What is Blowfish encryption, and how does it work?

Blowfish is a fast, flexible encryption algorithm designed to protect data using a shared secret key. While it’s an older algorithm, it’s still commonly used in legacy systems and for password hashing in the bcrypt tool.
It’s a good encryption algorithm for older machines, but newer algorithms like Advanced Encryption Standard (AES) have largely replaced Blowfish thanks to their superior security and better performance on modern hardware.
This article will explain what the Blowfish algorithm is, how it’s used, and what its limitations and weaknesses are.
What is the Blowfish algorithm?
Blowfish is a symmetric key block cipher, designed for speed and secure data encryption. It breaks data down into fixed block-size chunks and then scrambles it repeatedly using a secret key to guide the process.
It’s highly versatile because it allows a choice of key sizes ranging from 32 to 448 bits. This means users can balance speed and security.
Why Blowfish was created and who developed it
Cybersecurity researcher Bruce Schneier designed Blowfish in 1993 to address weaknesses in older block ciphers. At the time, Data Encryption Standard (DES) and the International Data Encryption Algorithm (IDEA), two competing encryption algorithms, were either limited by patents or slowed down on modern hardware, or both.
Schneier wanted a fast algorithm that didn’t cost anyone additional licensing fees to use. He published Blowfish as unpatented, royalty‑free code that was compatible with a wide range of software and hardware.
The variable key length also meant it could meet export restrictions while still offering strong protection. Schneier later created Twofish, which was a significant improvement on Blowfish. Despite that, Blowfish is a historical benchmark in encryption technology.
What makes Blowfish different from other encryption algorithms?
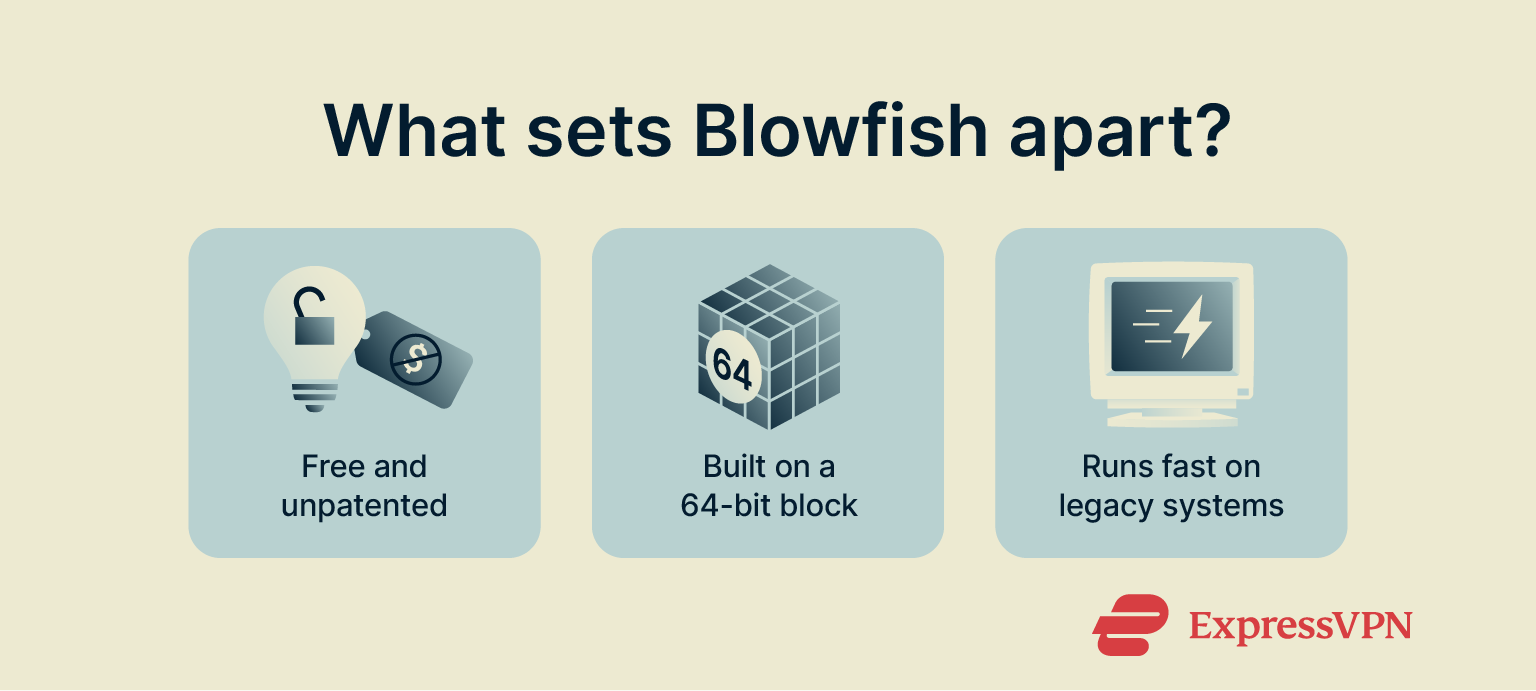 Blowfish works on 64‑bit blocks rather than the modern industry-standard 128-bit blocks. Additionally, users can choose variable key sizes between 32 and 448 bits rather than the fixed 128-, 192-, or 256-bit key sizes that are offered by AES. Essentially, Blowfish can be made compact to run more efficiently on older systems.
Blowfish works on 64‑bit blocks rather than the modern industry-standard 128-bit blocks. Additionally, users can choose variable key sizes between 32 and 448 bits rather than the fixed 128-, 192-, or 256-bit key sizes that are offered by AES. Essentially, Blowfish can be made compact to run more efficiently on older systems.
Because it’s freely available, Blowfish gained popularity early on. However, the small block size leads to unique risks and drawbacks, especially when large amounts of data are encrypted under one key.
Modern ciphers have since addressed the vulnerabilities within Blowfish by using larger block sizes. Because of this, newer options have largely replaced Blowfish in most applications.
How does Blowfish encryption work?
Blowfish is built around a 16‑round Feistel network, meaning it works by splitting data blocks and then scrambling them into ciphertext using a secret key. Here’s how.
Key size, block size, and structure
Blowfish operates on 64‑bit blocks and allows key sizes from 32 to 448 bits. Its 64-bit block size means it breaks data up and encrypts it in 64-bit chunks. Its variable key length allows it to work efficiently on both modern and outdated systems; longer keys are harder to guess with brute-force attacks, but they put more strain on the system.
While it was a strong choice for encryption when it first came out, Blowfish has since been largely replaced with stronger algorithms that use a 128-bit block size.
Feistel network and encryption rounds
Blowfish can operate effectively thanks to the Feistel network structure, which allows you to take a plaintext block, split it into two halves, then encrypt and decrypt these blocks using a secret key. After the data is split, it uses complex math (the F-function) to encrypt half of the data. That encrypted data is then replaced with the other half of the data, which is then scrambled, too.
This means that each 64‑bit block is divided into two 32‑bit halves, and those halves are then scrambled over 16 rounds. The same secret key is used for both encryption and decryption; decryption repeats the rounds in reverse order. Because the algorithm only uses simple operations, the process is fast and efficient, even on outdated hardware.
Blowfish uses exclusive OR (XOR) as part of its mixing process inside each round. Put simply, XOR is a logical operation that compares two bits and outputs 1 if they differ and 0 if they match. Applied inside each Feistel round, this helps scramble the data. When combined with the Feistel network, this ensures that the ciphertext no longer resembles the plaintext.
Blowfish encryption and decryption process
Before encrypting data, Blowfish performs a key expansion process. It starts with a constant set of 18 subkeys (called the P-array) and four substitution boxes (called S-boxes), all initialized using the hexadecimal digits of pi. The user’s secret key is then mixed repeatedly into these initial values to produce the final P-array and S-boxes used for encryption.
This key expansion involves repeatedly encrypting an all-zero 64-bit block and using the output to replace entries in the P-array and S-boxes. Although this process is computationally intensive, it only needs to be done once for each key.
When encrypting a 64‑bit block, Blowfish applies 16 Feistel rounds. Each round uses a subkey from the P‑array to scramble the halves before swapping them. After the final round, the two halves are combined with the last two subkeys to produce the final encrypted block. Decryption uses the same rounds in reverse order with the subkeys reversed.
Despite the complex key schedule, the data encryption and decryption are efficient, requiring only simple arithmetic and lookups (retrieving a value from a pre-computed table). The most computing-intensive part happens when Blowfish first generates the P-array and S-boxes.
What is Blowfish encryption used for?
Blowfish’s speed and free availability meant it was adopted by a wide array of systems. While modern systems have embraced newer encryption standards like AES, Blowfish is still used in legacy software and by users who need low overhead and flexible key lengths.
Common use cases in software and systems
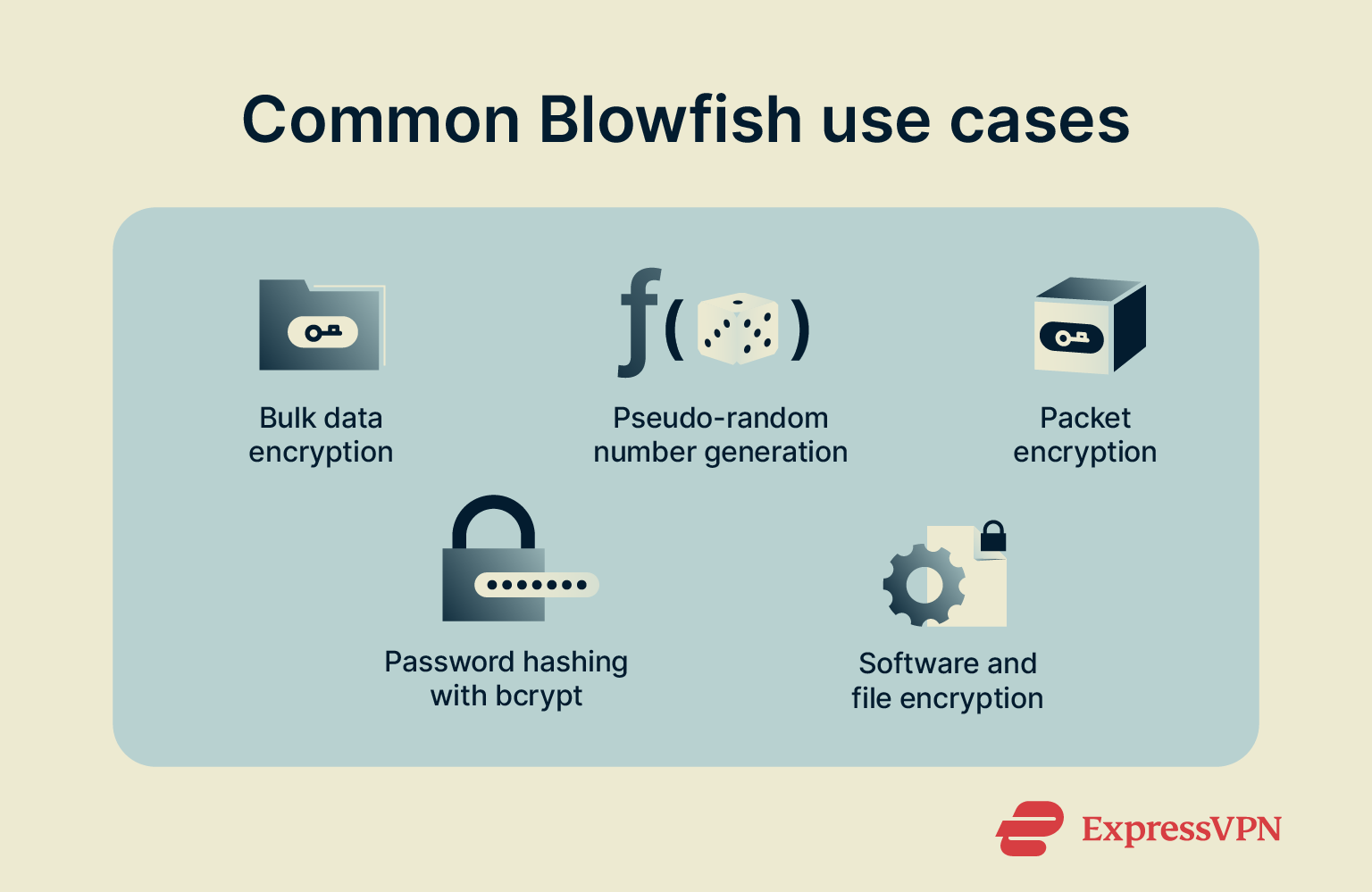
- Bulk encryption: Blowfish can encrypt data streams or files in 64‑bit blocks. However, this is risky if you’re encrypting more than approximately 30GB with the same key, and modern encryption methods like AES are more secure and fulfill this function better.
- Random bit generation: Some systems use Blowfish alongside other software to generate pseudo-random numbers, primarily for ciphertext.
- Packet encryption and VPNs: Modern VPNs like ExpressVPN mostly rely on AES, but older VPN protocols frequently used Blowfish. For example, OpenVPN’s 2001 default cipher was Blowfish, before it converted to AES.
- Password hashing: The bcrypt algorithm, widely used for password hashing, is based on Blowfish’s cipher core and uses its key expansion mechanism to perform its operations.
- Embedded systems and legacy systems: Because of its variable key size and efficient computing, Blowfish is still used in many legacy systems that struggle with AES or larger block-size algorithms. Additionally, embedded systems with specific use cases incorporate Blowfish, since it fits within a few kilobytes of RAM.
Is Blowfish still relevant today?
Blowfish is relevant in specific cases, but it’s generally considered to be outdated and isn’t widely used in newer systems. Its 64‑bit block size limits how much data can be safely encrypted under one key before it exposes patterns in the cipher.
Modern standards such as AES use 128‑bit blocks and are better suited for use on modern hardware. Even Bruce Schneier, the creator of Blowfish, recommends using his newer Twofish algorithm instead of Blowfish.
That said, Blowfish is still broadly used in legacy software and is used in bcrypt for password hashing. Its simplicity and variable key size make it a viable and mostly secure option for older machines.
Advantages and disadvantages of Blowfish encryption
Strengths and benefits
Blowfish was designed for efficiency. Once the key schedule is complete, it encrypts data quickly using simple math and table lookups. This makes it useful for older 32‑bit processors and embedded systems.
Its variable key length lets each user find a balance between speed and effectiveness. If you’re using a legacy system, you can use a smaller key that requires less intensive computing. Conversely, modern systems can use larger key sizes. Blowfish has a 448 key-size limit, which is impressive even by modern standards. For example, 256-bit AES only uses a 256-bit key.
Despite some vulnerabilities, Blowfish is mostly secure. The cipher has been subjected to extensive cryptanalysis, and full‑round Blowfish has never been cracked.
Weaknesses and limitations
Blowfish’s biggest weakness is its outdated 64-bit block size. When large volumes of data (more than roughly 32GB) are encrypted under the same key, birthday attacks become feasible. These attacks come from the basic logic that in a large enough set, two people will eventually share the same birthday.
When applied to data, this principle essentially means that if you can find even one repeated ciphertext block, that pattern will repeat again somewhere else. Birthday attacks are collision-seeking predictive attacks, rather than purely brute force attacks.
Regarding cracking the encryption itself, Blowfish’s variable key length makes it hard to label as fundamentally vulnerable. If you’re using a shorter key length, it’s more vulnerable to brute force attacks, but there are no known successful brute force attacks against the full algorithm.
Finally, because Blowfish was optimized for 32‑bit CPUs and predates modern standards, it lacks hardware acceleration and isn’t built into modern hardware.
Is Blowfish encryption safe to use today?
Blowfish is a safe enough choice for legacy machines and for smaller quantities of data. The full 16‑round cipher has survived decades without being cracked. However, its 64‑bit block size and slow key setup mean that modern algorithms like AES are almost always a better option.
Blowfish vs. AES: Which is better?
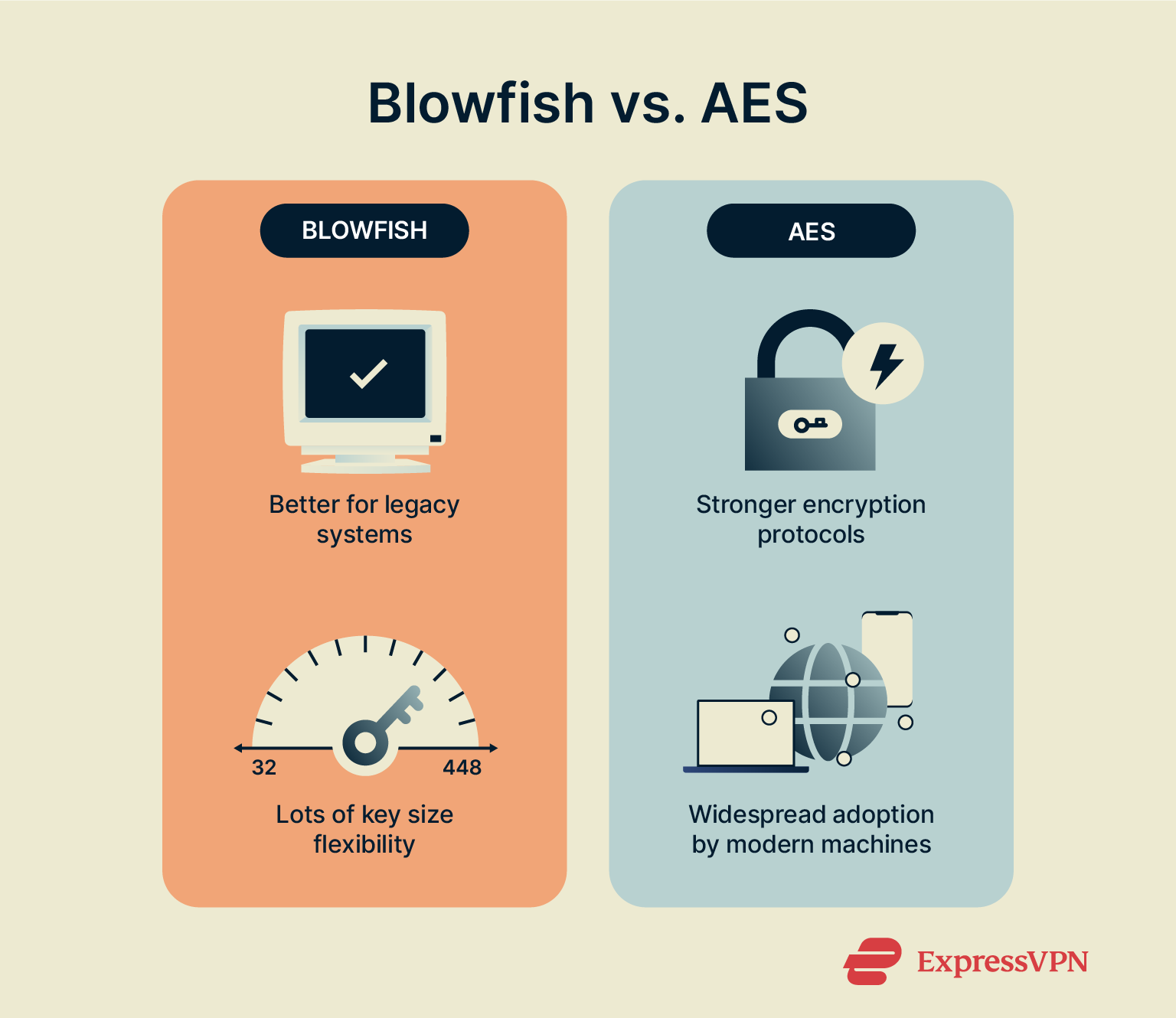
AES encryption is better than Blowfish in the vast majority of circumstances. AES’s 128‑bit block size means it’s more resistant to attacks against large data sets.
What’s more, AES is the current industry standard and offers better performance in most modern environments. Blowfish, though flexible, operates on 64‑bit blocks and lacks broad hardware support.
That said, Blowfish still has a valid use case on legacy 32-bit systems, where its variable key size makes it more compact and easier to run.
Is 256-bit AES better than Blowfish?
 For the most part, AES encryption is better and more future-proof than Blowfish. 256-bit AES encrypts data in 128‑bit blocks using a 256‑bit key and 14 rounds of data scrambling. The larger block size offers more resistance against brute force attacks.
For the most part, AES encryption is better and more future-proof than Blowfish. 256-bit AES encrypts data in 128‑bit blocks using a 256‑bit key and 14 rounds of data scrambling. The larger block size offers more resistance against brute force attacks.
Plus, 256-bit AES is approved by the National Institute of Standards and Technology (NIST), is widely implemented, and uses hardware acceleration on most modern CPUs. This makes it both more secure and faster in modern environments.
Blowfish, in contrast, uses 64‑bit blocks and 16 Feistel rounds and allows keys up to 448 bits. While a long Blowfish key provides strong brute‑force resistance, its small block size and slower key schedule make it less secure overall. Unless you’re using a legacy system, AES is a better option for nearly every application.
Why Blowfish is rarely used in modern encryption tools
Blowfish isn’t used in many modern encryption tools because it has vulnerabilities that have since been addressed by modern competitors. Blowfish’s 64‑bit block size cannot safely encrypt files of roughly 32GB or above due to the risk of block collisions that can compromise your data.
Conversely, modern algorithms like AES and 3DES offer larger block sizes, stronger security proofs, and hardware acceleration, all of which make them far more practical for modern machines.
Blowfish still serves a niche role in password hashing and legacy system encryption, but otherwise, modern encryption services are simply more effective.
Can Blowfish encryption be cracked?
 No practical attack has broken the full 16‑round Blowfish cipher. Differential and linear cryptanalysis have only succeeded in cracking ciphers that aren’t using the full 16 rounds.
No practical attack has broken the full 16‑round Blowfish cipher. Differential and linear cryptanalysis have only succeeded in cracking ciphers that aren’t using the full 16 rounds.
Because keys can be up to 448 bits long, brute‑force attacks are nearly impossible (when using a long, strong key). The main weakness is the 64‑bit block size; encrypting large amounts of data under one key can lead to collisions and information leaks.
While Blowfish has never been cracked, it has limitations that prevent it from competing with modern encryption algorithms.
Known vulnerabilities
Researchers have identified weak keys and proved that attacks on reduced‑round versions of Blowfish can succeed. It was discovered that a class of keys could be detected but not broken in variants with 14 rounds or fewer.
The small 64‑bit block also allows birthday attacks if large quantities of data are encrypted under a single key. Additionally, Blowfish lacks any built-in integrity checks, which makes it more prone to data tampering.
FAQ: Common questions about Blowfish
What is Blowfish encryption used for?
Blowfish is used to encrypt and decrypt data in legacy systems and specialized software. It’s also the basis of bcrypt for password hashing. Because it’s highly efficient and freely available, it’s still used in embedded devices and older platforms that can’t easily adopt newer ciphers.
Can Blowfish encryption be cracked?
The full Blowfish algorithm has never been cracked, but it does have vulnerabilities. Reduced-round or lower-bit Blowfish versions can be vulnerable to attack, even if brute-force attacks are unrealistic against higher-bit versions.
Its main vulnerability lies within the 64‑bit block size, which can expose patterns when encrypting large amounts of data under the same key.
Is Blowfish better than AES-256?
No, 256-bit Advanced Encryption Standard (AES) is stronger and performs better on modern hardware, making it industry standard. Because it’s harder to break, it’s used in high-quality VPNs like ExpressVPN. Blowfish still has a place in legacy systems, but its 64-bit block size isn’t as secure as 256-bit AES.
Is Blowfish safe for securing personal data?
Blowfish can protect personal data when used correctly and on a limited scale. It’s still safe for encrypting small files, passwords, or basic data, but Advanced Encryption Standard (AES) encryption provides larger block sizes and broader hardware support.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN