Botnet explained: Types, attacks, detection & protection tips

Botnets, also known as robot networks, are one of the biggest cybersecurity threats online, yet they often go unnoticed. These networks of infected computers, routers, and smart devices quietly turn everyday tech into tools for cybercriminals. They spread malware, steal data, and launch attacks—all without their owners realizing. The real danger? Many people don’t know their devices are part of a botnet until it’s too late.
As internet-connected devices multiply, so does the risk of botnet infections. This guide covers what botnets are, how to detect them, what to do if you’re affected, and how to keep your devices secure.
Botnet definition and how they work
Before you can protect yourself from botnet attacks, it’s important to understand what botnets are, how they work, and the types of attacks they carry out.
What is a botnet?
A botnet is a network of hacked devices—including computers, routers, and even smart cameras—that are controlled remotely by a botmaster. These devices can be used to spread malware, steal data, and carry out cyberattacks, often without their owners realizing.
Botnets are commonly used for DDoS attacks, spamming, fraud, and data theft. Some are even rented out to other cybercriminals, making them a massive security risk.
While IoT devices (like smart speakers, security cameras, and home routers) are often targeted due to weak security, any internet-connected device can be part of a botnet.
Not all botnets are malicious, though. Some legal botnets, like SETI@Home and Folding@Home, allow people to donate their device’s computing power for scientific research.
How do botnets operate?
A botnet forms when malware infects a device and connects it to a network controlled by a botmaster. This can happen in several ways:
- Phishing emails that trick people into opening infected attachments
- Fake software downloads that secretly install malware
- Pirated software that comes bundled with malicious code
- Exploiting security flaws in outdated devices
Many botnets use Trojan malware, which disguises itself as a harmless file or program to gain access. Once installed, it gives the botmaster remote control over the infected device.
After infection, the compromised device can follow remote commands and even help spread malware to other devices. Some botnets actively scan the internet for vulnerable systems, while others rely on phishing scams to trick users into downloading malware.
As a botnet grows, it can expand from a few infected devices to thousands—or even millions. With this scale, botnets can launch major cyberattacks, including DDoS attacks, financial fraud, and spam campaigns.
The rise of IoT botnets
As smart home devices become more common, IoT botnets are becoming a bigger problem. Many smart devices—like security cameras, speakers, and fridges—lack strong security and don’t receive automatic updates. This makes them easy targets for attackers.
Read more: When the Internet of Things goes wrong
The role of botmasters and zombies
A botnet wouldn’t exist without the person controlling it—the botmaster. This could be an individual hacker, a cybercriminal group, or even a state-sponsored actor. Botmasters operate remotely, using infected devices to carry out cyberattacks, send spam, or even mine cryptocurrency. Some run botnets for their own use, while others rent them out to criminals who pay for access.
Once a device is infected, it becomes a “zombie”—a compromised machine that silently follows the botmaster’s commands. A single zombie might not seem like a big deal, but when combined with thousands (or even millions) of others, botnets can:
- Overwhelm websites with DDoS attacks
- Flood inboxes with spam
- Steal login credentials and financial data
- Spread malware to other devices
Because most zombie devices work in the background, owners usually don’t realize they’ve been compromised. Some botnets remain active for years, running quietly until security measures detect and remove them.
Common botnet architectures and models
Not all botnets operate the same way. Their structure determines how they communicate, issue commands, and resist takedown attempts. Some rely on centralized servers, while others function as peer-to-peer networks that are harder to shut down.
Here’s a breakdown of the three main types of botnet architectures:
Client-server model
The client-server model is one of the oldest and most common botnet structures. Infected devices (clients) connect to a central command-and-control (C2) server, which sends instructions to control their behavior.
Since the entire botnet relies on one or more central servers, shutting down those servers can cripple the botnet—but cybercriminals have found ways to make these networks more resilient.
Star network topology
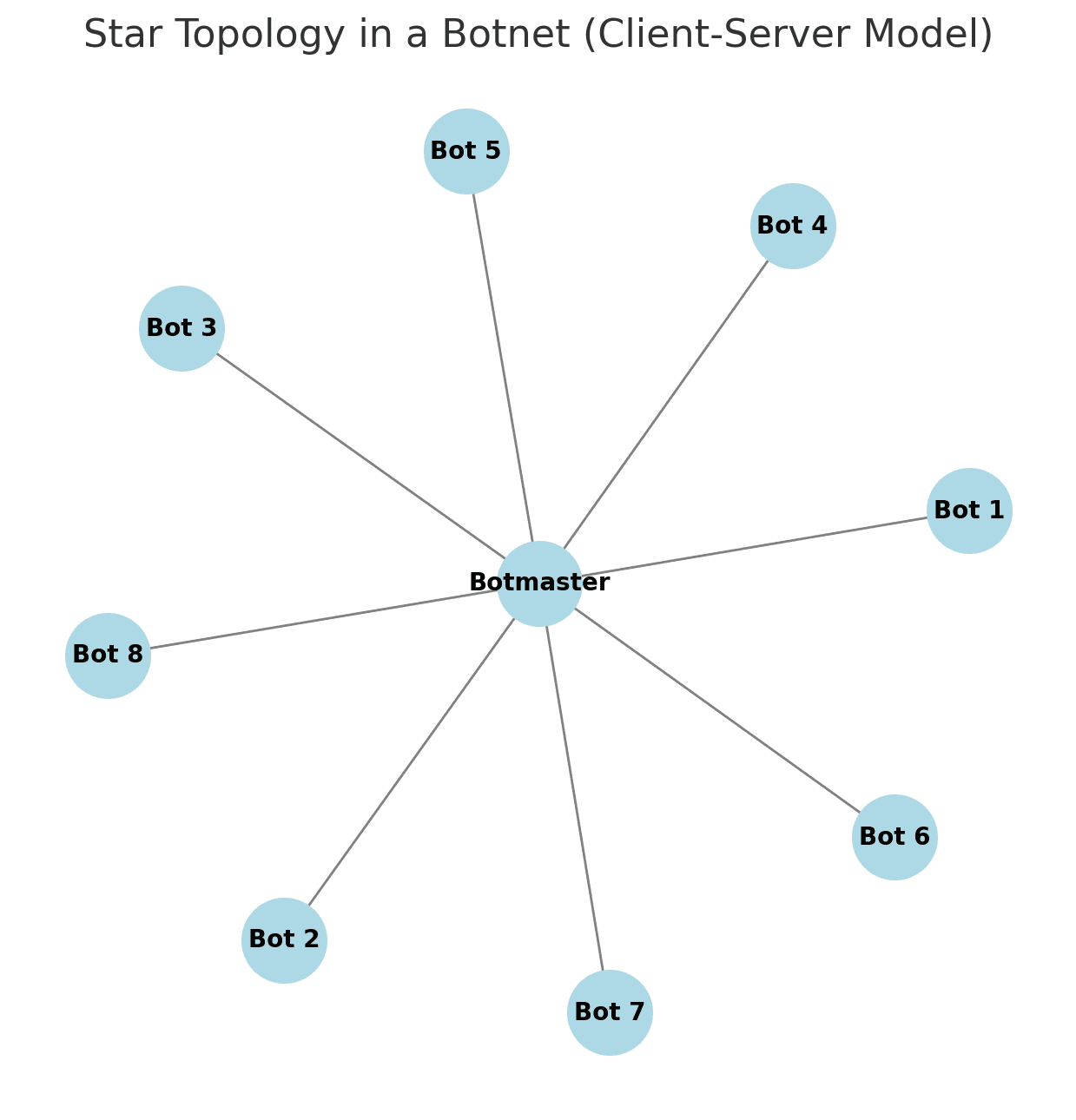
In a star network, all infected devices communicate with a single central server, like spokes on a wheel. The botmaster issues commands through this server, which then distributes instructions to every compromised device.
This setup makes botnet management efficient but comes with a major weakness: If the central server is taken down, the entire botnet collapses.
One of the most infamous botnets using this model was Mirai, which targeted IoT devices like routers and security cameras with default or weak passwords. At its peak, Mirai infected hundreds of thousands of devices and was responsible for the massive DDoS attack on Dyn in 2016, which disrupted Twitter, Netflix, and Reddit.
Multi-server network topology
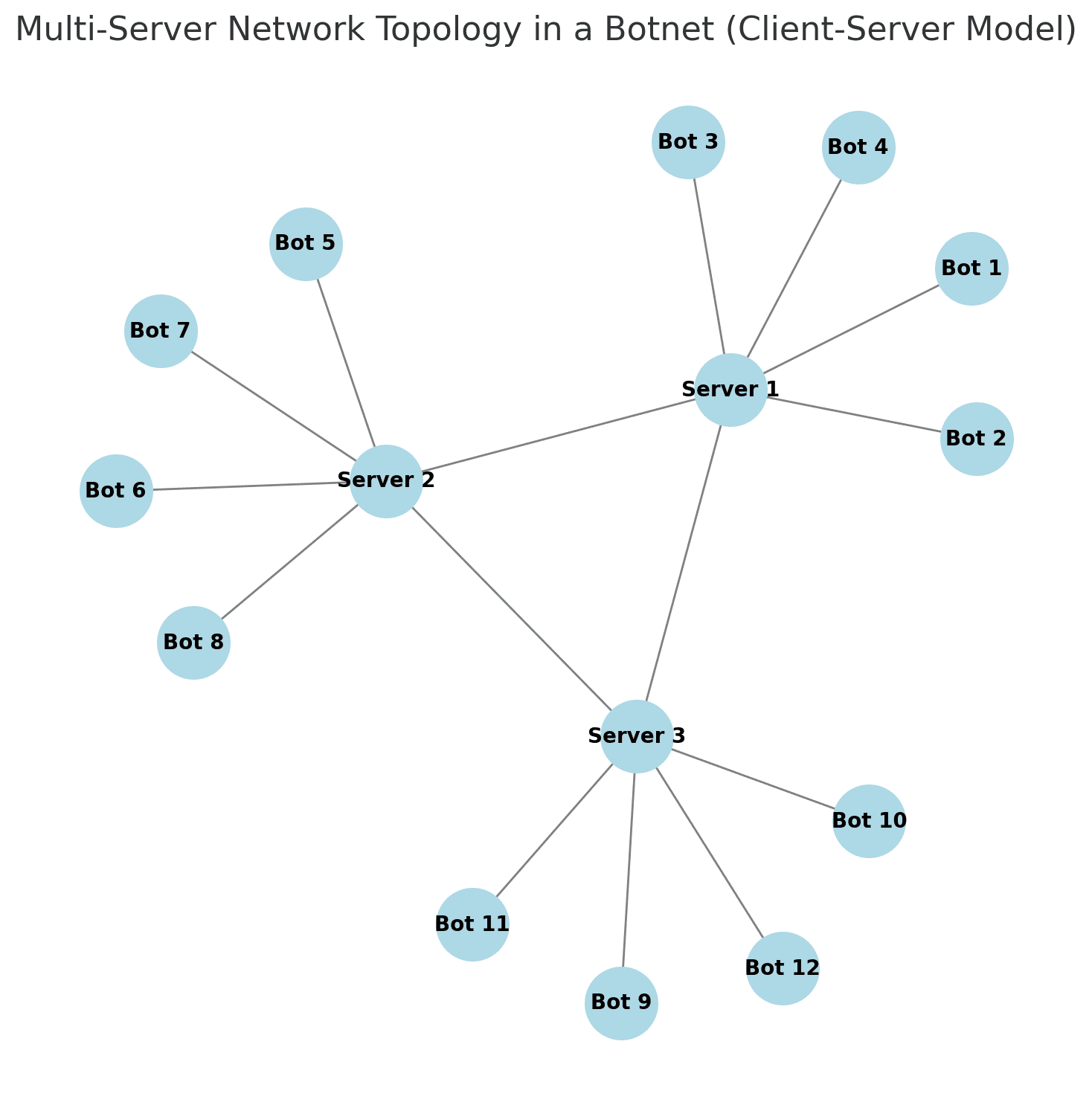
To reduce the risk of a single point of failure, some botnets use multiple command servers instead of one. Infected devices connect to different servers, and these servers communicate with each other.
This setup makes the botnet more resilient—even if one server is shut down, the others keep the network running. Some botmasters take this a step further by switching control servers frequently or using encrypted communication channels to avoid detection.
However, this model isn’t invincible. If enough servers are shut down, the botnet gradually loses effectiveness.
Peer-to-peer model
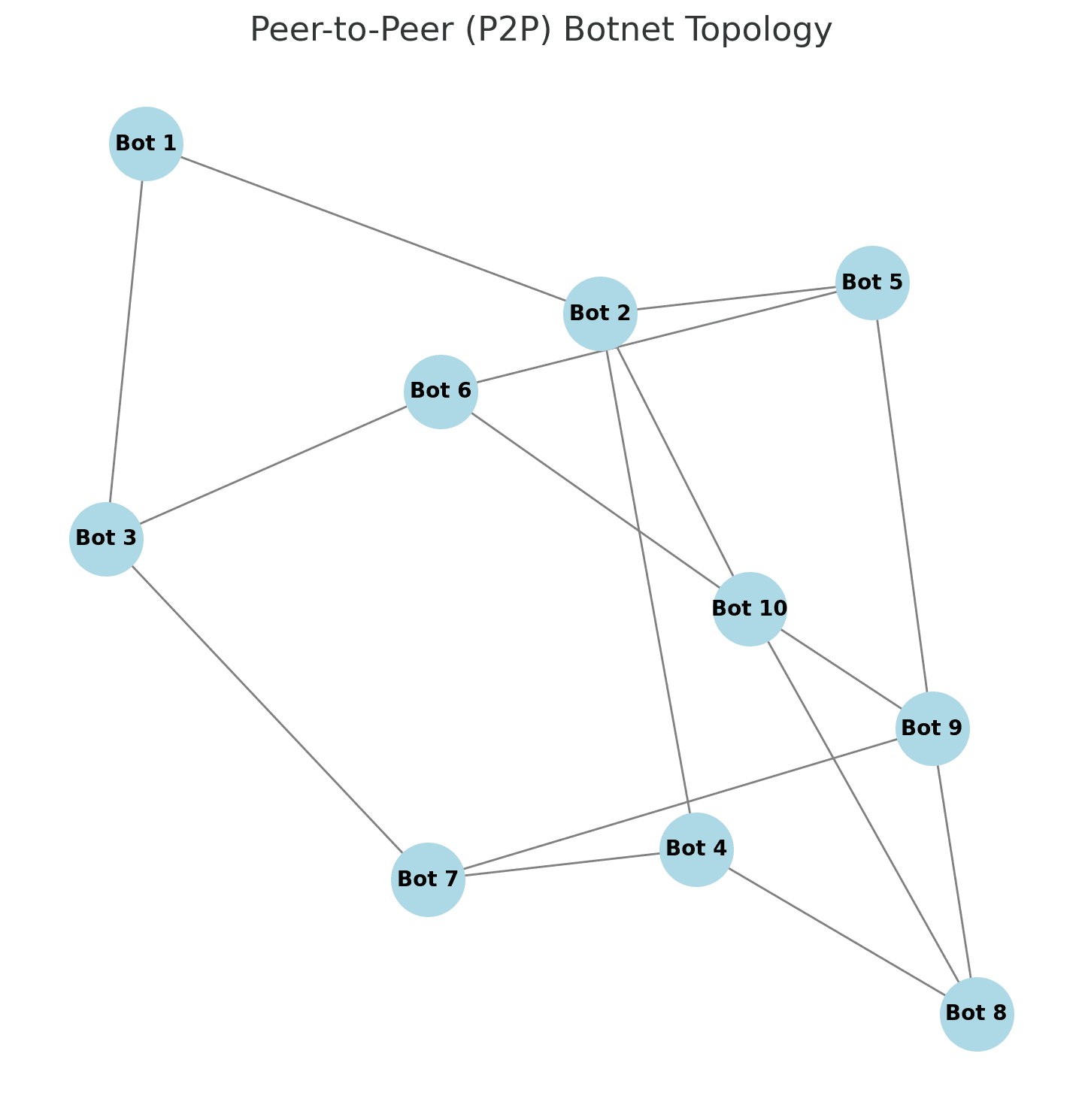
Unlike client-server botnets, a peer-to-peer (P2P) botnet doesn’t rely on a central control server. Instead, infected devices communicate directly with each other, spreading commands across the network.
This decentralized structure makes P2P botnets much harder to dismantle. Even if security experts manage to disable some infected devices, the rest of the botnet remains active and can continue spreading malware.
To make them even more resistant to takedowns, many modern P2P botnets use cryptographic signatures. This ensures that only the botmaster can send commands, preventing outsiders from interfering.
Because of their resilience, P2P botnets are often used for:
- DDoS attacks
- Data theft
- Spamming and malware distribution
Shutting down a P2P botnet is a major challenge for law enforcement and cybersecurity teams since there’s no central server to target.
Types of botnet attacks
Once a botnet is up and running, it doesn’t just sit idle. Botmasters put these networks to work—some for quick financial gain, others for large-scale cyberattacks that disrupt businesses, steal sensitive data, or even manipulate the internet itself.
Some botnets operate loudly, flooding websites with traffic until they crash. Others lurk in the background, silently siphoning off passwords and financial information. No matter the method, the result is the same: cybercriminals profit while unsuspecting users are left vulnerable.
Here’s a look at the most common ways botnets are used in cybercrime.
Distributed Denial-of-Service Attacks (DDoS)
One of the most disruptive botnet attacks is a DDoS attack, where a botmaster instructs thousands (or even millions) of infected devices to overwhelm a website or online service with traffic. The goal? To slow it down or crash it entirely.
DDoS attacks can be financially devastating for businesses. Online stores, streaming services, and banking platforms rely on uptime—every minute of downtime means lost revenue. Some attackers use this as leverage, demanding a ransom to stop the attack. Others carry out DDoS attacks for political reasons, revenge, or simply to cause chaos.
Read more: Wayback Machine cyber attacks: Everything you need to know
Spamming and phishing campaigns
Botnets don’t just attack websites. Many are built to send out massive waves of spam emails, designed to flood inboxes with scam offers or trick people into clicking malicious links.
These emails might look like shipping notifications, tax refunds, or urgent security alerts from a bank. But hidden inside is a phishing link that directs victims to a fake login page, where their credentials are stolen. Some botnets go further, spreading malware through infected email attachments, which can lock files, steal passwords, or install more botnet software.
For cybercriminals, automation is key. With a botnet, they don’t need to send each scam email manually. They simply command their infected devices to do the job for them, ensuring millions of messages are sent in minutes.
Spyware and data theft
Not all botnet attacks are noisy. Some botnets are built to stay hidden, quietly collecting data from infected devices.
Spyware-based botnets log everything you type, track the websites you visit, and even monitor financial transactions. Some use keyloggers to steal passwords, while others track browsing habits to target victims with more effective scams.
Hackers then sell this stolen data on the dark web, where login credentials, bank details, and personal information can fetch a high price. Some botnets go beyond individuals and target businesses, stealing sensitive corporate data for espionage or extortion.
Unlike DDoS attacks, which can be detected quickly, spyware botnets can remain active for months or even years before being discovered.
IoT-based botnet attacks
Smart home devices are everywhere—security cameras, voice assistants, smart locks, even refrigerators. But most of them aren’t built with security in mind, making them easy prey for botnets.
Many IoT devices ship with weak default passwords, and some don’t allow users to change them. Others never receive updates, leaving security flaws open for years. Attackers take advantage of this, scanning the internet for vulnerable devices and infecting them automatically. Once inside, the botmaster can use them to launch cyberattacks, steal data, or even spy on their owners.
One of the largest IoT botnet attacks happened in 2019 when the Mozi botnet infected over 1.5 million devices. Mozi exploited weak passwords on IoT gadgets, turning them into an army of zombie devices used for DDoS attacks and data theft. Unlike earlier botnets, Mozi stayed active for years, continuously evolving to avoid detection.
IoT botnets are especially dangerous because they don’t just affect one device—they put entire home networks at risk. If a hacker controls your smart thermostat or baby monitor, they could use it to infiltrate your router, phone, or laptop. That’s why locking down IoT security—changing default passwords, keeping firmware updated, and securing your network—is more important than ever.
Remote desktop protocol (RDP) attacks
Some botnets don’t need to infect a device to control it—they walk right in through the front door.
Remote Desktop Protocol (RDP) is a tool that allows users to access a computer remotely—common in workplaces, IT support, and cloud systems. But if RDP is left exposed with weak security, attackers can break in without ever sending malware.
Cybercriminals scan the internet for open RDP ports and try common passwords or stolen credentials to gain access. Once inside, they can:
- Turn the system into a botnet zombie
- Steal sensitive data
- Use it as a stepping stone to attack the entire network
In 2020, the GoldBrute botnet targeted over 1.5 million RDP servers worldwide. Instead of infecting devices with malware, GoldBrute brute-forced login credentials, gaining direct access to machines and adding them to its growing botnet.
RDP-based attacks are especially dangerous for businesses, where a single compromised machine can give hackers access to entire networks. Unlike traditional botnets, RDP attacks don’t rely on malware—they use real login credentials. That makes them harder to detect and easier for cybercriminals to exploit.
How to protect yourself from botnets
Cybercriminals are always looking for new ways to expand botnets, whether by exploiting outdated software, tricking people into clicking malicious links, or taking advantage of weak device security. Staying protected isn’t just about avoiding infection—it’s about making sure your devices don’t unknowingly become part of a botnet.
Here’s how to reduce your risk.
Security tips for individuals
Keep software and firmware updated
Botnets often exploit outdated software, apps, and firmware to gain access to devices. If security vulnerabilities aren’t patched, attackers can use them to install malware and take control.
The fix is simple: Keep your operating system, apps, and firmware updated. Most software updates include security patches that close loopholes hackers rely on. Whenever possible, enable automatic updates so you don’t have to remember to install them manually.
Be cautious with emails, links, and downloads
Botnets spread through phishing emails, fake downloads, and malicious ads. Even if a message looks like it’s from someone you trust, it could contain malware.
Some key red flags:
- Unexpected attachments (especially PDFs, ZIP files, or .exe programs)
- Links that don’t match the sender’s email address
- Urgent language pressuring you to act quickly
When in doubt, don’t click. If you need to verify a link, visit the company’s official website instead of clicking through an email.
Use a VPN to protect your network
A VPN (virtual private network) encrypts your internet traffic, making it harder for attackers to intercept data or track your activity. While a VPN won’t stop you from downloading malware or clicking on phishing links, it does add an extra layer of security—especially when browsing on public Wi-Fi.
Be careful with free VPNs, though. Some have weak encryption, track user data, or—like the 911 S5 botnet—turn users’ devices into part of a larger botnet. Stick to a trusted, no-logs VPN like ExpressVPN, which secures your connection without compromising privacy.
Monitor your network for suspicious activity
If your internet suddenly slows down, your device overheats, or you notice unusual network traffic, it could be a sign of botnet activity.
Use a network monitoring tool to check for devices communicating with unknown servers. Some routers have built-in logs that can help identify suspicious connections. If something seems off, disconnect from the internet and run a security scan.
Best practices for IoT devices
As we mentioned above, IoT devices—like smart cameras, speakers, and routers—are easy targets for botnets. Many come with default passwords and outdated firmware, making them vulnerable to attack. Here’s how to secure them:
Change default passwords immediately
Many IoT devices ship with weak, factory-set passwords that hackers can easily guess. Change them as soon as you set up a new device. Use strong, unique passwords, and if possible, enable two-factor authentication (2FA).
Disable unnecessary features and services
Some devices come with remote access features—like Universal Plug and Play (UPnP) and Telnet—enabled by default. These can be exploited by attackers, especially if they don’t require authentication.
Review your device’s security settings and turn off any features you don’t use.
Protect your router
Your router is the gateway to your entire home network. If it’s compromised, every connected device is at risk.
To secure it:
- Change the default admin password
- Turn off remote management (unless absolutely necessary)
- Enable WPA3 or WPA2 encryption
- Use a VPN router to protect IoT devices that don’t support VPN apps
ExpressVPN’s Aircove is a VPN router designed for always-on security. It encrypts your entire home network, protecting every connected device—even IoT gadgets that don’t support VPNs.
Using antivirus and firewalls
Antivirus software and firewalls are effective defenses against botnets and for botnet detection. A good antivirus scans for and removes malware before it can turn your device into part of a botnet. Many antivirus programs also include real-time protection, blocking malicious files and downloads before they can cause harm.
On the other hand, firewalls act as a barrier between your device and incoming threats, filtering out suspicious connections and preventing unauthorized access. Enabling your system’s built-in firewall and using a network firewall on your router adds another layer of security, keeping botnet traffic from spreading across your network. For the best protection, update your antivirus and firewall regularly, as new botnet threats emerge constantly.
How to detect and remove a botnet infection
Botnets can run silently in the background for weeks—or even months—without showing obvious signs. They might be using your device to send spam, participate in a DDoS attack, or even mine cryptocurrency without your knowledge.
If your device is acting strangely, here are the key signs it might be part of a botnet:
Signs your computer might be part of a botnet
Unusual network activity
Botnets communicate with command-and-control (C2) servers to receive instructions and send stolen data. Signs of suspicious network activity include:
- Unexplained spikes in outgoing traffic
- Large data transfers to unknown IP addresses
- High bandwidth usage, even when you’re not using the internet
Use network monitoring tools to detect abnormal traffic patterns.
Sudden slowdowns and overheating
A botnet infection can put extra strain on your system, causing it to slow down, overheat, or drain battery life more quickly. This is especially common in botnets that mine cryptocurrency or perform DDoS attacks, as they use significant processing power.
Frequent system crashes or software failures
Some botnet malware modifies system settings or disables security tools, causing instability. If your operating system or apps frequently crash, freeze, or stop responding, it could indicate an infection.
Strange background processes or unknown programs
If you see unfamiliar programs, browser extensions, or background tasks running, your device could be compromised. Checking your Task Manager (Windows) or Activity Monitor (Mac) for unknown processes using excessive CPU or network resources can help identify suspicious activity.
Blocked access to security websites
Some botnets prevent infected devices from reaching cybersecurity websites to stop users from downloading antivirus tools or updates. If you suddenly can’t access security-related sites, it could be a sign that malware is interfering with your connection.
Unauthorized emails or messages sent from your accounts
Some botnets turn infected devices into spam machines. If your email outbox contains messages you didn’t send or friends report receiving strange links from you, your device or account may be compromised.
Your IoT devices are overheating
IoT botnets often use smart devices like speakers, security cameras, and routers to carry out attacks. If your IoT device is overheating, running slower than usual, or behaving strangely, it could be infected and working in the background to power a botnet.
Steps to remove botnet malware
If your device is part of a botnet malware, acting fast is the best way to prevent further damage. Follow these steps to clear out the infection and secure your system:
Run a full system scan with antivirus software
A strong antivirus program can detect and remove most botnet malware. Run a full system scan using a trusted security tool, making sure your software is updated to detect the latest threats. If malware is found, follow the removal instructions provided by your antivirus.
End suspicious programs and remove unknown software
Check Task Manager (Windows) or Activity Monitor (Mac) for processes using a high amount of CPU, memory, or network activity. If you see an unfamiliar program consuming significant resources, research it online. If it’s linked to malware, end the process and delete any related files.
Change all your passwords
Botnets can steal login credentials, so updating your passwords is crucial. Change passwords for your email, banking, social media, and any other important accounts. If possible, enable multi-factor authentication (MFA) for added security.
Disconnect from the internet
To stop the botnet from communicating with its command server, disconnect your device from Wi-Fi or unplug your Ethernet cable. If an IoT device is infected, power it off until it can be reset.
Reset or update your router
Botnets often target routers to infect entire networks. If you suspect an infection, update your router’s firmware to patch vulnerabilities. If the issue persists, reset it to factory settings and set up a strong, unique password.
Enable firewalls and strengthen security
Firewalls can block unauthorized connections, preventing botnets from sending or receiving commands. Make sure your system’s built-in firewall is turned on and consider enabling your router’s firewall for extra protection.
FAQ: About botnets
What is an example of a botnet attack?
Another example is the Emotet botnet, which spread through phishing emails containing malicious attachments. Once a computer was infected, Emotet stole sensitive information and used the compromised system to send more phishing emails, growing the botnet.
Are botnets illegal?
However, some legal botnets exist for distributed computing projects, like Folding@Home, which uses volunteer computers to simulate protein folding for medical research.
How do hackers control a botnet?
- Client-Server Model (Centralized Control) – Infected devices connect to a central server, which sends commands and coordinates attacks. This model is efficient but easier to take down if the server is identified and shut down.
- Peer-to-Peer (P2P) Model (Decentralized Control) – Infected devices communicate with each other rather than relying on a single server. This makes it much harder to dismantle the botnet since there’s no single point of failure.
Botmasters (the hackers controlling the botnet) often hide their C2 servers using Tor, proxy networks, or fast-flux DNS techniques to avoid detection.
Why do scammers like botnets?
- Massive Reach – A botnet can have millions of infected devices, making it easy to launch widespread attacks.
- DDoS botnet for Hire – Attackers rent out botnets to criminals who want to take down websites through DDoS botnet attacks.
- Spam and Phishing Campaigns—Many botnets send millions of scam emails daily, tricking people into clicking malware-infected links.
- Stealing Credentials and Financial Information – Some botnets include keyloggers that record everything a victim types, including passwords and credit card details.
- Cryptojacking – Botnets can hijack infected devices’ processing power to mine cryptocurrency, generating profits for scammers without the victim knowing.
How can I protect myself from botnet attacks?
- Keep your software updated – Regularly update your operating system, apps, and firmware to patch security vulnerabilities before attackers can exploit them.
- Use a VPN – A trusted VPN encrypts your internet traffic, making it harder for hackers to target your device, especially on unsecured networks.
- Install antivirus software and firewalls – A good antivirus program can detect and remove botnet malware, while a firewall blocks unauthorized access to your device and network.
- Monitor your network activity – Check your router logs or use network security tools to spot unusual spikes in traffic, which could indicate a botnet infection.
- Be cautious with links and downloads – Avoid clicking on suspicious links or downloading files from unknown sources, as botnets often spread through phishing emails and malicious attachments.
- Secure IoT devices – Change default passwords on smart home devices like routers, security cameras, and smart TVs. These are common botnet targets due to weak security settings.
- Enable multi-factor authentication (MFA) – Adding an extra layer of security makes it much harder for attackers to gain control of your accounts.
- Be wary of free VPNs and proxy services – Some free services have been found to exploit users’ devices, turning them into part of a botnet. Stick to reputable providers that prioritize security.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN