Fast flux networks: Complete guide to risks and detection

Fast flux is a Domain Name System (DNS)-based evasion technique that rapidly rotates the IP addresses associated with a malicious domain so that it doesn’t remain at a single host. Attackers achieve this by using networks of compromised machines as temporary hosts or proxies.
The tactic hides the true origin of phishing pages, malware distribution sites, and botnet command‑and‑control infrastructure, which makes takedowns and IP-based blocking much more difficult.
In this guide, we’ll look at what fast flux actually is, how these networks are set up, the risks they pose, and the steps you can take to recognize and defend against them.
What is fast flux?
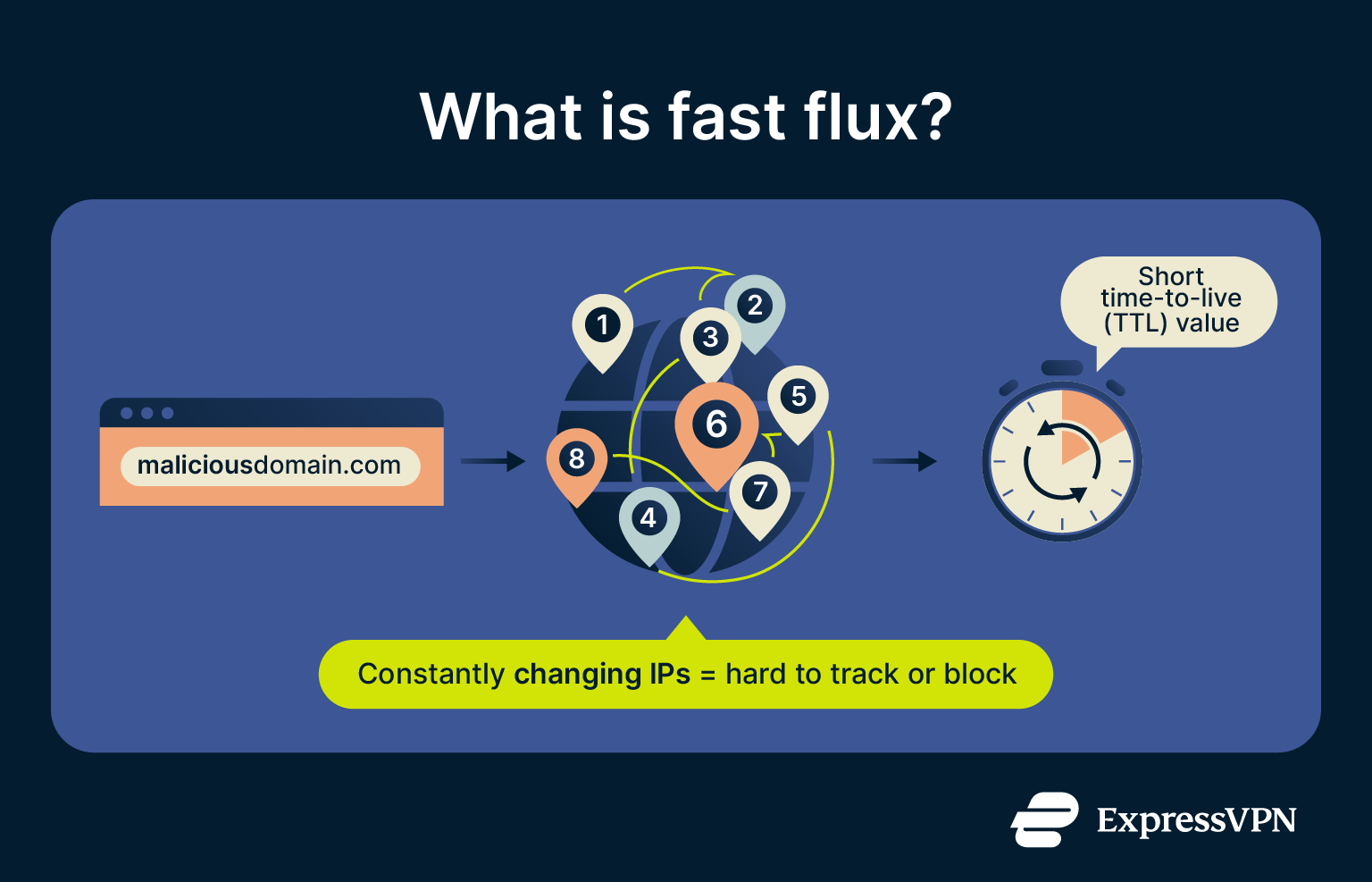
Fast flux is a way of using DNS to disguise malicious domains behind a constantly shifting set of IP addresses. To do this, attackers use a botnet of compromised machines that act as proxies, keeping the underlying servers hidden.
The domain name itself stays consistent, but every lookup may return a different compromised host. This constant rotation makes phishing sites, malware, and other attacks much harder to track or block.
Fast flux uses very short time to live (TTL) values. TTL is the amount of time a DNS record is considered valid before the system has to look it up again. Short TTLs force systems to refresh DNS lookups frequently, often every few minutes, ensuring that each query can return a different result. This constant turnover is what defines fast flux behavior.
Significance of fast flux in cybersecurity
Fast flux bypasses many of the usual cybersecurity defenses. Tools that rely on static IP blocklists lose their effectiveness when a domain keeps shifting to new addresses every few minutes or even seconds. A static IP blocklist blocks connections to known malicious IP addresses, but it can’t keep up when those addresses change constantly.
The constant churn also spreads activity across many servers, which disrupts tools that look for concentrated or repeated patterns in network traffic. This resilience is what makes fast flux valuable for the attackers behind phishing sites, malware, or botnets.
The effectiveness of fast flux has been recognized at the highest levels. In 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that fast flux poses a national security threat.
Key characteristics of fast flux networks
Fast flux network types
There are two main types of fast flux network:
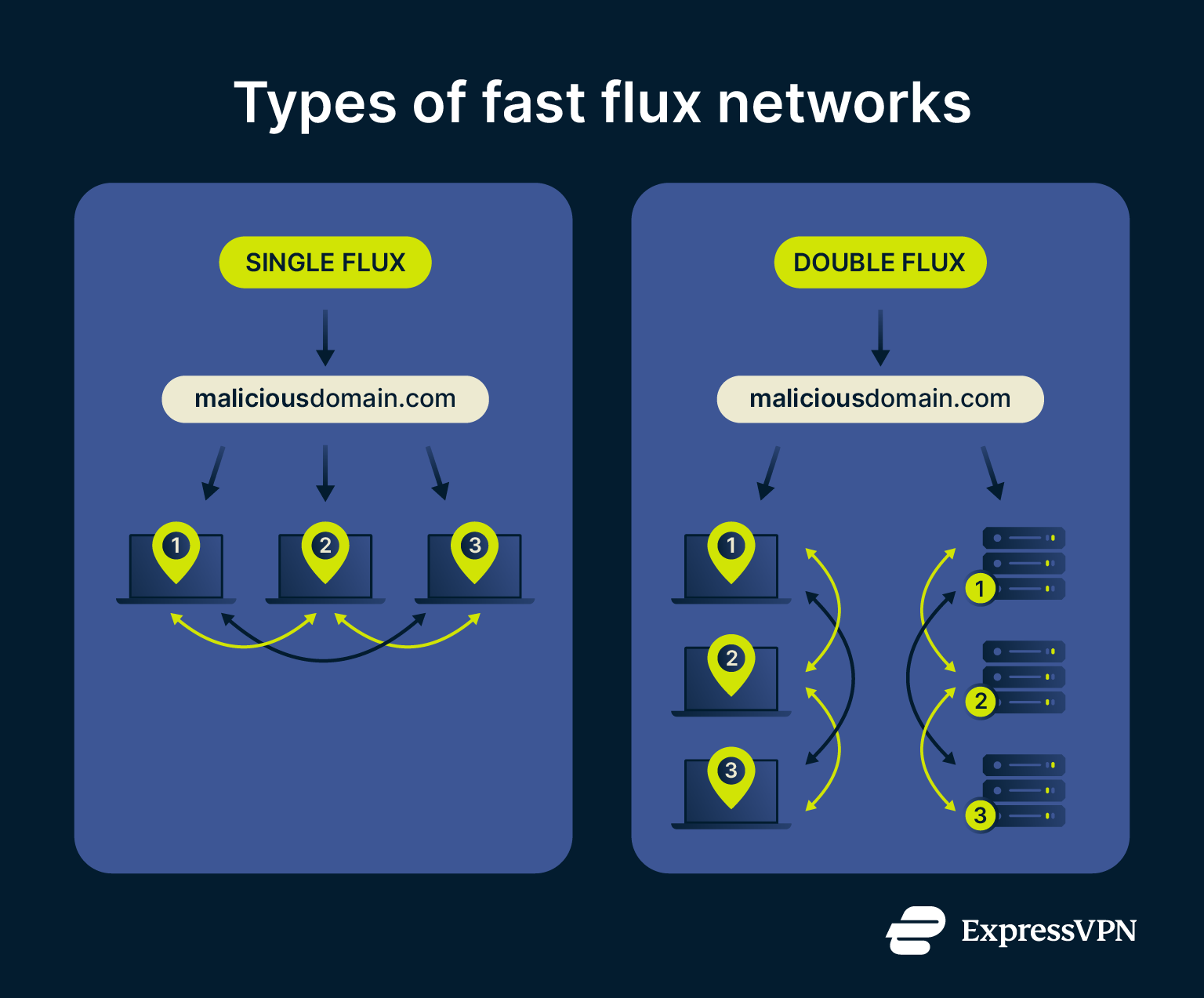
Single-flux networks
In a single-flux setup, one domain is tied to many IP addresses that are rotated in DNS responses, so the address changes regularly even as the domain name stays the same.
Double-flux networks
Double-flux networks go further by also rotating the name servers (the authoritative DNS servers for the domain). Rotating name servers adds a second layer of movement and resilience, because both the IP addresses and the DNS infrastructure that resolves the domain are dynamic.
How fast flux differs from traditional DNS
In a typical DNS setup, a domain name is linked to one or a few IP addresses that remain fairly stable, even when short TTL values are used to refresh records.
With fast flux, the pattern is different: the DNS records are deliberately set with very low TTLs so they change rapidly, often every few minutes. This means the same domain can resolve to a different compromised host with each lookup. The rapid turnover across a large pool of IPs creates a distinct operational footprint compared to normal DNS behavior.
Fast flux techniques and tools
Attackers build fast flux networks from large pools of compromised machines. These act as temporary hosts or proxies, masking the true servers and making tracing or blocking more difficult.
Operators intentionally configure DNS records with very short lifetimes, so lookups frequently resolve to different infected hosts, and they typically automate the changes using scripts or management tools. Compromised machines in these networks often run lightweight proxy or web server components to deliver content or relay traffic.
Some criminal toolkits and service offerings (sometimes described as fast-flux service networks, or FFSNs) even let criminals rent this setup instead of building their own botnet.
Fast flux in malware distribution and phishing campaigns
Attackers use fast flux to keep phishing websites active and difficult to block. These sites often trick people into giving away sensitive information or downloading malware. The domains are often created through typosquatting (where attackers register lookalike versions of trusted sites to encourage you to visit them).
To better understand the threats posed by phishing URLs and how to recognize them before they lead to fast flux traps, check out our URL phishing guide, which breaks down how phishing URLs work and how to spot them.
Criminal groups also use fast flux networks to stage and distribute malicious software and to host forums or marketplaces where stolen data and hacking tools are traded. Compromised hosts in the network commonly run lightweight proxy or web server components.
Fast flux is tightly associated with droppers, malware programs that install other malicious payloads on an infected device, and command-and-control (C2) servers, the systems attackers use to send instructions to infected machines and coordinate malicious activity. By rotating IP addresses and servers, criminals make both droppers and C2 infrastructure harder to locate or disrupt.
Documented cases of fast flux in a recent national security advisory include:
- Hive: A ransomware group that used fast flux to make its C2 servers harder to disrupt.
- Nefilim: Another ransomware operation that applied fast flux to make its infrastructure more resilient.
- Gamaredon: A state-linked group that employed fast flux in campaigns to reduce the effectiveness of IP blocking.
Rapid changes in IP addresses: DNS round robin vs. fast flux
Round robin DNS is a standard way to distribute traffic across servers. A domain name points to several IP addresses, and each DNS query hands out a different one in turn. The set of servers is fixed and managed by the site owner, so while queries may return different IPs, they always come from the same small pool. This makes the addresses stable and predictable while also balancing the load and helping to keep services online.
Fast flux takes that idea and twists it. Instead of using a small, stable set of servers, attackers rotate through large numbers of compromised machines. They intentionally use very short DNS record lifetimes so answers expire quickly and lookups rapidly return different infected IPs, making the infrastructure far harder to trace or block.
How to detect fast flux attacks
Fast flux is designed to blend in with normal network activity, which makes detection a challenge. However, security teams can still uncover it by looking for distinctive behaviors and applying focused analysis.
Signs of fast flux activity
IT professionals can recognize fast flux by looking at patterns that don’t usually appear in legitimate DNS activity:
- Large numbers of IPs for one domain: A single domain may resolve to hundreds or even thousands of addresses in a short time, often scattered across different regions.
- Geographic and Autonomous System Number (ASN) irregularities: The returned IPs tend to belong to many unrelated networks and countries, unlike a normal content delivery network (CDN), where most IPs sit in a few data centers.
- Compromised hosts in the mix: Many of the IPs show up on malware or spam blacklists, suggesting they come from infected machines.
- Inconsistent responses: Some servers fail intermittently or deliver different content, reflecting the instability of hijacked infrastructure.
- Unusual query spikes: Because of the very short TTLs, DNS resolvers end up sending far more lookups for these domains than they would for ordinary ones.
Detecting fast flux using tools and DNS analysis
Security teams can detect fast flux by combining DNS analysis with dedicated tools. Reviewing DNS logs is one of the most direct methods, as fast flux domains often return unusually low TTL values and cycle through a large number of IP addresses over time. The following tools can also be useful:
- Threat intelligence services: Help to flag domains or IPs already linked to malicious activity
- DNS filtering: Can stop lookups before users reach dangerous sites
- Examining network flow data: Reveals abnormal traffic spikes
Used together, these methods help teams to clearly distinguish fast flux from legitimate activity.
Using machine learning to detect fast flux activity
Machine learning helps to spot fast flux networks by looking at patterns in DNS traffic and how they change over time. It goes beyond simple rule-based checks, picking up subtle signals that more traditional methods may miss.
These systems can quickly and automatically determine factors such as how spread out the IPs are across countries, how many different autonomous systems they belong to, and whether the servers respond consistently. All of this data goes into classifiers that can differentiate normal services from suspicious activity to a high degree of accuracy.
Clustering and anomaly detection also play a role, highlighting domains that behave very differently from the rest. And because the models run on real-time feeds, they can adapt quickly when attackers tweak their tactics.
Prevention strategies for fast flux attacks
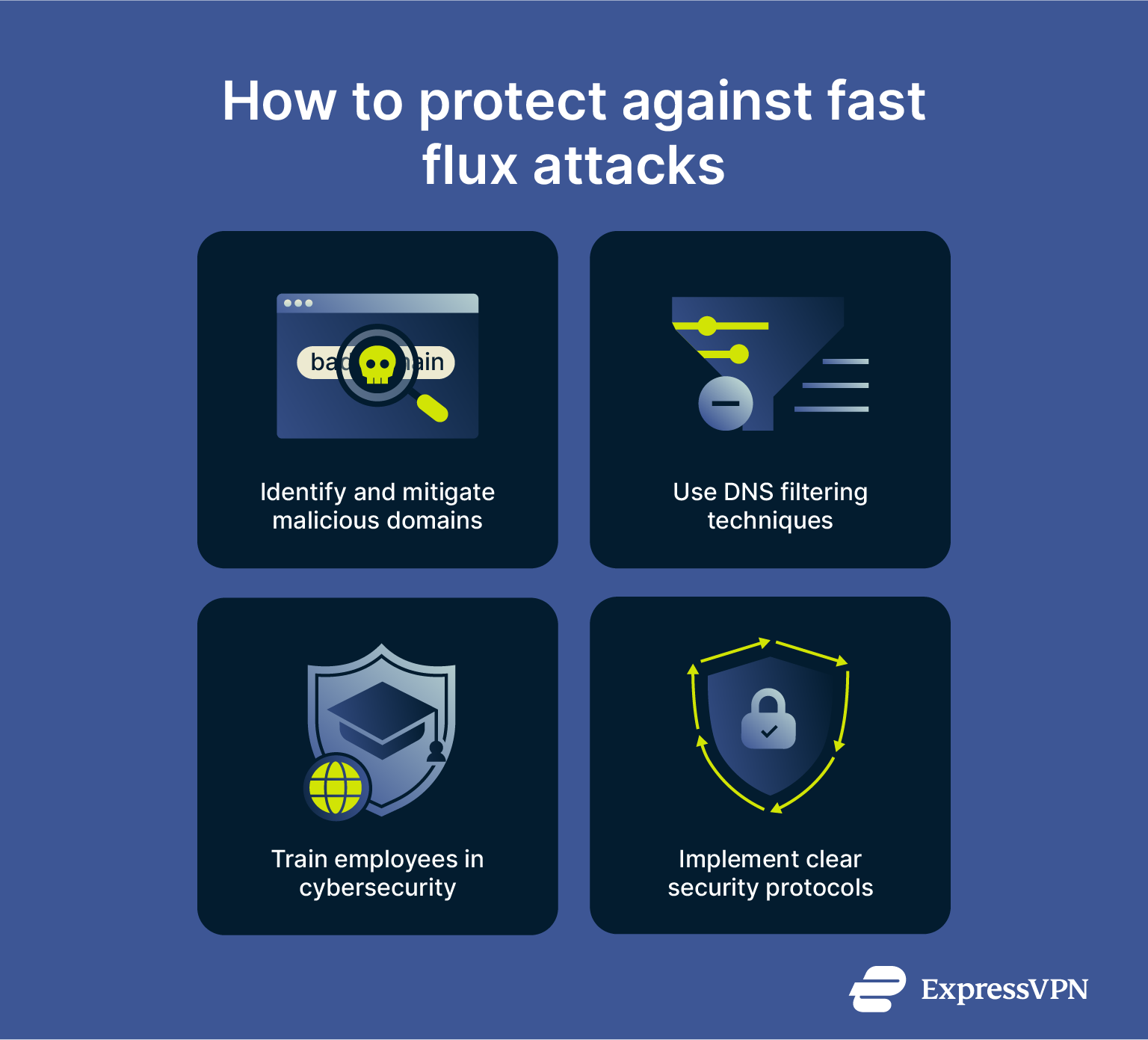 Fast flux networks are difficult to disrupt because they constantly change their infrastructure. Still, organizations can reduce their risk by using layered defenses. Blocking malicious domains, applying DNS filtering, and using sinkholes (controlled servers that redirect malicious traffic for safe analysis) all help limit the impact of fast flux when used alongside internal security measures.
Fast flux networks are difficult to disrupt because they constantly change their infrastructure. Still, organizations can reduce their risk by using layered defenses. Blocking malicious domains, applying DNS filtering, and using sinkholes (controlled servers that redirect malicious traffic for safe analysis) all help limit the impact of fast flux when used alongside internal security measures.
Identifying and mitigating malicious domains
Cybersecurity professionals can limit fast flux activity by identifying the domains involved and applying targeted controls. Security teams may block these domains at DNS resolvers or firewalls or redirect traffic to sinkhole servers for analysis.
While blocking a domain can disrupt access to the malicious infrastructure, the underlying botnet may still operate. Ongoing monitoring and coordination with registrars or law enforcement are often needed to address the threat more effectively.
DNS filtering techniques
DNS filtering adds another layer of defense against fast flux networks. These tools block or redirect suspicious queries and highlight the behaviors that mark fast flux activity. They can:
- Block malicious lookups: Protective DNS services stop queries to domains known for fast flux, cutting connections before users reach them.
- Use reputation filtering: Filters deny traffic to and from IPs or domains with poor reputations, limiting access to malicious infrastructure.
- Spot unusual DNS behavior: Some filtering systems check for short TTL values and frequent IP changes, both common in fast flux activity.
- Enhance overall protection: Complements blocklists and internal controls for more effective mitigation.
Organizational measures against fast flux
Technical defenses are essential, but organizations also need to implement effective internal measures to handle fast flux threats. Training employees to recognize phishing attempts and enforcing clear security protocols make it harder for attackers to succeed.
Cybersecurity training for employees
Fast flux often shows up in phishing campaigns, so employee awareness makes a real difference. When people know how to spot and react to suspicious messages or fraudulent sites, the chances of an attack succeeding drop sharply. For extra support, you can refer to our phishing prevention guide, which offers practical tips for building awareness.
Here’s how to upskill your team:
- Raise awareness of phishing: Employees should learn to spot suspicious emails, links, and websites, which attackers often host on fast flux domains.
- Teach safe responses: Training should show staff how to react when they suspect a phishing attempt, to reduce the risk of compromise.
- Reinforce good habits: Ensure regular exercises to keep security practices fresh, making users less likely to fall for fast flux–based attacks.
Implementing security protocols
Organizations strengthen their defenses against fast flux when they put clear protocols in place. There should be policies to guide how to manage and contain phishing incidents linked to fast flux, and enhanced monitoring and automated alerts to help detect unusual patterns early.
Sharing indicators of malicious domains or IPs with trusted partners adds another layer of protection, creating a collective defense that means it’s harder for attackers to stay hidden.
FAQ: Common questions about fast flux
What is the fast flux algorithm?
Fast flux algorithms rotate Domain Name System (DNS) records to hide malicious infrastructure. In single flux, a domain switches between many IP addresses. In double flux, attackers also rotate the name servers, adding another layer of movement and resilience.
How do you block fast flux?
Security teams block fast flux by blocking malicious domains, filtering Domain Name System (DNS) requests, and using sinkhole servers to redirect traffic for analysis. Reputation-based filtering and automated alerts also help stop connections to fast flux networks.
What is a flux network?
A flux network uses compromised machines to act as proxies for a malicious domain. The domain name stays the same, but the IP addresses and sometimes the name servers change constantly, keeping the infrastructure hidden.
How to detect fast flux attacks?
Fast flux activity shows in Domain Name System (DNS) patterns like low time to live (TTL) values, frequent IP address changes, and inconsistent geolocation. Detection tools and machine learning models analyze these behaviors to flag suspicious domains.
What are the effects of fast flux on cybersecurity?
Fast flux increases the resilience of malicious infrastructure. It lets attackers hide command-and-control (C2) servers, phishing sites, and malware delivery systems behind constantly changing IP addresses. This makes tracking and blocking attacks harder, creating a defensive gap that threat actors can exploit for longer periods.
Can fast flux networks be shut down effectively?
Fast flux networks are difficult to dismantle because their IP addresses and even name servers change constantly. This makes IP-based blocking ineffective. The most effective step is to target the domain itself through coordinated takedowns with registrars or law enforcement, though this is complex and doesn’t eliminate the underlying botnet. Effective mitigation usually combines domain takedowns with Domain Name System (DNS) filtering, monitoring, and user awareness.
How does fast flux compare to traditional phishing techniques?
Traditional phishing campaigns often rely on static servers that cybersecurity tools can identify and block quickly. Fast flux extends the lifetime of phishing sites by rotating IP addresses and sometimes name servers, making takedown attempts less effective. This technique allows phishing pages to stay online longer, giving attackers more time to steal credentials and spread malware.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN