How to stop phone mirroring on iPhone and Android?


Phone mirroring, a process where your smartphone’s screen and actions are shown on another device, can be a powerful tool for presentations, education, and troubleshooting. However, in the wrong hands, it poses a significant privacy risk.
When your device is mirrored, everything on your screen is shown on another screen. This could be done intentionally, such as if you want to enlarge the contents on your phone by showing it on your TV screen. Mirroring could also be done as a form of attack to see everything you’re doing on your phone.
Unauthorized mirroring can expose sensitive information, personal messages, and even your passwords.
Protecting yourself while mirroring your phone is easier than you think. With ExpressVPN, your internet connection stays encrypted even during phone mirroring. This means that any data transmitted remains private and secure, protecting you from hackers or third parties who might try to intercept your connection—especially when using public Wi-Fi in places like the office or a co-working space.
Can someone mirror your phone without you knowing?
Yes, it is possible for cybercriminals to mirror your phone without your consent. However, it’s not very common or easy to achieve. It can be done through spyware or malware downloaded inadvertently by the user, physical access to the device, or even man-in-the-middle attacks. Mirroring makes everything on your screen available to the attackers, which immediately threatens your privacy.
How to tell if someone is mirroring your phone
In many cases, it’s going to be difficult to tell if someone is mirroring your phone without your consent.
The most obvious way to tell is if your phone’s mirroring functionality is turned on and connected to a different device—and you weren’t aware of it.
But if your device has been compromised with malware (or spyware), allowing someone to see everything you’re doing, it might not be as obvious. In such cases, you’ll have to notice strange behavior of your phone, like decreased battery life, increased data usage, or abnormal screen activity. You might also find that someone knows a lot about you when they shouldn’t, including messages you’ve been sending or websites you’ve been browsing.
How can someone mirror your phone?
Mirroring a phone involves displaying its content on another device in real-time. This can happen in several ways, each requiring varying levels of access to your device:
- Screen sharing apps. Legitimate applications designed for screen sharing can be misused. If someone gains access to your phone, they can install such an app and view your screen remotely.
- Spyware. Malicious software designed to operate stealthily can be installed on your device. This software can capture your screen, among other private data, and send it to a third party without your consent.
- Network interception. Attackers can exploit public or unsecured Wi-Fi networks to intercept data transmitted from your phone, including screen activity, if proper encryption isn’t used. This is called a man-in-the-middle attack.
- Physical access. Direct physical access to your device can allow someone to set up mirroring or monitoring tools. This is more straightforward but requires the attacker to have temporary control over your device.
- Phishing attacks. By tricking you into clicking malicious links or downloading compromised applications, attackers can gain control over your phone, including screen mirroring capabilities.
Risks of unauthorized phone mirroring
You may still be wondering how bad unauthorized phone mirroring can really be. Unauthorized phone mirroring exposes you to various risks, from personal privacy breaches to financial fraud. Let’s get into some of them.
Loss of privacy
If someone mirrors your phone, every message you send, every photo you view, and every app you interact with can be monitored remotely. This means confidential conversations, private photos, and sensitive information are no longer just yours.
Compromised passwords
As you type or access passwords on your device, a third party will also see them, potentially revealing your login credentials. This can extend to email, social media, banking, and any other secured service you use on your phone.
Lowered physical safety
If you use a map application such as Google Maps, someone looking at your screen will also know where you are and where you want to go. Any address you’ve searched can be paired with any messages you exchange with people you’ll meet, and an attacker will know your current and future location.
How to stop someone from mirroring your phone
To prevent unauthorized phone mirroring for both iPhone and Android devices, there are several measures you can take.
How to stop phone mirroring on iPhone
Disable mirroring
Mirroring on iPhone is called AirPlay, and you can ensure it is turned off.
- Open Control Center by swiping down the screen from the top right corner and tap the Screen Mirroring button. Note that it may or may not say “Screen Mirroring” according to your layout, but it will always have two overlapping rectangles.
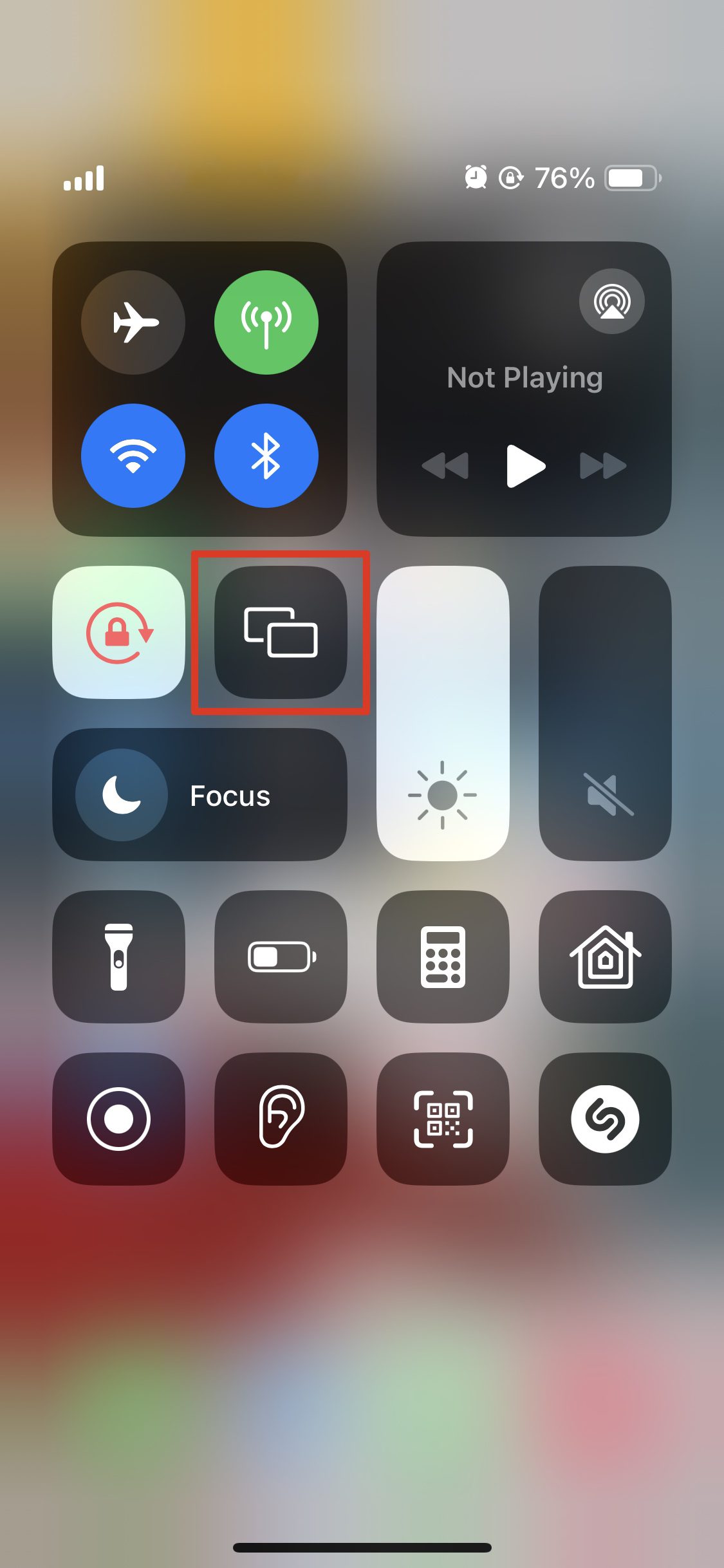
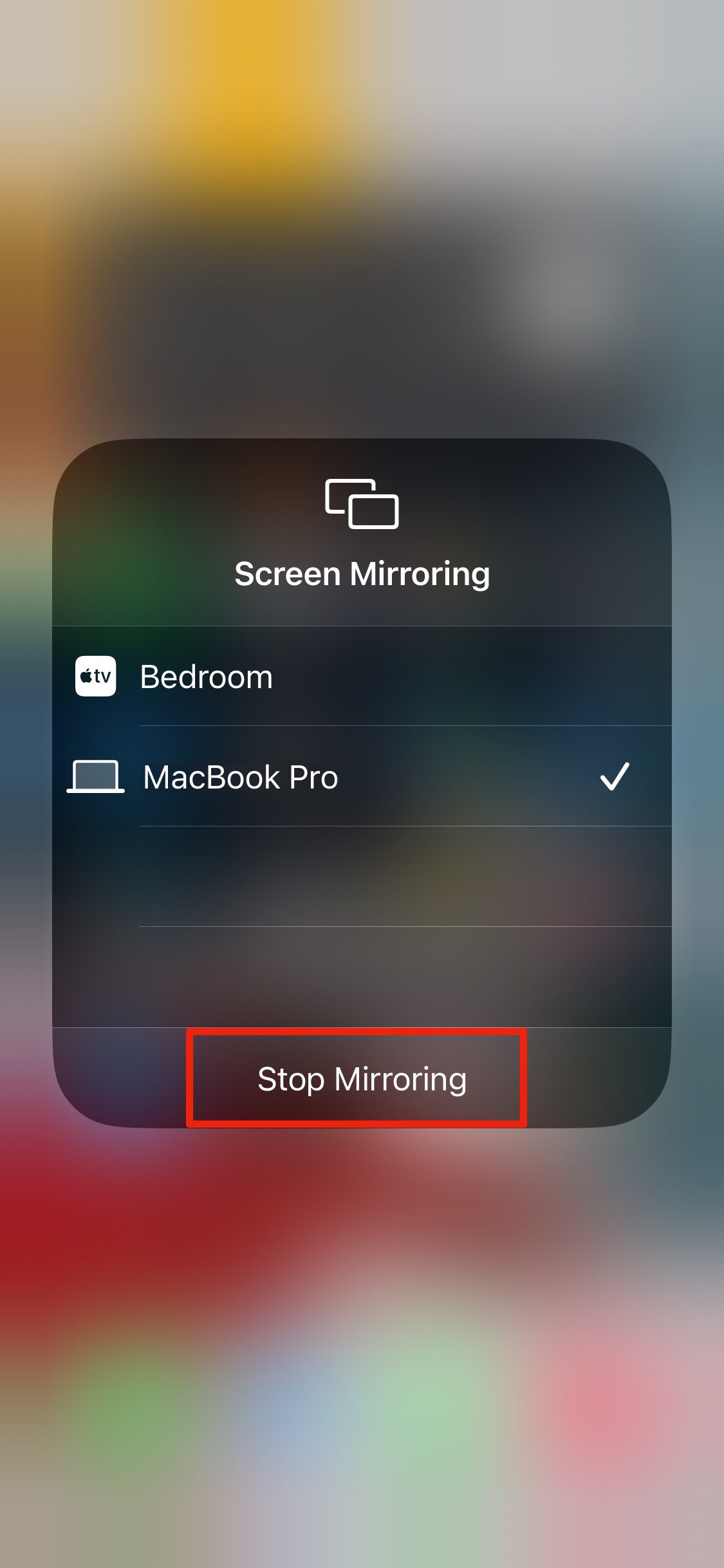
2. Tap on Stop Mirroring.
Delete any sketchy apps
Check your phone for apps that could be spying on you. It’s important that you follow the method below and don’t just review your home screens, because some apps might not have an icon there.
1. Open your app library by swiping left on your home screen. If you have many icons on your home screen, it could take a few swipes.

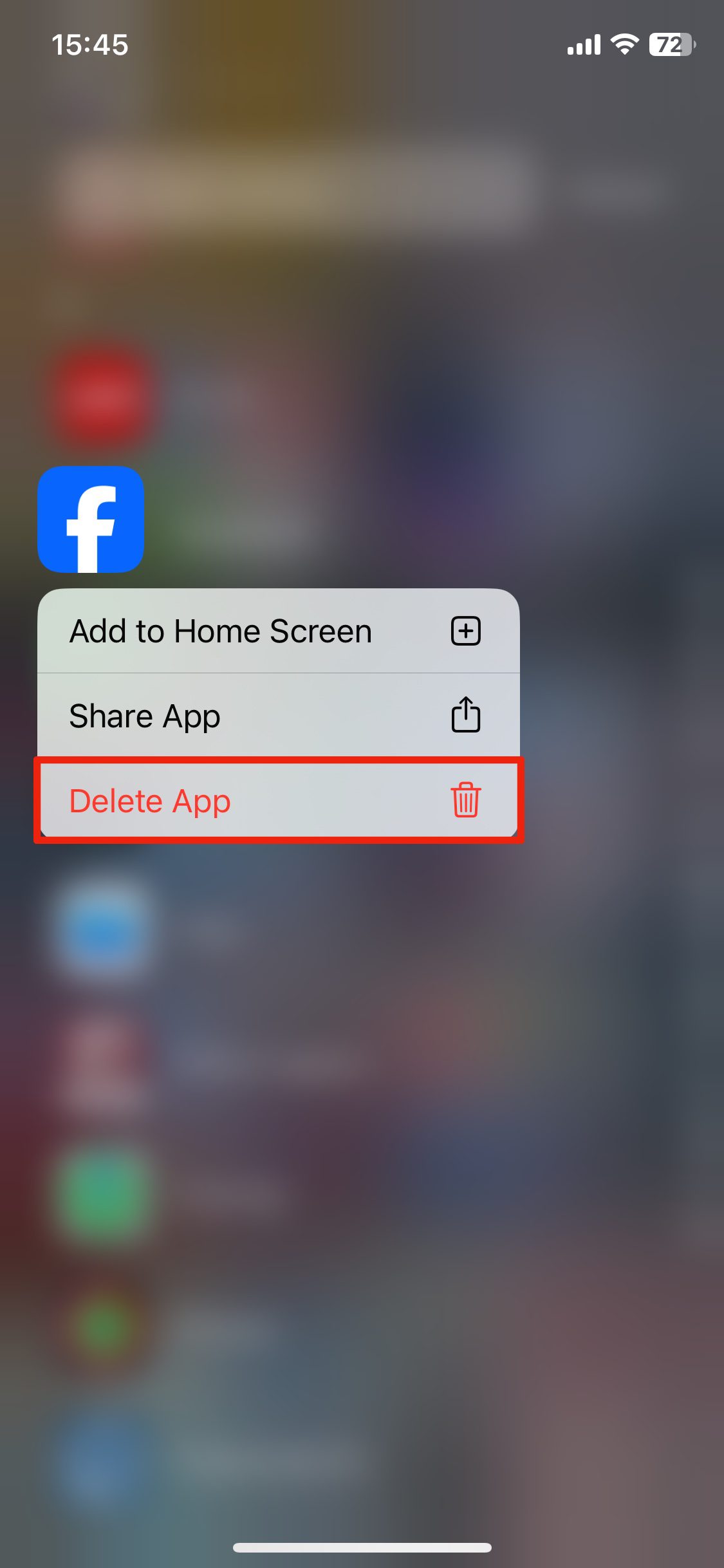
2. Go through the entire list of apps. If you see any that you suspect are malicious or would otherwise like to remove, tap and hold the icon and select Delete App.
Factory reset your iPhone
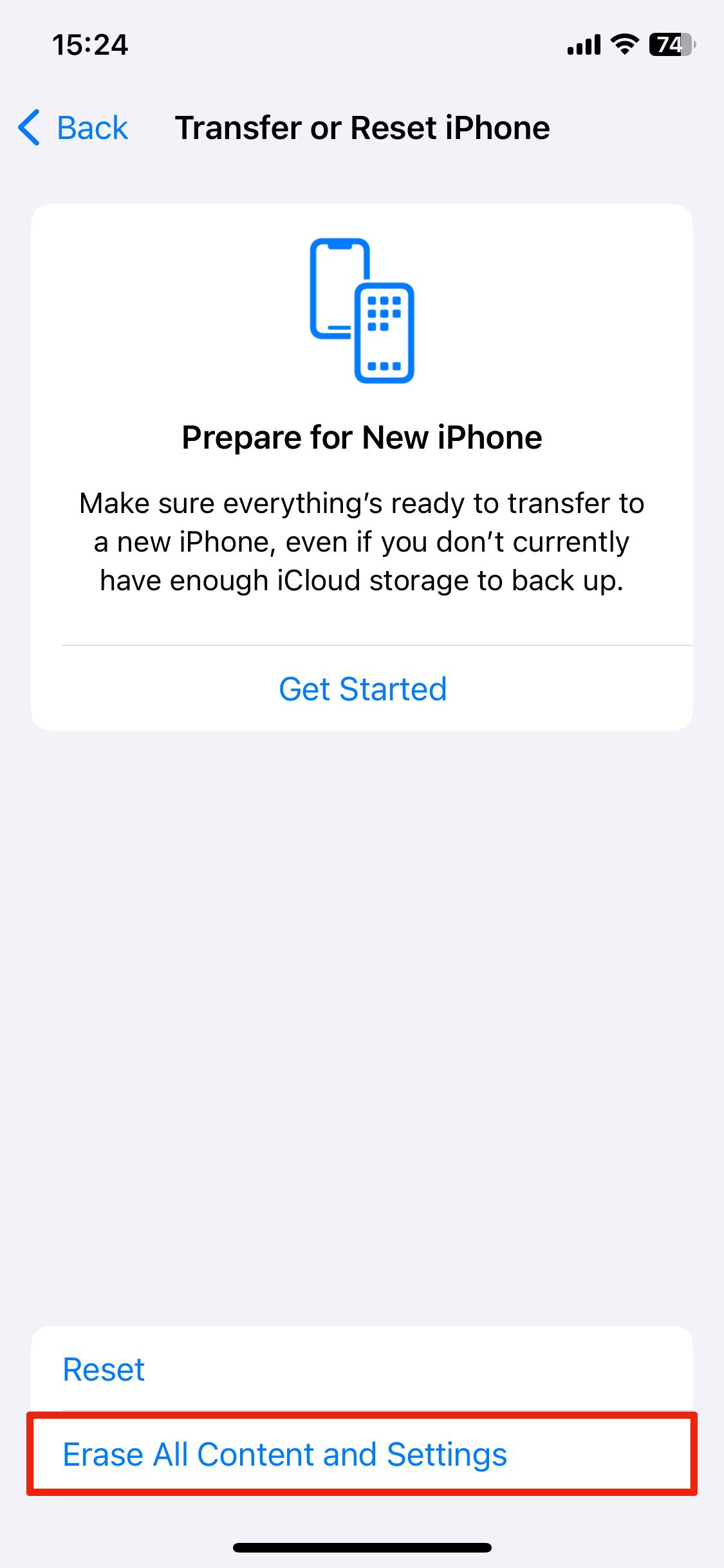
If you still have doubts about whether your screen is still being mirrored via malicious software, you could reset it to factory settings. Note that this will delete all your content, so make sure you have a backup of your important information. To reset your iPhone, follow these steps:
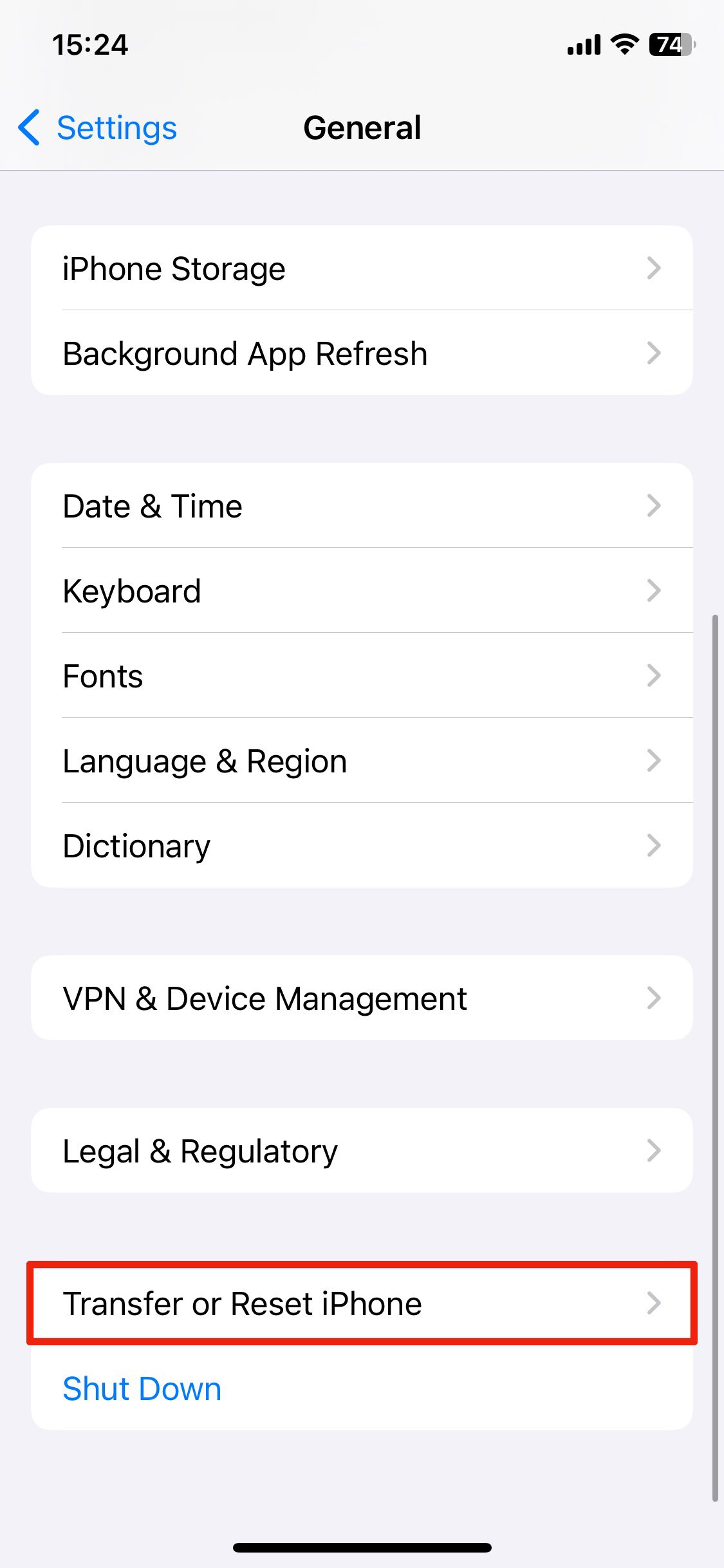
1. Open Settings, and then choose General.

2. Scroll down and choose Transfer or Reset iPhone.
3. Now choose Erase All Content and Settings at the bottom of your screen.
How to stop phone mirroring on Android
Disable mirroring
The first line of defense should be to disable mirroring. The functionality is called something different on various Android devices. In Samsung phones, it’s called Smart View. Go to the setting in your phone, and you’ll see any devices that you may connect to. Ensure no devices are mirroring your phone.
Manually delete any suspicious apps
Carefully review your installed apps and delete any that you don’t recognize by following these steps:
- Open the Google Play Store.
- Tap your profile icon at the top right.
- Choose Manage apps and devices.
- Tap Manage.
- Carefully scroll through the list, and select the apps you want to delete.
- Click on Uninstall.
Factory reset your phone
While extremely effective, remember that resetting your phone will delete all your content, so ensure you have a recent backup.
- Open Settings.
- Go to General management.
- Tap on Reset.
- Select Factory data reset and then press Reset.
- Enter your security pattern (or PIN).
- Press Delete all.
Reinstall your OS
Reinstalling the OS goes one step further than resetting to factory settings by loading a completely new image from another source. If you’re an advanced user, you could connect your phone to your computer and flash it.
Can you stop someone from mirroring your phone?
Yes, turning off your Bluetooth and Wi-Fi connections should immediately stop someone from mirroring your phone. There are other ways to stop someone from mirroring your phone, which we’ll look at below.
How to prevent unwanted phone mirroring
Preventing unauthorized access and mirroring of your phone requires a proactive approach to security. Here are key strategies to safeguard your device:
1. Keep your OS updated
Regularly update your phone’s operating system. Updates often include security patches that address vulnerabilities and can also improve the overall performance and stability of your device. These updates often introduce new features and remove outdated ones, ensuring your phone runs efficiently. It’s a simple yet crucial step in maintaining your device’s security and functionality..
2. Be cautious with apps
Only download apps from trusted sources like the Apple App Store or Google Play Store. Regularly review app permissions and uninstall any apps that aren’t in use or seem suspicious. Apps may occasionally go out of service and it’s important to delete them as they’re likely not going to receive anymore support or updates.
3. Be alert to phishing attempts
Be cautious about sharing your information with individuals pretending to be from trusted organizations. Always verify the authenticity of the request before providing any personal details.
4. Disable features not in use
Turn off Bluetooth, NFC, and other wireless connections when not in use to prevent unauthorized access. Additionally, regularly update your devices' software to patch any security vulnerabilities, and use strong, unique passwords for all your accounts. Consider using a VPN, especially on public Wi-Fi, to further protect your data from potential eavesdroppers.
5. Regularly monitor your phone’s activity
Pay attention to your phone’s performance, battery life, and data usage for signs of unauthorized activity. Additionally, keep an eye out for unexpected app installations or unusual messages and calls that could indicate your device has been compromised.
6. Use screen locking features
Enable features like automatic screen lock and facial recognition or fingerprint scanning to prevent unauthorized physical access to your device. Additionally, consider encrypting sensitive files and using secure passwords or multi-factor authentication for an extra layer of security. Regularly updating your device's operating system and applications can also protect against the latest security vulnerabilities.
7. Review connected devices
Regularly review the list of devices connected to your accounts and remove any that you don’t recognize or no longer use.
8. Don’t jailbreak or root your phone
Attempting to modify your phone, such as jailbreaking or rooting, can significantly alter the security measures implemented by manufacturers like Apple and other companies. These security features are designed to protect your device and personal information from unauthorized access and malicious attacks.
By modifying your phone, you might unintentionally disable these protections, making your device more vulnerable to security breaches. Such alterations can potentially expose your phone to malware, compromise your personal data, and even render some functions or apps inoperative. Manufacturers typically caution against unauthorized modifications for these reasons, emphasizing the importance of maintaining the integrity of the device's built-in security mechanisms.
9. Avoid charging your devices in public places
It’s become increasingly common for attackers to use public USB charging points and cables to install malware on devices. These charging points, often found in airports, hotels, or cafes, can be tampered with to facilitate the unauthorized installation of malware on unsuspecting users' devices.
This form of cyber attack, known as "juice jacking," leverages the USB connection not only to provide power but also to establish a data connection, allowing malware to be silently installed on the device or sensitive data to be exfiltrated. If you’re concerned, avoid using public charging points and carry a portable battery pack instead.
10. Secure your Wi-Fi connections
Avoid using public or unknown Wi-Fi networks without protection when mirroring your screen. If you absolutely have to do it on public Wi-Fi, make sure to download a reputable VPN service such as ExpressVPN to encrypt your data transmission on public networks.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN




Comments
Is it possible for someone to access your phone though the WiFi and then mirror your phone using the same name as your phone so if it comes up on your device list it looks like your phone name? Can someone remotely use my phone and information as a remote connection to access, say, my other friends phones? If so how can I prove its not me to the authority? Please help, this is way out of my comfort zone, but I need proof so that it stops!
I'm having the same issue. The police department has installed a device on the inside of my phone that is constantly recording the back drop or the apps running in the back ground. With this they have gotten the IP of the other devices ( yes multiple) they pull this in info weekly off the phone. I also hired a developer to mirror the phone ( legally) of the person's devices that's doing it to me. I've been dealing with this for 5 or longer months and we are about done. It will be a slam dunk case when we are done and the person is looking at 35 years as of now. We have decided to continue surveillance on them maybe 2 more weeks to assure there is no way they can walk per the prosecutor. It's a hard thing to deal with not to mention how you NEVER have any privacy. Talk to your police department daily if you need to and ask for help. It's out there! I'll pray for you and good luck.