How to protect your email: Step-by-step guide

Your email account is an important point of access to the rest of your online life. Many services use it as the primary recovery channel, so whoever controls your inbox can request password resets, intercept verification codes, and gain entry to accounts you thought were unrelated.
A compromised inbox can also expose years of conversations and sensitive files. It may even allow an attacker to impersonate you, tricking your contacts or colleagues into sharing information or sending money.
This guide explains why email security matters, how to apply effective protections, and what steps to take if your account is breached.
Why email security matters in 2025
Email is a prime target for attackers because it often links to banking, shopping, cloud storage, and workplace tools. The main risks include:
- Phishing emails: Attackers send messages designed to trick you into clicking a link or opening a file. Many now use generative tools to create convincing, multilingual content, and some kits can even capture session tokens to bypass two-factor authentication (2FA).
- Stolen credentials: Cybercriminals often try usernames and passwords leaked in earlier breaches directly against email providers. If you’re using a password that has previously been exposed, they can break in without sending a single phishing message.
- Malware and Wi-Fi threats: Malicious software can steal saved cookies or session tokens from your browser, which lets intruders skip the login step entirely. Others install keyloggers that record everything you type, including your login details. On unsecured Wi-Fi, man-in-the-middle (MITM) attacks can redirect or intercept your traffic before encryption is applied.
For businesses, email compromise remains one of the most expensive attack types. Well-crafted invoices or executive impersonation have tricked staff into wiring large sums or releasing confidential documents.
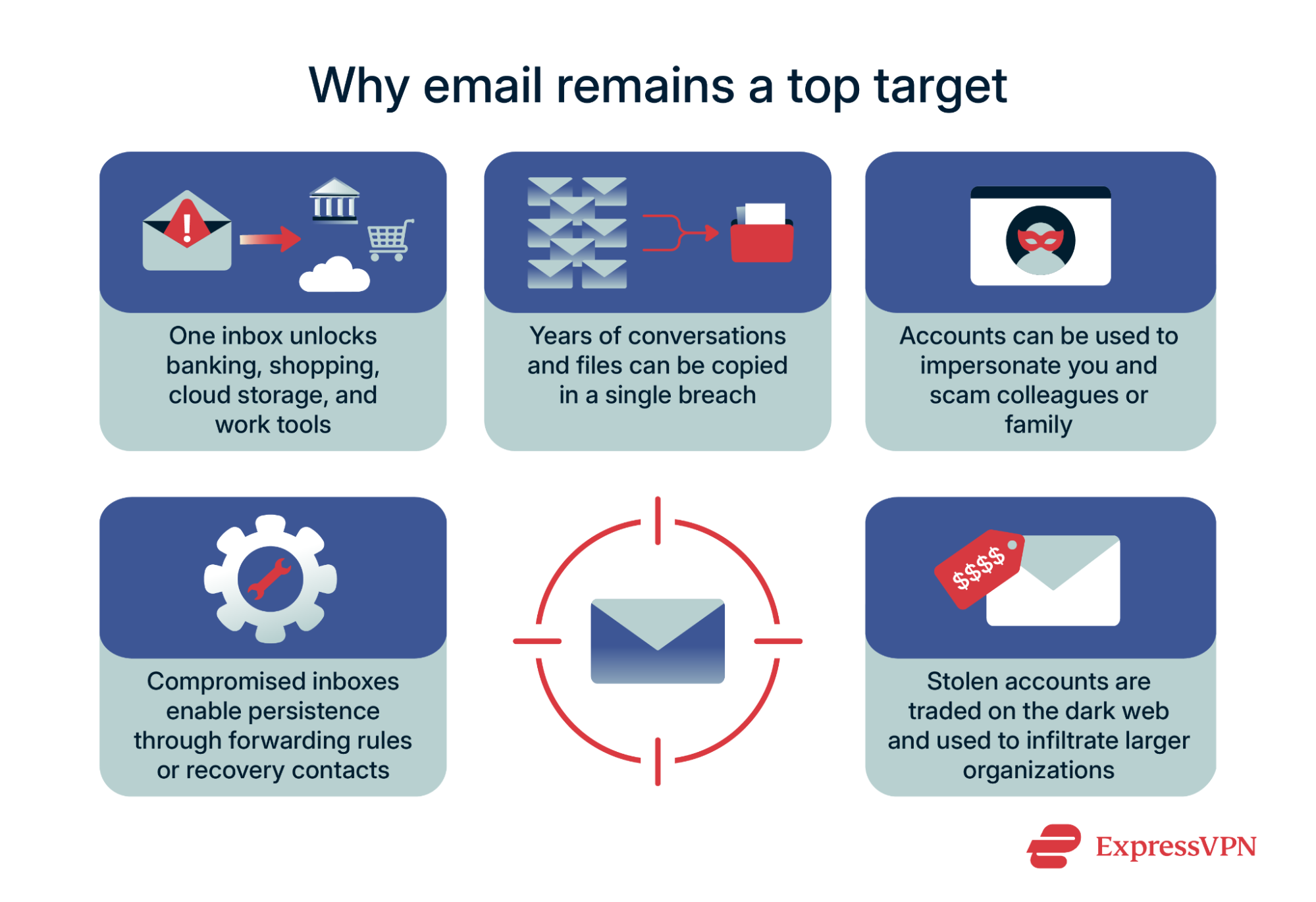
Once inside, attackers usually try to stay. They may reset passwords for linked services, copy years of archived mail, or pose as the account owner to deceive colleagues and family. Many create forwarding rules, add recovery contacts, or register app-specific passwords so access survives even after a reset.
Stolen email accounts are often sold on the dark web. Criminals use them not only to send spam but also as a starting point for deeper attacks. In companies, a single compromised inbox can open the door to shared drives, calendars, and project tools, turning one mailbox into a company-wide breach.
How to secure your email account
Here are some email security best practices to help keep your account safe.
Create a strong, unique email password
A good password should be long, unpredictable, and unique. It should have at least 14 characters and include a mix of letters, numbers, and symbols to make it harder to crack.
The simplest way to manage multiple complex passwords is to use a password manager like ExpressVPN Keys. It can generate strong passwords automatically and then store them securely in an encrypted vault.
If you prefer a password you can remember, use a passphrase. Combine four or more unrelated words and add capitals, numbers, or separators. For example: Orange-Ladder7-Ocean-Velvet. Avoid predictable choices like quotes, song lyrics, or personal details. The more random the words, the stronger the passphrase. But if it’s too random, you may forget it. Pick a structure that you can recall without making it obvious to others.
Whatever method you choose, it’s best to avoid unsafe storage. Don’t keep passwords in notes, screenshots, or email drafts, and if you use a password manager, secure it with a strong master password.
Enable two-factor authentication (2FA) for email
2FA adds a second check at sign-in. Even if your password leaks, an attacker still needs that extra factor to get in.
Most email providers let you enable this from your account or security settings. The process is usually the same: go into your security menu, choose 2FA (sometimes called 2-step verification), and follow the prompts to add your first method. Always add a backup option if the service allows it.
Many email services let you use time-based codes from an authenticator app. With ExpressVPN Keys, you can generate those codes directly inside your password manager whenever your provider supports app-based 2FA. This means you can keep your passwords and codes in one encrypted vault rather than spreading them across multiple apps.
Authenticator apps are safer than SMS because the codes are generated offline on your device and can’t be intercepted while they’re sent.
Why you should never reuse passwords across accounts
When the same password is used for multiple accounts, a compromise on any service can open the door to many others. Attackers can take stolen username and password pairs and run them through automated tools against email providers, online banking, cloud storage, and social networks. If even one match succeeds, they may be able to take over critical accounts.
Using unique passwords breaks this chain. If one account is breached, the damage stays contained instead of spreading to your inbox, your money, or your files. A password manager makes it easier by generating strong passwords, storing them securely, and flagging duplicates so you can replace them before attackers exploit them.
Recognize and avoid phishing emails
Phishing emails often rely on urgency or familiarity to get your attention. A message might warn that your account will be closed, claim a delivery failed, or promise a refund. Others pose as routine notifications or shared documents to make you click without thinking.
There are a few checks that help expose them. Read the sender’s address carefully, since attackers often swap letters, such as "rn" for "m," or slip in extra characters to mimic a brand. You should also hover over links before clicking to see where they really lead and never trust the display text alone.
Be cautious with attachments you weren’t expecting, because malicious files can arrive disguised as routine documents. Attackers also use compressed archives like ZIP or RAR files, which can hide harmful programs inside. If you didn’t request the file directly from someone you trust, don’t open it.
Phishing techniques have also evolved. Criminals may use generative tools to write convincing emails in many languages and phishing kits that steal session tokens to bypass 2FA. That’s why the best prevention is to slow down and check. If a message feels urgent, ignore the link and open the official site or app directly.
Is it safe to check your email on public Wi-Fi?
Public Wi-Fi carries risks because anyone on the same network can try to monitor your activity, inject malicious content, or set up a fake hotspot that looks legitimate.
The weak point is often the connection setup phase. Many hotspots first redirect you to a captive portal: the page where you accept terms or enter a code. Until you complete that step, traffic can be hijacked or manipulated.
Even after you’re online, a rogue access point (sometimes called an “evil twin”) can launch a MITM attack by placing itself between you and the email provider. That can allow attackers to read or alter unencrypted traffic, present fake login pages, or steal the session cookies that keep you signed in.
Modern email providers use encryption, which makes email safer than it once was, but metadata and session security can still be targeted on an unsecured network. That’s why public Wi-Fi should be treated as untrusted unless you add extra protection, such as a virtual private network (VPN).
Benefits of using a secure VPN for email access
A VPN like ExpressVPN creates an encrypted tunnel between your device and the server you connect to. That stops anyone in the middle, like your internet service provider (ISP), the owner of a Wi-Fi network, or someone running a fake hotspot, from reading or changing the data before it reaches your mail provider.
It also hides your real IP address. Instead of your location being visible every time you log in, websites and services only see the VPN server’s address. That makes it harder for advertisers or attackers to connect your activity across sessions or trace it back to you.
A VPN adds strong protection, but it doesn’t replace end-to-end encryption (E2EE) like HTTPS or Transport Layer Security (TLS). Your email provider still handles your emails, and the VPN provider becomes a trusted party in the process. That’s why choosing a reputable VPN service and relying on secure email protocols remain essential.
How to set up a secure email system
Securing your inbox isn’t just about strong passwords or 2FA. The provider and tools you choose make a big difference in determining how safe your email really is.
Choose a secure email provider
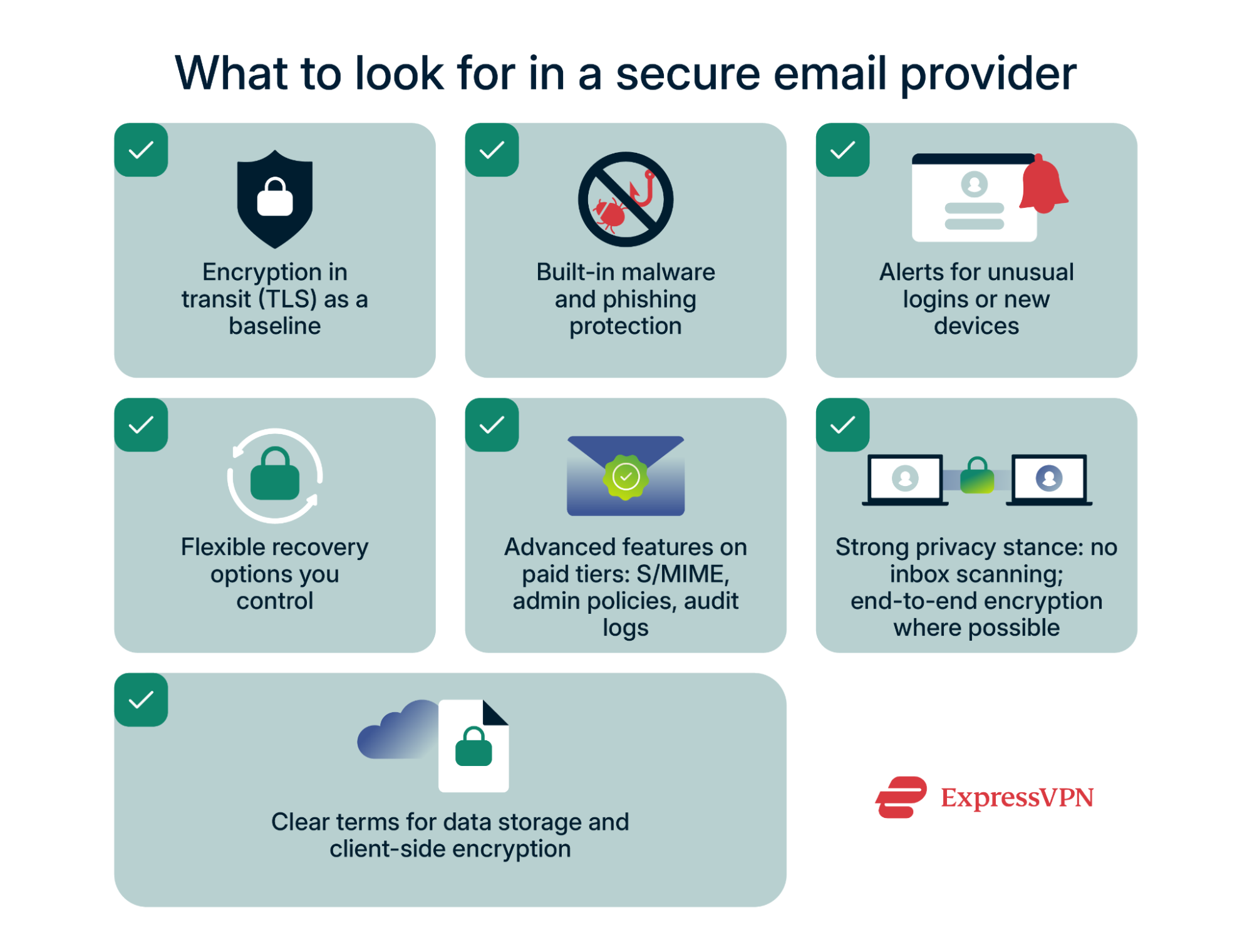 A secure email service should protect you by default. Look for a provider that:
A secure email service should protect you by default. Look for a provider that:
- Uses TLS so messages are encrypted while moving between servers. This is now standard practice with modern email providers, but it’s worth confirming.
- Scans for malicious links or attachments to block phishing and malware before they hit your inbox.
- Alerts you to suspicious logins and shows a history of devices that accessed your account.
- Gives you recovery options you can manage, such as adding, changing, or removing backup emails and phone numbers.
Business and paid accounts might add more controls. For example, some support Secure/Multipurpose Internet Mail Extensions (S/MIME), a system that lets you digitally sign messages to prove authenticity and encrypt content so only the intended recipient can read it. What’s more, some business email accounts let administrators enforce 2FA across all users, apply retention rules for compliance, or view audit logs showing account activity.
Privacy is just as important as security. Some services scan inboxes to target ads, while others commit to E2EE or limit the amount of metadata they collect. Read the provider’s privacy policy carefully to understand what they can see and what they can’t.
High-risk users should consider hardened services that restrict third-party integrations and narrow recovery options. For Gmail users, Google offers its Advanced Protection Program, which requires a passkey or physical security key for login, limits risky third-party access, and applies extra safeguards against phishing and harmful downloads.
Block remote content and tracking pixels in email
Many marketing emails include remote images known as “tracking pixels” that load from a server when you open the message. That request confirms your address is active and can reveal details such as when you opened the email, which client or device type you used, and sometimes your IP address.
The simplest defense is to block remote content by default. Most webmail services and mobile apps offer a setting to stop external images from loading automatically. You can still allow images from trusted senders, but keeping them blocked prevents most routine tracking. For a deeper look at how these pixels work, see our guide on email tracking.
Limit or disable email forwarding safely
Attackers can abuse automatic forwarding to maintain access after a breach. If enabled, this hidden rule could send every incoming message (including password resets or security codes) to another inbox without the account owner noticing. Because the victim still sees their mail normally, the rule may go undetected for months.
To protect yourself, check your account’s forwarding settings regularly and delete any you didn’t set up. Also, keep an eye on other changes that attackers might use to stay hidden, like new mail filters that automatically forward or delete certain messages, or shared access permissions that let another person read and send mail from your account. If your provider offers alerts for these kinds of changes, turn them on.
Forwarding does have valid uses, but it should never run silently. Treat it as an intentional setting that is checked, documented, and monitored.
Advanced email protection tips
Use email aliases to hide your real address
Aliases reduce exposure and make cleanup easier. You can use separate addresses for shopping, newsletters, job sites, and forums, for example. If one of those aliases ever leaks or starts receiving spam, many providers let you turn it off or delete it, so mail sent to that alias never reaches your inbox and doesn’t affect your main email address.
Some providers support plus addressing (adding a tag after your name, like alex+shopping@example.com), while others offer fully masked addresses with controls to pause, route, or remove them.
Aliases also help with organization; you can filter certain addresses into folders or apply stricter rules while keeping your primary inbox uncluttered. For setup examples, see our guide on email masking.
Set up spam and junk filters effectively
Good spam filtering lowers risk by reducing the odds of a bad click. Start with your provider’s default setting, then train it by marking any unwanted emails you receive as spam and flagging legitimate messages that slip into your junk mail as safe. Over time, the filter will adapt to what you accept and reject.
Keep an allowlist for people or services you can’t afford to miss, and use rules or folders to route bulk mail like newsletters so it never buries important messages. Check the spam folder once a week to catch mistakes.
In a small business, you should manage these rules centrally and give staff a clear way to escalate when something is wrongly flagged. For a broader checklist that applies to teams, see our cybersecurity tips for small businesses.
Should you use PGP or end-to-end encryption (E2EE)?
Most email services encrypt traffic in transit with TLS, but the provider itself can still read your messages. E2EE goes further by locking the content with the recipient’s public key so only their private key can open it. Pretty Good Privacy (PGP) and S/MIME are well-known systems for this; both combine public-key and symmetric encryption and support digital signatures to prove authenticity.
Some email providers offer built-in E2EE. Proton Mail, for example, always uses E2EE for messages between Proton users, while emails to outside addresses are only end-to-end encrypted if you enable password protection. Without that step, they fall back to standard TLS.
The trade-off is complexity: PGP and S/MIME require both sender and recipient to manage keys, while provider-based E2EE is easier but usually only works seamlessly inside the same service. Metadata such as the sender, recipient, and subject line remains visible either way.
You should also use a VPN to strengthen your email security. It hides your IP address, prevents your ISP from tracking which service you use, and protects traffic on unsecured Wi-Fi. While it doesn’t encrypt your email end-to-end, it adds another layer of defense against tracking and network-based attacks.
Should you use an encrypted email client?
Yes, if you want more control over how your email is secured and stored. A secure encrypted client validates server certificates, enforces encryption protocols, lets you configure security settings, and supports message-level encryption standards such as PGP or S/MIME.
The trade-off is convenience. Webmail services like Gmail or Outlook already apply strong protections in the background, while an email client shifts more of the responsibility to you. If you allow the client to cache email offline (download and store copies of your inbox on your laptop or phone), you must secure that device with full-disk encryption. Otherwise, someone who steals the device could access the stored mail directly.
If you deal with confidential information or juggle multiple accounts and want a single place to manage forwarding rules and settings, a secure client is worth considering. But for everyday users, modern webmail often provides sufficient protection with less effort.
What to do if your email has been compromised
Immediate steps to take if your email is hacked
 If you suspect your email has been compromised, act quickly. The goal is to regain control and remove anything the attacker may have added.
If you suspect your email has been compromised, act quickly. The goal is to regain control and remove anything the attacker may have added.
- Check access: If you can still log in, go straight to your account’s security settings and secure your account using the following steps. If you can’t sign in, start the recovery process immediately; using a device and network you normally use improves the chances of success.
- Change the password: Use your password manager to generate a strong, unique password, save it, and immediately update your email account with this new password. This cuts off the attacker from reusing the old one.
- Reset 2FA: Remove devices you don’t recognize, add back your own authenticator app or hardware key, and generate new backup codes. This stops an attacker who may have registered their own method.
- Revoke access: Sign out of all sessions. Remove devices you don’t recognize and delete any suspicious app passwords or third-party connections.
- Check your settings: Check forwarding rules, filters, delegated access, and recovery contacts; attackers often use these to keep a foothold even after a password change. Delete anything you didn’t set up.
- Scan your devices: Update your operating system and browser, then run antivirus scans on both your phone and computer. If you suspect malware that steals cookies or tokens, clear all browser sessions after updating, and only sign back in from clean devices.
How to alert your contacts and secure other accounts
If your email was compromised, warn recent contacts so they don’t fall for follow-up scams. Use a different channel you still control (another email address, a messaging app, or even SMS). Explain that your account was breached and ask them to ignore unusual messages. If money or sensitive files were requested, call those contacts directly to confirm nothing went through.
Then, turn to the accounts tied to your inbox. Attackers who get in often dig through old emails looking for password reset links, bank alerts, or stored codes. Check your financial accounts, cloud storage, and social media for unfamiliar logins or reset notices. Change the passwords on those services and add 2FA if it’s not already on. Even if nothing looks out of place yet, assume linked accounts could be at risk and reset them proactively.
Using email recovery and support tools
Most providers offer built-in recovery flows that guide you through regaining access. They may ask you to confirm a secondary email or phone number, answer security questions, or verify your identity with documents.
If self-service recovery doesn’t work, reach out to customer support; many providers have dedicated teams for compromised accounts, and some premium services offer specialized security support. The faster you start this process, the better your chances of locking out the attacker. Once access is restored, run the provider’s security checkup (like Google’s Security Checkup) to review recent logins, connected devices, and recovery settings. Remove anything you don’t recognize.
It’s also a good idea to preserve evidence before making changes. If you find suspicious emails, save them with their full headers (in many clients, this is under “View original,” “Show source,” or “Message headers”). Headers show which servers handled the email and can help investigators trace the origin. Keep attachments or links as files without opening them, since they may be needed by support staff, your bank, or law enforcement.
Finally, report what happened. Most providers include a “Report phishing” or similar option to flag malicious emails. If money was involved, notify your bank or payment service immediately and share the evidence you collected.
FAQ: Common questions about email protection
How do I know if my email has been hacked?
Clues include login alerts you don’t recognize, messages sitting in your Sent folder that you never wrote, or password reset emails for accounts you didn’t touch. Look through your account’s device history and forwarding rules; attackers often add new entries to keep access. If you see anything you can’t explain, change the password at once and reset two-factor authentication (2FA).
Is Gmail more secure than Outlook?
Both Gmail and Outlook encrypt mail in transit, scan for phishing, and support two-factor authentication (2FA). Gmail builds on Google’s ecosystem with tools like login alerts and its Advanced Protection Program, while Outlook with Microsoft 365 gives admins policy controls suited for business. For individual users, the baseline protections are similar; the overall security of your account depends on how you configure it.
How often should I change my email password?
Change it right away if you suspect a breach or if the password was reused anywhere. Otherwise, a strong, unique password stored in a password manager doesn’t need frequent rotation. Regular checks for reuse or leaks are more effective than scheduled changes.
Can someone track me through my email address?
Yes. Marketers or attackers can confirm that your inbox is active and use tracking pixels in emails to see when you opened a message, your device, and sometimes your IP address. Blocking remote content, using aliases for sign-ups, and using a VPN all help to prevent this kind of tracking.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN


















Comments
Would you recommend ProtonMail and Disroot.org as privacy conscious email providers?
Vgg
I love you
I have been having trouble with sending my e-mails, not receiving, After several days of trying everything to get it right, I tried turning off ExpressVPN and to my amazement, my emails could be sent. Is there a setting in ExpressVPN that will allow me to send emails when I have the VPN connected. I am using Windows 10 and eM Client as my email program. I also had the same problem when I used Outlook. Regards - Graeme Keed