What is clickjacking and how to prevent it

You click “Continue” on what looks like the next step of a signup form. Nothing seems to happen, at least not until you notice a small charge tied to one of your accounts.
That’s clickjacking in action: a hidden or overlaid interface tricks you into performing an unwanted action that may put your data or finances at risk. It’s often hard to spot, but it’s preventable if you understand how it works. This guide explains what clickjacking is, common and emerging techniques, and which security measures help safeguard against it.
Note: Attempting to perform clickjacking or any form of unauthorized manipulation of websites, user interfaces, or online accounts is illegal and unethical. This article is provided solely for educational and defensive purposes.
Understanding clickjacking
What is clickjacking?
Clickjacking, also called a UI redressing attack, is a type of attack that tricks victims into clicking hidden or misplaced elements on a page. The user believes they’re interacting with a site’s normal interface, like a “Play” or “Sign up” button. However, in reality, their clicks are redirected to a hidden layer controlled by a malicious actor.
This can trigger unintended actions that can do real harm. For example, it might authorize payments, change account settings, or grant access to a camera or microphone without the user’s knowledge.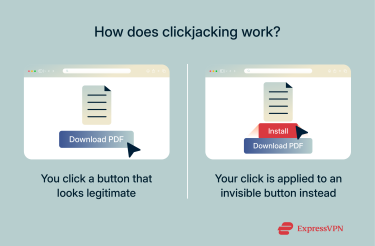
How clickjacking works
Clickjacking exploits the way browsers process user input, causing your clicks or keystrokes to be delivered somewhere other than where you expect. An attacker can place invisible or disguised elements over what you see, or subtly alter how a page behaves so that when you click or type, your input is routed to something entirely different, such as a hidden button, a fake form, or a malicious script.
In each case, it’s your browser, not the attacker’s server, that executes the action. The site sees this data and recognizes the request as coming directly from a legitimate user: it has no way of knowing that the action wasn’t deliberate.
This means that the attacker doesn’t have to steal your credentials or break into your account directly; instead, they rely on you to do it for them.
Why clickjacking is still a serious threat
Clickjacking remains a real risk for websites that don’t use the right protective measures. While some attackers use it for low-level abuse, like inflating clicks on posts, ads, or engagement counters, others aim for more harmful outcomes. On sites without proper defenses, clickjacking can be used for spreading scams, tricking users into granting permissions, or making purchases or transfers.
Types of clickjacking attacks
Clickjacking attacks differ mainly in how the deception is created. Some rely on hidden or overlapping elements that cover real content, while others manipulate the page itself just before or during interaction. Broadly, they fall into two categories: overlay-based and non-overlay-based clickjacking.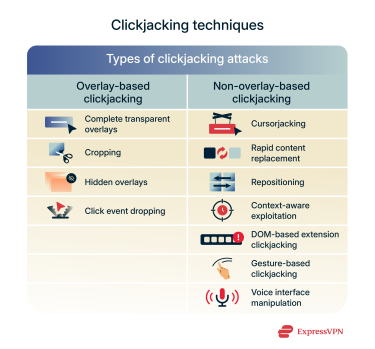
Overlay-based clickjacking
In overlay-based attacks, an attacker makes changes to a page to make it appear as though you’re clicking on something innocuous, like a “Sign Up” button, but you’re actually clicking on a malicious element.
Common techniques used
Security researchers have observed that overlay-based attacks typically rely on one or more of the following visual manipulation methods:
- Complete transparent overlays: Attackers place a malicious element over the real UI. The victim believes they are clicking the visible page, but their actions are actually performed on the layer above it.
- Cropping: Cybercriminals manipulate what part of a legitimate UI the victim can see and interact with.
- Hidden overlays: Attackers may create a minuscule element containing malicious content and hide it. Victims often can’t see the element, so they’re very likely to click it.
- Click event dropping: Malicious actors make the legitimate page appear unresponsive, so users think their clicks do nothing. But, in reality, their clicks are actually registered on a malicious page layered underneath.
Real-world examples
Past security research has documented several cases where popular platforms were found to be vulnerable to overlay-based clickjacking before updates or patches were released. Here are some examples:
- Adobe Flash vulnerability: Attackers could have created malicious Flash games that would have allowed them to access a user’s camera and microphone.
- PayPal clickjacking threat: A security researcher discovered a PayPal vulnerability that would have made it possible for cybercriminals to steal user funds.
- Facebook clickjacking attacks: Scammers used malicious links to trick victims into unknowingly recommending a website on Facebook.
Non-overlay-based clickjacking
In non-overlay-based attacks, the attacker modifies the page’s content or behavior, allowing a normal-looking interaction to perform a different action.
Because these changes happen within the same page, the browser is interacting with what it believes to be the legitimate site. When you click or type, the page forwards your input to an attacker.
Cursorjacking, rapid content replacement, and repositioning
Cursorjacking is a technique that alters the cursor’s appearance and positioning. This leads victims to believe they are performing an intended action while the browser registers the click elsewhere.
Security researchers have also documented other, related interface manipulations. For instance, rapid content replacement involves a quick swap or overlay of a malicious UI element. Similarly, repositioning attacks move a hidden clickable element just before the click occurs.
Emerging attack vectors
As interfaces evolve, attackers are adapting clickjacking techniques to new input methods beyond traditional clicks. These trends are largely speculative but help highlight where future risks might emerge. Current examples include:
- Context-aware exploitation: Attackers may adjust deceptive UI elements based on details they can infer from the user.
- Document Object Model (DOM)-based extension clickjacking: Cybercriminals could manipulate the DOM to interfere with UIs so users unknowingly trigger extension actions.
- Gesture-based clickjacking: Attackers might try to trick users into performing gestures in an augmented or virtual reality environment.
- Voice interface manipulation: Cybercriminals could make voice assistants perform unintended actions, such as initiating purchases or revealing account information.
How to prevent clickjacking
Protecting against clickjacking attacks is a combined effort. Website owners must implement strong security controls that prevent their pages from being framed or misused by attackers. Also, internet users should stay alert to suspicious links and social-engineering tricks, and rely on trusted security tools to reduce exposure to deceptive clicks.
Server-side protection
Web developers and IT security teams can take certain security precautions to protect their pages and resources, as well as website visitors, from clickjacking attacks.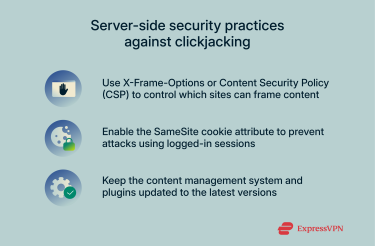
The following section outlines some of the most common defensive measures used in the industry.
X-Frame-Options header
X-Frame-Options allows developers to control whether or not browsers can render a page inside an iframe. Websites generally use this method to protect against clickjacking, as it prevents their content from being embedded into other sites. This method is only effective if visitors use a browser that supports X-Frame-Options, though most modern browsers do.
The X-Frame-Options header offers the following directives:
- DENY: Prevents the page from being displayed in an iframe, no matter which site attempts to do this.
- SAMEORIGIN: Allows just the current website to embed the content in an iframe.
- ALLOW-FROM origin: Specifies a single page that can frame the content. However, this command is obsolete and modern browsers ignore it.
X-Frame-Options isn’t widely used today and has been replaced by the Content Security Policy (CSP), which provides more granular control.
Content security policy (CSP)
The CSP is a feature supported by most modern browsers that helps minimize the risk of certain security threats, including clickjacking. Developers enforce this using the frame-ancestors directive to specify which origins are allowed to embed a page inside frames or similar UI elements. In this context, “origin” refers to the exact combination of protocol, domain, and port of the URL that embeds the content.
For example, you can use Content-Security-Policy: frame-ancestors 'none'; to prevent any site from framing content. Alternatively, Content-Security-Policy: frame-ancestors 'self'; only allows the same site to embed content, while Content-Security-Policy: frame-ancestors 'self' https://partner.example.com; permits embedding by the current site and one trusted partner.
SameSite cookie attribute
The SameSite cookie attribute primarily helps protect against cross-site request forgery (CSRF) attacks, which can force users to perform unwanted actions in web apps they’re logged into. It can also defend against certain clickjacking strategies that rely on users already being authenticated.
Cookies with the SameSite attribute set to strict or lax aren’t sent when a page is loaded inside an iframe from another site. This means a clickjacking attack that depends on a logged-in session is far less likely to succeed.
System updates
Websites should always update to the latest version of the framework (WordPress, Shopify, WooCommerce) and plugins they’re using. New releases often include security patches that fix vulnerabilities attackers can exploit, reducing the effectiveness of their clickjacking attacks.
Client-side protection
As a regular internet user, you can take several measures to limit your exposure to clickjacking, such as learning to recognize phishing attempts and using an antivirus.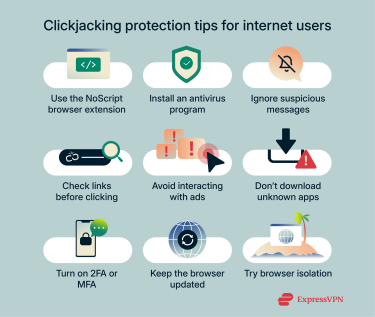
The following section covers these tips more in-depth.
Secure browser extensions
There aren’t many browser extensions that specifically protect against clickjacking attacks. That said, NoScript blocks potentially harmful scripts and plugins, safeguarding against many online threats, including clickjacking attacks. The extension is available for Firefox, Chrome, and other Mozilla or Chromium-based browsers.
Best practices for end users
Implement as many of the following cybersecurity tips as you can to avoid clickjacking attacks or make them less effective:
- Use antivirus software: Antivirus programs help protect your device against malware infections. Many of them can also flag and block malicious links that might redirect you to clickjacking pages.
- Ignore suspicious messages: Clickjacking attacks often start with phishing emails and messages. Ignore and block unknown senders and messages that instill a sense of urgency and try to pressure you into making rash decisions.
- Check if links are safe: Attackers can manipulate links, making them seem legitimate while they actually redirect to pages with clickjacking elements. Avoid shortened URLs and hover over links to see the real destination.
- Don’t click ads: Some advertisements may be malicious, especially those that sound too good to be true, and interacting with them can trigger unwanted actions.
- Don’t download suspicious apps: Cybercriminals sometimes lure users into downloading fake apps that contain malware. These scams may also mislead you into clicking buttons or granting permissions you didn’t expect, so only download apps from official sources.
- Enable two-factor authentication (2FA) or multi-factor authentication (MFA): 2FA and MFA make the login process more secure by requiring extra verification after entering the password.
- Update your browser: New releases often include security patches that help defend against clickjacking, embedded threats, and other web-based vulnerabilities.
- Try browser isolation: This advanced approach separates your browsing session from the rest of your device. It runs websites in a contained environment, so malicious pages or hidden actions triggered by clickjacking can’t directly impact your system.
Read more: To learn how to avoid clickjacking and other threats, we recommend reading our safe browsing guide.
Can a VPN protect against clickjacking?
While virtual private networks (VPNs) are good security tools, they can’t protect against clickjacking attacks because they don’t control what happens inside your browser once a web page loads.
However, some VPNs bundle privacy tools that warn you when you try to visit known malicious sites, which can help you avoid pages that might use clickjacking techniques. ExpressVPN does this through its Threat Manager feature, which is available on most of its apps, including Windows, macOS, Android, iOS, and Linux.
Limitations of VPNs in preventing UI-based attacks
A VPN works at the network level. It secures the path between your device and the sites you visit by encrypting data, so no one with access to the network, whether hackers, snoops, or even your internet service provider (ISP), can see or tamper with your activity.
But once you’re on a web page, your browser handles all interaction locally. If a page contains malicious overlays or scripts, the VPN doesn’t see or filter them. If you click on a disguised button or form field, the VPN can’t prevent that action; your browser will still carry it out.
How VPNs improve general online privacy
While VPNs can’t directly prevent clickjacking, they’re still essential tools for safeguarding your digital privacy. A VPN protects sensitive information, such as location data and web browsing.
For example, let’s say you click a suspicious link while connected to a VPN, and it redirects you to an attacker-controlled page that uses clickjacking. The VPN stops the cybercriminal from seeing your IP address and secures your connection to the site.
By encrypting your traffic, VPNs also help protect against man-in-the-middle (MITM) attacks, which try to intercept and alter your connections. Cybercriminals may target you with such attacks on unsecured public networks to redirect your traffic to a phishing page that uses clickjacking techniques.
Why VPNs should be combined with browser security measures
Using a VPN alongside other security measures that protect against clickjacking offers a high level of digital security and privacy. You limit your exposure to UI-based attacks while also making it harder for malicious actors or other third parties to monitor your web browsing and location data. ExpressVPN helps keep you safe online through industry-standard encryption, an independently audited no-logs policy, and built-in ad-blocking tools.
FAQ: Common questions about clickjacking
What is a clickjacking attack?
Clickjacking is a cyberattack that tricks users into interacting with hidden, malicious UI elements. For example, the victim might think they’re clicking a normal signup or download button, but their click actually triggers a different action, such as liking a post, confirming a purchase, or navigating to a phishing page that requests sensitive information.
How can clickjacking be prevented?
Clickjacking attacks can be prevented by implementing tight security practices. Developers should enforce server-side protection, usually through the Content Security Policy (CSP) feature and the SameSite cookie attribute, and by using the latest framework and plugin versions. Website visitors, on the other hand, can use the NoScript extension to block potentially harmful scripts, install an antivirus, and avoid interacting with suspicious messages, links, and ads.
Is clickjacking the same as phishing?
No, but the terms are related. Clickjacking is a cyberattack that tricks users into clicking harmful UI elements, while phishing is a type of scam where attackers trick victims into interacting with malicious links, downloading malware, or sharing sensitive information. Malicious actors often combine clickjacking with phishing to make them more effective.
How do I know if I’ve been clickjacked?
Clickjacking is often hard to detect because the page appears to work normally. A possible sign is when buttons or links trigger the wrong action. You may have been exposed if you notice unexpected account activity shortly after clicking something, such as unfamiliar posts or unauthorized small purchases.
Are certain browsers more vulnerable to clickjacking?
The biggest risk comes from using an outdated browser, since older versions may not support modern security protections against clickjacking. For example, they may ignore Content Security Policy (CSP) settings that prevent a page from being loaded in a hidden frame. Keeping your browser updated makes these protections more effective.
Can clickjacking impact mobile devices?
Web-based clickjacking is rare on mobile, but possible. App-based attacks can target mobile users, especially on Android. Malicious apps can display invisible overlays or fake screens, tricking you into granting permissions or tapping items you didn’t intend. To prevent this, only install apps from trusted sources, review app permissions, and use an antivirus.
How often should I update my browser settings?
You should always use the latest version, as it could include important security updates and protections against clickjacking. In addition, you should also use an antivirus, ignore suspicious messages, links, ads, and apps, and enable two-factor or multi-factor authentication to better protect your accounts.
What’s the difference between clickjacking and cross-site request forgery (CSRF)?
Both attacks try to make a user perform unintended actions, but they work differently. Clickjacking uses hidden UI elements to mislead victims into clicking malicious buttons or links. CSRF doesn’t rely on visible tricks, but instead causes browsers to send requests on the user’s behalf, often because the user is already logged into the web app being targeted.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN