly, with the necessary security measures in place, it’s very difficult for side-channel attacks to succeed.
Arguably the biggest risk to AES encryption is human error or weak human-made protections. You can have AES encrypt your data, for example, but then secure it all with a weak password that cybercriminals could easily guess, rendering the encryption worthless. Criminals can also use the likes of keyloggers and social engineering attacks to obtain passwords and access to AES-encrypted data.
AES and quantum threats
As we approach the age of quantum computers, many conventional encryption methods are under threat. This is because quantum computers operate in a completely different way to conventional ones, powered by the principles of quantum physics, which could allow them to easily break through most modern encryption algorithms, especially those that use asymmetric keys.
However, as a symmetrical cipher system, AES is relatively quantum-resistant. Quantum computers are expected to be able to brute force their way through AES twice as fast as standard computers, but this is still a huge amount of time.
What is the difference between AES and RSA?
Rivest–Shamir–Adleman (RSA) encryption is an asymmetric encryption algorithm, using a public key to encrypt the data and a private key to decrypt it. This makes it very different from AES, which is a symmetric method with just one key for both encryption and decryption.
RSA key sizes tend to be much longer than those used in AES, with some over 4,000 bits long, and it’s typically used for secure data transmission and key exchange protocols, mostly with small amounts of data, since it would take a long time to encrypt larger data sets.
Summary: Should you trust AES in 2025?
Yes, AES can still be trusted in 2025, particularly 256-bit AES, which is by far one of the most secure encryption systems in use today. It’s trusted by governments, intelligence agencies, and leading cybersecurity specialists; proven to be resistant against most known forms of attack; and even considered relatively future-proof for the upcoming age of quantum computers, too.
FAQ: Common questions about AES encryption
Can AES encryption be broken?
Yes, while Advanced Encryption Standard (AES) encryption is incredibly secure, it’s not impenetrable. It’s highly resilient to various forms of cyberattacks, like brute force attacks, but the security of AES ultimately comes down to how well the cryptographic key is protected. If the key becomes compromised, so, too, does the encrypted data.
What is the most secure AES key length?
256-bit keys are the most secure options, since they are longer than the alternatives (128-bit and 192-bit keys) and have more rounds of encryption (14, compared to just 10 rounds for 128-bit keys and 12 rounds for 192-bit keys).
Is AES used in VPNs?
Yes, Advanced Encryption Standard (AES) encryption is used in many VPN protocols, including ExpressVPN’s Lightway (which also supports ChaCha20), OpenVPN, IKEv2, and others. In most cases, a 256-bit key is used for AES VPN connections, providing maximum protection for the end user.
What’s the difference between AES-128 and AES-256?
Advanced Encryption Standard (AES) can use three different key lengths, with 128-bit at one end of the spectrum and 256-bit at the other. Both are strong and secure, but there are some key differences between them:
- Length: 256-bit keys are significantly longer and more complex than 128-bit keys.
- Number of rounds: 128-bit keys involve 10 rounds of encryption, while 256-bit keys put data through 14 encryption rounds in total.
- Performance: Because of the smaller key size and fewer rounds, 128-bit AES is the faster and less resource-intensive of the two methods, making it better suited to limited and low-power devices.
- Security: Thanks to the much longer key, additional encryption rounds, and far greater quantity of possible key combinations, 256-bit AES is more secure than 128-bit AES. That doesn’t mean that 128-bit AES isn’t secure, because it is, but 256-bit AES is even more secure and resilient to the likes of brute-force attacks and emerging threats.
Is AES the strongest encryption?
It’s certainly one of the strongest encryption methods, although it’s difficult to definitively state that one particular algorithm is the absolute “best” or “strongest” compared to all the others when comparing exceptionally secure algorithms that have never been cracked. There are other robust methods available, though, most notably ChaCha20.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN