Dark web scan: Is your personal data at risk?

Dark web scans help you find out whether and where your data may have been leaked on the dark web.
A personal data leak may include your email, Social Security number (SSN), insurance ID, name, physical address, phone number, and much more. Cybercriminals can use these to steal your identity, compromise your accounts, or even blackmail and extort you.
In this guide, we’ll explain what a dark web scan is, why it’s useful, how to do a dark web scan for free, and how it differs from dark web monitoring.
What is a dark web scan?
A dark web scan checks for personal information leaks on the dark web. Many dark web scan tools also check people directory websites and data broker databases. This is because leaked personal data may appear on these sites, and cybercriminals could collate and sell data from these sites or leak it on the dark web.
How does a dark web scan work?
 The first step in a dark web scan is to provide the data you want to check for leaks to a dark web scan tool. This data could be anything the scanner supports: some scanners can only check for your email address, but others can scan for your name, passwords, and SSN, for example.
The first step in a dark web scan is to provide the data you want to check for leaks to a dark web scan tool. This data could be anything the scanner supports: some scanners can only check for your email address, but others can scan for your name, passwords, and SSN, for example.
Next, the dark web scanner checks your information against sources on the dark web, including:
- Dark web forums
- Dark websites
- Dark web chat groups
- Leaked credentials databases
- Data dumps
- Data broker websites
- People directory websites
On completing these checks, the dark web scan tool lets you know if it has found personally identifying information (PII). That’ll usually be indicative of a data leak or breach, meaning you should change any compromised information as soon as possible.
Who should use dark web scans and why?
Everyone who has ever signed up to use an internet service should perform a dark web scan.
A common misconception is to think that you don’t need a dark web scan if you’ve never been on the dark web. This would be the same as saying that you shouldn’t wear a “Made in Italy” hat since you haven’t been to the country.
Likewise, some internet users believe they don’t need a dark web scan since they’ve never signed up for shady online services. That would be wrong, since even legitimate brands get breached and have their user data end up on the dark web, as shown below:
| Year | Breached company | Leaked data | Affected accounts |
| 2024 | AT&T | Call and message logs, SSNs, passcodes | 73 million |
| 2024 | Change Healthcare | Health insurance data, SSNs, passport numbers, payment card information, banking information, and more | 100+ million |
| 2024 | Ticketmaster | Email, phone number, credit card information (encrypted), and more | 560 million |
| 2022 | DoorDash | Email address, name, credit card data (partial), and more | 360,000+ |
If you had an account with those companies around the time of the breach, chances are that your personal information is on the dark web.
What technology does dark web scanning use?
Dark web scan tools use a variety of technologies, depending on the depth of their service:
- Dark web crawlers and scrapers: Crawlers and scrapers automatically access thousands of dark web pages in search of specific data. They collect this information and report back when they’ve found matching PII.
- Database cross-referencing: Many scanners keep a database of confirmed leaks and breaches and check your data against it.
- Encryption: Dark web scanners must use robust encryption methods to prevent your data from falling into the wrong hands. Otherwise, a threat actor could simply breach a popular dark web scanning tool to obtain all the emails, passwords, and other data that users have submitted to it.
- AI and Machine Learning (ML) tools: Extensive dark web scanning tools use AI and ML models to better optimize their resources. This way, their crawlers and scrapers become more efficient at collecting relevant data, knowing where to look, generating fewer false positives, and improving the overall data scanning model.
The specific dark web scan tool you choose may use other types of technology. So, it’s best to research the tool extensively or speak with a customer support rep to understand how it generates results.
What are the limitations?
Dark web scans are indispensable to maintaining a clean online security profile, but they’re not without limitations. For example, a scan only checks for possible leaks at one point in time, and the results you get are only as reliable as where your preferred tool has checked.
Here’s a more detailed look at the limitations of a dark web scan:
- Instantaneous security snapshot: A dark web scan only shows possible leaks as of the time you ran the scan. Therefore, you wouldn’t know if there’s been a leak after that time until you run another scan.
- Limited coverage: The dark web is made up of hundreds of thousands of pages and is notoriously hard to navigate, so your scanning tool might not effectively check all sensitive parts of the dark web. This may give you a false sense of security if your data has leaked somewhere that the tool didn’t check.
- Dark website behavior: New dark websites come and go very often, so much so that it might be difficult to scan and monitor them all. For instance, a cybercriminal could set up a temporary site to sell some leaked data and take the domain down afterward. A dark web scan will miss such data dumps unless you scanned while they were active.
How does the dark web work?
The dark web is a secluded, hidden part of the internet that can only be accessed by special browsers, such as the Tor browser.
This part of the internet prioritizes anonymity above all else; not even user IP addresses are recorded. That’s why the dark web is a safe haven for legitimate users who want to transact or share information anonymously. However, that also makes it a prime spot for cybercriminals.
The dark web is not to be confused with the deep web, both of which are distinct from the surface web.
Surface web vs. deep web vs. dark web
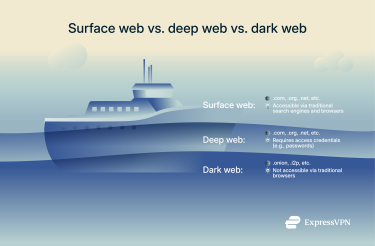 The biggest differences between the dark web, deep web, and surface web sites are how they can be accessed, how user-friendly they are, and how easy they are to find.
The biggest differences between the dark web, deep web, and surface web sites are how they can be accessed, how user-friendly they are, and how easy they are to find.
| Type/Criteria | Surface web | Deep web | Dark web |
| Access | Traditional browsers | Traditional browsers | Special browsers, e.g., Tor |
| Domains | .com, .org, .net, etc. | .com, .org, .net, etc. | .onion, .i2p, etc. |
| User-friendliness | High | High | Low |
| Search engines access | Yes | No | No |
In a nutshell, the surface web refers to the parts of the internet that you can access with your traditional web browser and via a traditional search engine. This includes the ExpressVPN website, which you can find on Google or access via your regular web browser.
The deep web is a layer beneath that, usually hidden behind a username and password or other access parameters. A good example is your Gmail account: your personal email contents aren’t indexed on the surface web and can only be accessed with your login credentials.
Finally, the dark web is hidden behind several layers of encryption, preventing access from traditional browsers. The encryption and masking technology used by the dark web also keeps it from being crawled by search engines like Google, explaining why dark websites won’t show up in your search results. Instead, you’ll need specialized browsers for access.
How data ends up on the dark web
Cybercriminals are often the source of PII ending up on the dark web. These groups or individuals may obtain user data from direct breaches or via social engineering attacks, such as phishing.
Likewise, some illegitimate data brokers may collect your data at different points, aggregate the data, and sell it on the dark web. This is why you should always use an internet privacy tool, like a reliable VPN, when surfing the web. That prevents data brokers from tracking you across the web and gathering sensitive data points to be sold on dark websites and forums.
Best free dark web scanners
Many dark web scan tools offer to help you check for personal data leaks at no cost. But you shouldn’t just blindly trust these tools, because:
- They may be out to get your data for themselves.
- Some tools don’t use strong enough encryption to protect your data against cybercriminals.
- Some tools generate false positives or negatives.
Considering these points, here are a few of the best free dark web scanners.
Mozilla Monitor
 Mozilla Firefox is a privacy-focused browser, so its addition of a dark web scan tool (called Monitor) is no surprise. There are a few things to like about Mozilla Monitor:
Mozilla Firefox is a privacy-focused browser, so its addition of a dark web scan tool (called Monitor) is no surprise. There are a few things to like about Mozilla Monitor:
- You can add and scan up to 5 email addresses.
- You get dark web monitoring (limited).
- You have to confirm ownership of emails, which ensures user privacy protection.
However, Mozilla Monitor only scans for your email address. Given that threat actors now collect and sell many other kinds of PII, including credit card details, driver’s licenses, passport numbers, SSNs, and much more, scanning only email addresses isn’t enough. For a free tool, though, it does okay.
Have I Been Pwned
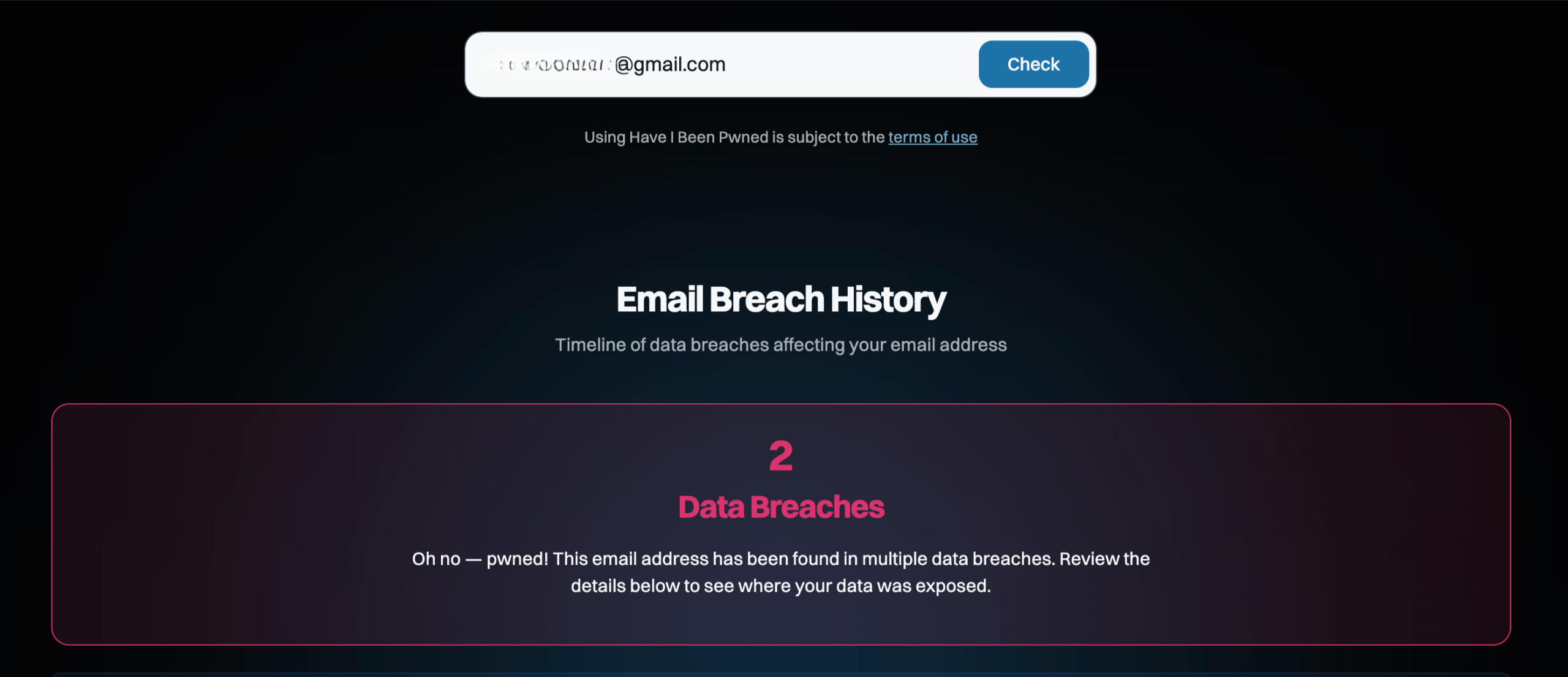 Have I Been Pwned allows you to check your emails and passwords for breaches. It’s good that it ensures no email or password entered into its search engine is stored on its servers. This means it can’t serve as a warehouse for sensitive data, making it less attractive to cybercriminals.
Have I Been Pwned allows you to check your emails and passwords for breaches. It’s good that it ensures no email or password entered into its search engine is stored on its servers. This means it can’t serve as a warehouse for sensitive data, making it less attractive to cybercriminals.
Likewise, the email and password searches are independent. That way, you don’t run the risk of pairing such sensitive datasets and increasing the damage a leak would do.
IDStrong
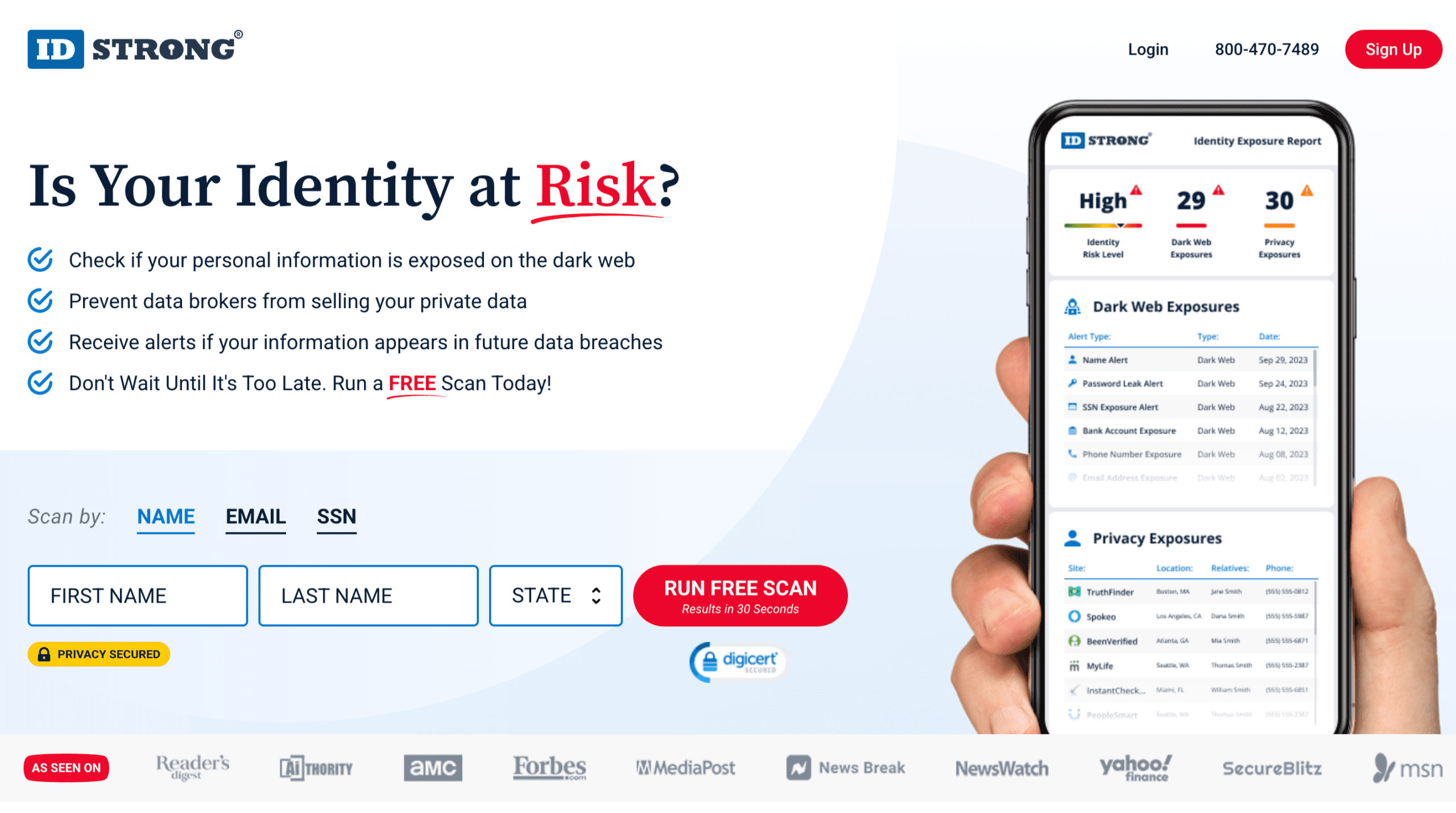 IDStrong offers a freemium service that checks for your email address, name, and SSN on dark websites, underground chat forums, public records, background check databases, black markets, social media, and more channels.
IDStrong offers a freemium service that checks for your email address, name, and SSN on dark websites, underground chat forums, public records, background check databases, black markets, social media, and more channels.
What to do if your information is found
If your information is found in a dark web scan, that doesn’t mean that it’s already been bought or used by a threat actor. After all, it could be from a recent hack or from a data dump that no one has purchased yet.
However, there’s no way to be sure of this. So, it’s best to act quickly to prevent or limit the damage from that data falling into the wrong hands.
Step 1: Change all compromised passwords
Reliable dark web scan tools will show you breached accounts associated with your scanned email addresses. Those that scan for passwords will also show you which of your passwords have been identified in a leak.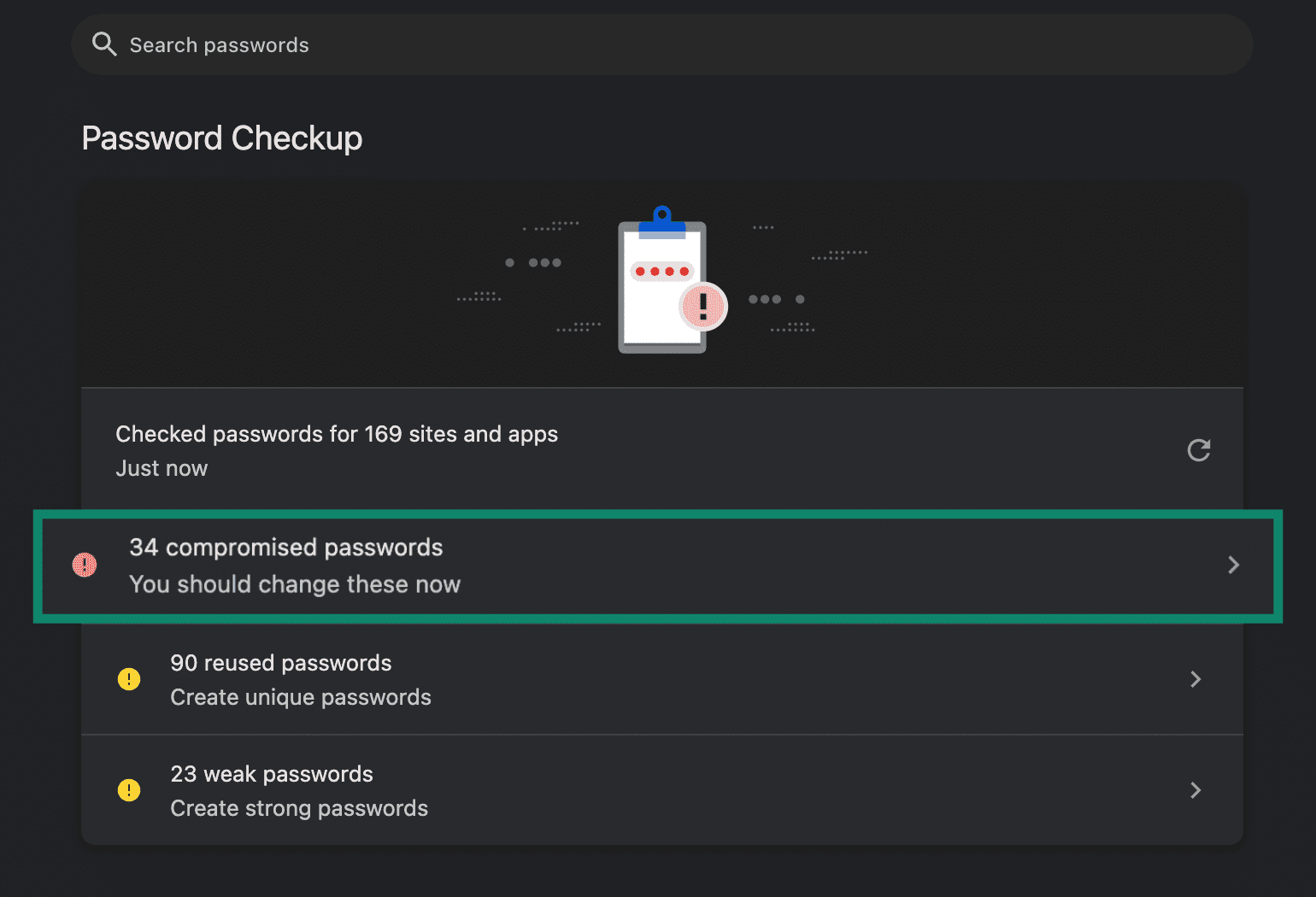 In such instances, change all compromised passwords immediately. We recommend generating a secure password and storing it in a password manager so you don’t have to worry about remembering it. ExpressVPN Keys is a good option; it generates and stores secure logins and can autofill them for you across your devices. This adds convenience on top of reliable password security.
In such instances, change all compromised passwords immediately. We recommend generating a secure password and storing it in a password manager so you don’t have to worry about remembering it. ExpressVPN Keys is a good option; it generates and stores secure logins and can autofill them for you across your devices. This adds convenience on top of reliable password security.
Finally, enable multi-factor authentication (MFA) on your account. That way, even if a threat actor has your password, they still won’t gain access to your account without the second authentication factor.
Step 2: Alert financial institutions
This is crucial if your financial information (such as your SSN, credit card details, account number, etc.) shows up in a dark web scan. After all, a scammer could use your SSN to open new accounts or even take out loans in your name.
When you inform your financial institutions of the data leak, they’ll advise you on what to do next to ensure no damage is done, or at least no further damage.
Step 3: Monitor and/or freeze your credit
If your SSN or other financial info has been breached, monitoring and freezing your credit can preserve your finances. This way, the cybercriminal is unable to open a new line of credit, take out loans, or make other financial commitments in your name.
The process to do this will depend on your credit reporting agency. U.S. customers can also use services like ExpressVPN Credit Scanner to monitor their credit 24/7, get alerts on suspicious activity, and access actionable insights.
Step 4: Report to the authorities
File a report with local law enforcement and other relevant offices, such as the FBI Internet Crime Complaint Center (IC3) if sensitive information like your SSN, passport, or driver’s license information has been leaked.
Step 5: Set up ongoing monitoring
You can’t rely on one-off dark web scans to uncover all new threats. Plus, depending on the sensitivity of the leaked data, it might already be too late when you remember to scan. This is where ongoing dark web monitoring comes in.
ExpressVPN’s Identity Defender offers monitoring tools for ExpressVPN users in the US. These include ID Alerts, which constantly scans the dark web for your personal info, as well as alerting you to potential misuse of your SSN and unauthorized address changes.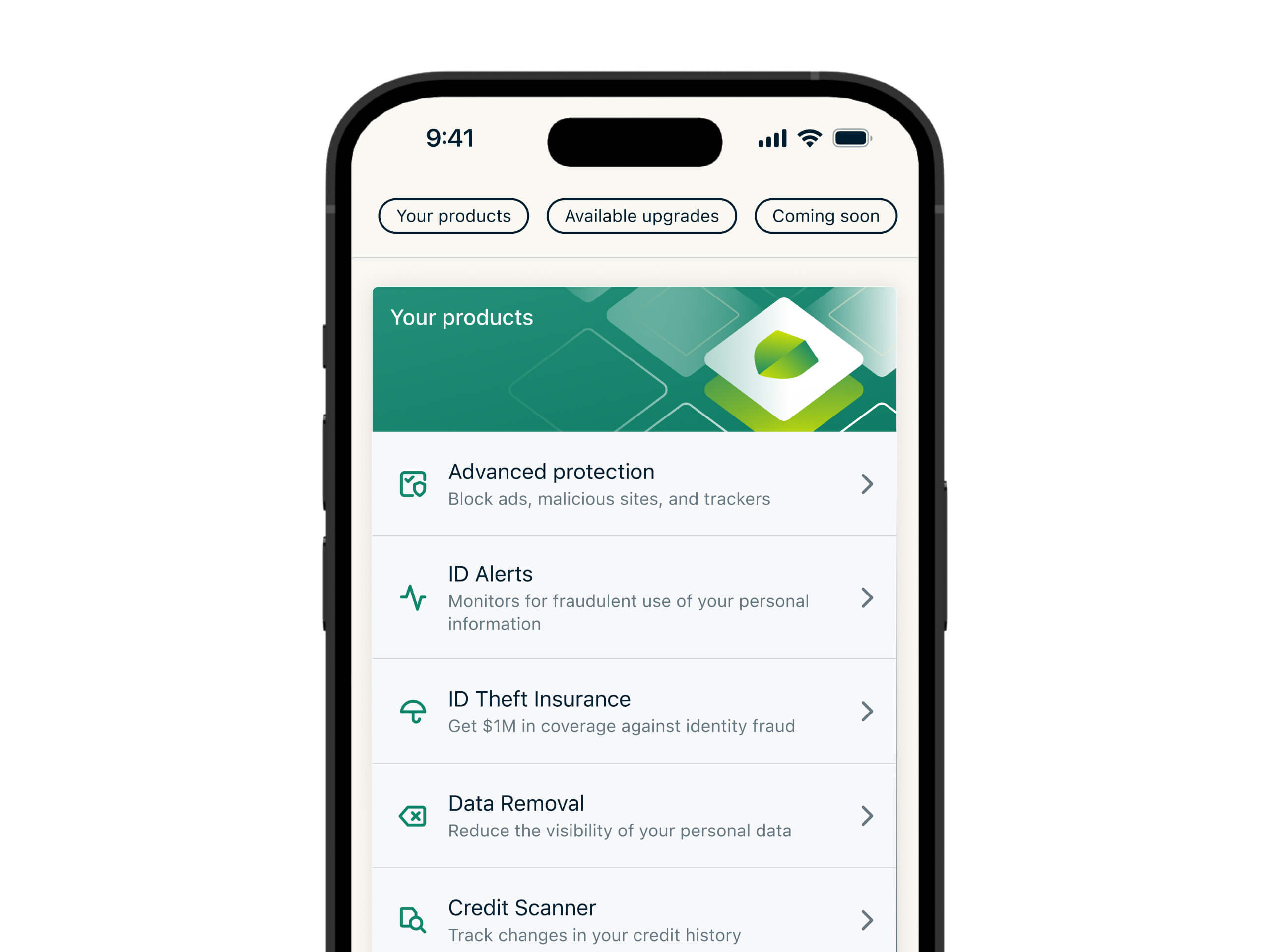 Monitoring your data removes the manual constraint, ensuring you’re alerted to any data breach as soon as it happens. That way, you can get on top of things faster. Read on for a comprehensive explanation of how dark web scans compare to breach monitoring.
Monitoring your data removes the manual constraint, ensuring you’re alerted to any data breach as soon as it happens. That way, you can get on top of things faster. Read on for a comprehensive explanation of how dark web scans compare to breach monitoring.
Step 6: Check app permissions and limit the info you share
Some apps request access to more data than they need. For example, a photo editing app might request access to your contacts or email application. Make sure you only grant permissions that are relevant to the service provided.
It’s also important to avoid shady apps altogether, as they might include malware that can access sensitive data on your device. Stick to downloading apps from the official Google and Apple stores, and always check reviews and ratings.
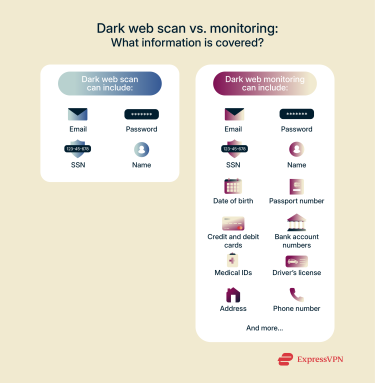
Dark web scanning vs. monitoring: What’s the difference?
Dark web scanning and dark web monitoring services have one thing in common: they check the dark web for PII and notify you when they find any. However, they differ in how they offer this service.
| Scanning | Monitoring | |
| Scanned data | Limited | Comprehensive |
| Checks | Instantaneous | Ongoing |
| Price | Free or Freemium | Premium |
| Coverage | Limited | High |
What does dark web scanning do?
Dark web scans check some dark websites and databases (such as data dumps) for information you feed into the scanning tool. Reliable tools will return matches for any compromised account information on the dark web.
However, dark web scans are often limited to checking email addresses alone. The more generous tools also scan for your passwords, SSN, and name.
Dark web monitoring: Ongoing protection explained
Dark web monitoring improves on dark web scans by constantly checking scraped dark web data against your personal information. This means that dark web monitors don’t only check at the time you entered your information but at every other time after that.
These ongoing checks make dark web monitoring tools better at detecting data breaches and leaks the instant they happen. By so doing, they promise you a better security profile, since you can address breaches and leaks immediately.
Furthermore, dark web monitoring tools often cover a lot more personal data than dark web scans, including:
- Name
- Passport number
- Credit card details
- Local bank account numbers
- International bank account numbers
- Tax ID
- SSN
- Health insurance details
- Driver’s license
- Address
- Phone number
- …and more
Likewise, the constant scanning model means that dark web monitoring tools can catch new dark websites set up to sell user information before they’re taken down. A simple scan will miss such sites if you don’t scan when they’re active.
Dark web monitoring tools are also often better suited for in-depth searches of the dark, deep, and surface web, including dark web chat rooms, people search websites, dark web forums, and background check databases.
Comprehensive dark web monitoring tools often come at a price. Some tools are free, like the Mozilla Monitor, but they’re limited in the scope of what they can monitor. You may get only email address monitoring, for example, which doesn’t cover your personal data threat landscape.
Fully fledged monitoring tools like ExpressVPN’s Identity Defender (available for U.S. users) bring more functionality to the table. As well as in-depth dark web monitoring, it can remove your personal information from data brokers, provide you with identity theft insurance*, and monitor your credit activity.
Dark web scan or monitoring: Which should you choose?
 Dark web monitoring is a better option than dark web scans. You can set up and forget the dark web monitoring tool, as it’ll send you alerts if anything pops up. However, you have to constantly be on alert and remember to schedule individual dark web scans.
Dark web monitoring is a better option than dark web scans. You can set up and forget the dark web monitoring tool, as it’ll send you alerts if anything pops up. However, you have to constantly be on alert and remember to schedule individual dark web scans.
Furthermore, dark web scanners are often limited in scope, only covering a few personal data types. And some rely on database comparisons alone, checking data breaches that have already been made public, rather than searching for actively trading data.
What can cybercriminals do with your data?
Your name or email address alone might be insufficient for a cybercriminal to do anything nefarious. Once they piece together enough personal information about you, though, you could become a victim of identity theft, credit card fraud, account takeovers, and more.
Identity theft
Financial institutions, banks, and businesses rely on your personal information to identify you and grant certain access. They operate on the belief that you should be the only one with access to certain personal information.
So, if a cybercriminal were to get enough personal information about you, they could use these stolen credentials to:
- Call your bank and make transfers or take loans
- Claim your government grants, apply for government support, or collect your benefits
- Order from a business, cancel a large shipment, or redirect important purchases
- Open new tax accounts or file fraudulent tax refunds
Credential stuffing and account takeover
Credential stuffing occurs when cybercriminals try login details found in one breach across other accounts. For instance, a cybercriminal with breached login email and password data from an e-commerce website can try the same details on an online banking platform.
Of course, the threat actor might not know what other online accounts you own. Still, that doesn’t stop them from guessing other services you use (such as popular financial, travel, social media, and health services) and trying their luck with the stolen login credentials.
This attack works since some users like to reuse passwords across multiple online accounts. You can avoid this risk by using a trustworthy password manager like ExpressVPN Keys to generate and store unique passwords for all your accounts.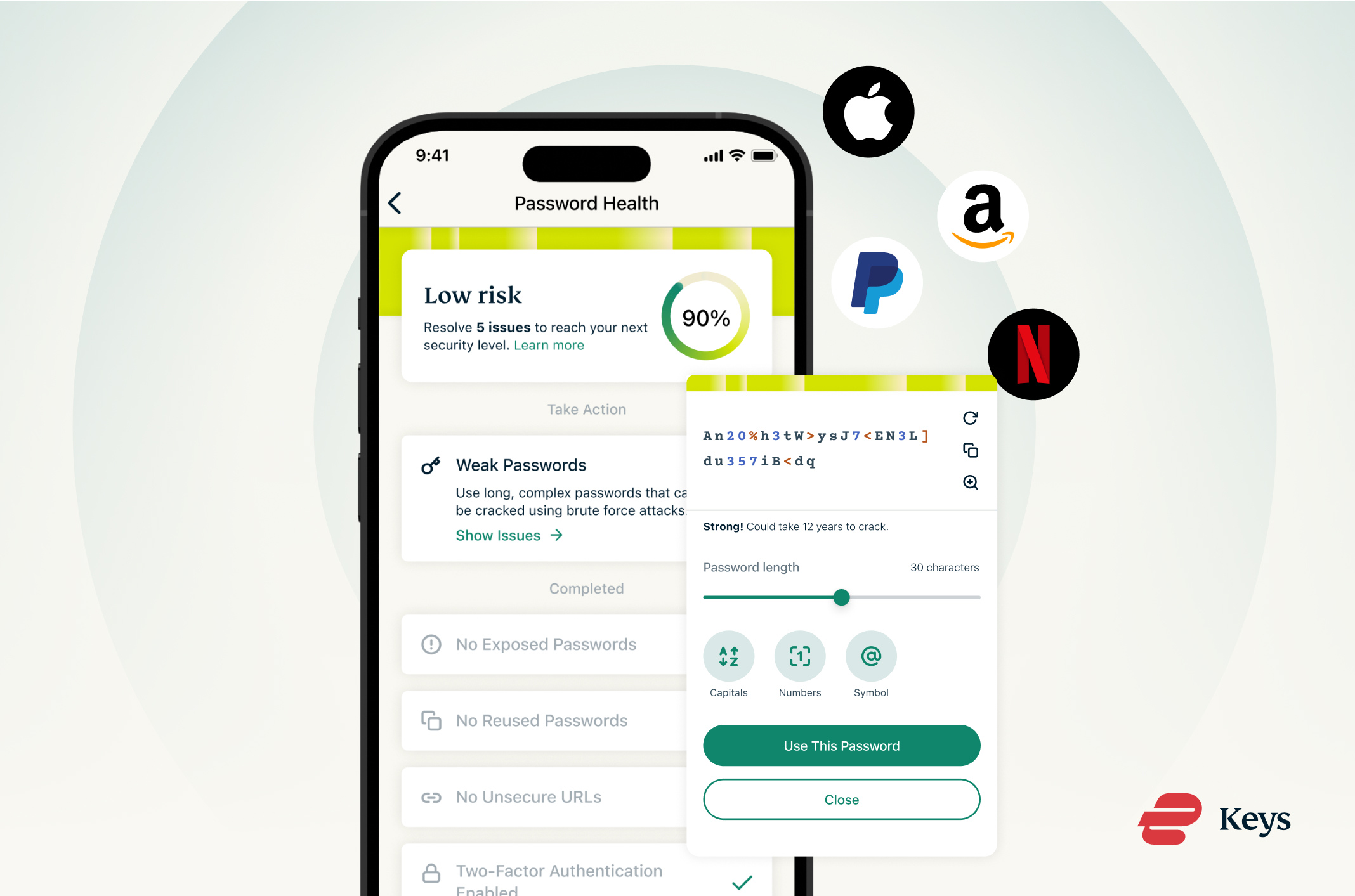
Credit card fraud
A cybercriminal with your credit card details can use them to:
- Fund a vacation.
- Make large online purchases.
- Pay for fraudulent, self-generated invoices.
You may be left with the credit card debt if you’re unable to prove that it’s fraud. Even if you’re able to prove it, the incident could impact your credit score, which might affect your access to credit facilities in the future.
You can use the ExpressVPN Credit Scanner, which is included in select ExpressVPN plans for U.S. customers, to monitor your credit activity and spot unauthorized personal information usage. The tool also offers actionable information to freeze your credit fast if you notice strange activity.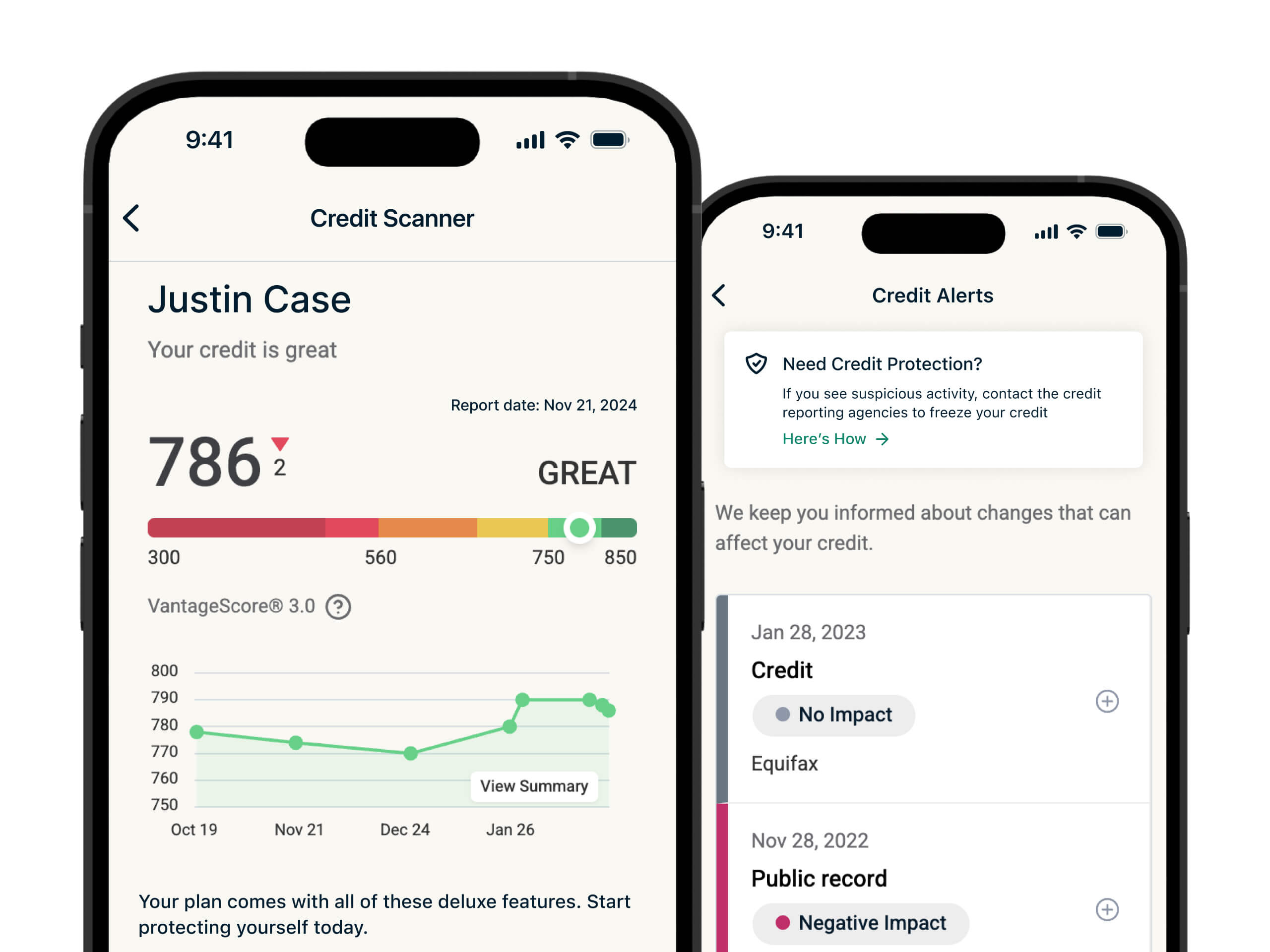
Robocall and phishing campaigns
Has your contact information (email and phone number) leaked on the dark web? Unscrupulous advertisers may purchase such information to start bombarding you with robocalls.
Scammers also love such lists, since they allow them to send out mass phishing campaigns to unsuspecting users. They play a numbers game here: if they send out the same phishing email to 100,000 users and 1% of recipients click the link, it’s still a win for them.
Blackmail and extortion
 In 2015, Ashley Madison (an online dating service for married people) suffered a database breach. Cybercriminals copied thousands of users’ data and promised to leak that information if the website and its parent company didn’t shut down operations.
In 2015, Ashley Madison (an online dating service for married people) suffered a database breach. Cybercriminals copied thousands of users’ data and promised to leak that information if the website and its parent company didn’t shut down operations.
The company refused, and the threat actors released 2,500 items of PII to cement their claims. This is an example of how such leaks can be used for blackmail.
But how about extortion?
When Ashley Madison still wouldn’t comply, over 70GB of personal information stolen from the dating website was released on the dark web.
Then, dark web users started combing through the information to find notable names and email addresses. In this quest, some of the users targeted email addresses from countries where adultery was a severe offense with an extortion scam: pay us to keep silent, or we expose you to your government.
That’s just one example, but it shows the lengths to which cybercriminals and other unscrupulous dark web users will go to benefit from personal data leaks.
FAQ: Common questions about dark web scans
How do I scan the dark web for stolen information?
You can use dedicated dark web scanning tools like Have I Been Pwned and IDStrong to scan the dark web for email leaks, password data, and other stolen credentials. You just need to enter the information you want to scan into your preferred tool, and it’ll check dark websites, forums, data dumps, and databases for matches.
Is dark web scanning safe and private?
Dark web scanning is safe and private if you use reliable tools. Otherwise, a dark web scan tool might store your personally identifiable information (PII) in an unsafe format, leaving it susceptible to hacks and leaks. Likewise, you might unknowingly divulge your personal information to a disreputable dark web scanner designed to collect and steal user information.
How accurate are dark web scans?
Dark web scans are only as accurate as the sources they check. Some dark web scanners only check data dumps and leak databases. Other dark web scan tools may look deeper into private chat forums, crawl new dark websites, and check active discussion boards where data leaks are published.
Do dark web scans cover the entire dark web?
Dark web scans do not often cover the entire dark web, due to the sheer size of the dark web and the resources that would be required for such an extensive scan. Instead, most dark web scans focus on leak databases and known data dumps.
How often should I scan for personal data leaks?
It’s best to schedule dark web scans as often as possible. Leaving too much time between scans can be dangerous, as threat actors may have already breached and acted on your information in the meantime. Alternatively, set up dark web monitoring for automatic ongoing checks so you don’t have to rely on individual dark web scans.
Is dark web monitoring free or paid?
Dark web monitoring is often a paid service, as it requires more resources than a dark web scan. Dark web monitoring ensures ongoing coverage and often covers more of the dark web than ordinary scans. You also get the added advantage of getting notified the instant a leak is noticed, improving your reaction time and mitigating damage effectively.
Are dark web scans worth paying for?
Dark web scans are often not worth paying for, as they usually only check a handful of personal identifying information against known data dumps and breach databases. However, dark web monitoring is worth paying for, especially for its automated nature and coverage of extensive personal data types.
How to start a free dark web scan?
You can start a free dark web scan by entering your details in tools like Have I Been Pwned, IDStrong, or Mozilla Monitor. Some of these tools restrict the data you can scan for free to your email address; this is a popular entry point for cybercriminals and spammers. However, some tools may also allow you to scan your Social Security number (SSN), first name, last name, and passwords for free.
When should I use a dark web scanner?
The best time to use a dark web scanner is right now. After all, your accounts might have already been compromised. You should also scan immediately if you notice any strange activity in your accounts, helping you to confirm or rule out a breach.
Finally, scan the dark web after applying for jobs, renting a new place, or making a purchase where you were required to submit sensitive information. That way, you can rest assured that the other party handled your data carefully.
*The insurance is underwritten and administered by American Bankers Insurance Company of Florida, an Assurant company, under group or blanket policies issued to Array US Inc, or its respective affiliates for the benefit of its Members. Please refer to the actual policies for terms, conditions, and exclusions of coverage. Coverage may not be available in all jurisdictions. Review the Summary of Benefits.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN




![[Quiz] How much is your data worth on the dark web?](/wp-ws-cache/uploads-expressvpn/2023/04/how-much-are-you-worth-on-the-dark-web-1-1-640x423.jpg)