There’s a reason encryption was once officially classified as munitions under U.S. law. Though commonly used to defend against cyberattacks, encryption can also be an extremely powerful offensive weapon, most notably in the form of ransomware.
What is ransomware?
As its name implies, ransomware takes a person’s files for ransom. The attacker locks the victim’s device or network and demands payment in order to unlock it. Ransomware is especially damaging for companies and large organizations, which often become unable to operate without access to their documents and systems.
Ransomware is increasingly common thanks to ransomware marketplaces that sell ransomware-as-a-service (RaaS) to less tech-savvy criminals. In other words, you don’t have to be a skilled hacker to execute a ransomware attack, as long as you’re willing to share profits with someone who is. This was the case in the infamous Colonial Pipeline attack that forced a shutdown of a 5,500-mile oil pipeline.
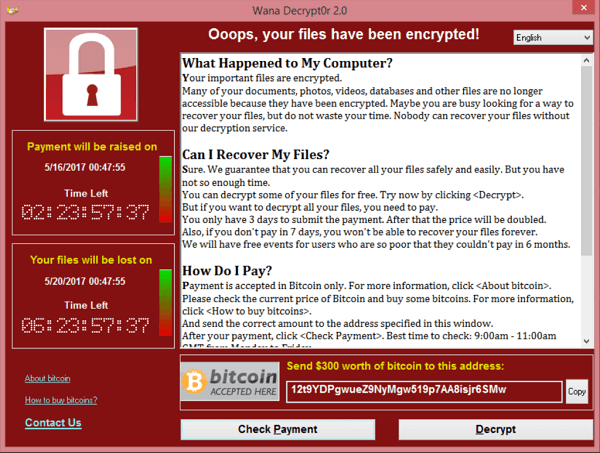
How does ransomware work?
Ransomware can infect a system in a variety of ways. It can be accidentally installed by the user—smuggled inside another piece of malware, or downloaded from a link in a phishing email—or, more rarely, it can be injected by the attacker directly through vulnerabilities in the network or device.
Once inside a system, ransomware will search for important files like photos, documents, or whole databases, and encrypt them with a public key generated specifically for that attack. Only the attacker holds the private key needed to decrypt the files.
Victims then see a lock screen—the digital equivalent of a ransom note—explaining their predicament, with instructions on how to pay a ransom to their attacker in exchange for the decryption key (basically a pass code). Attackers almost always ask for payment in a cryptocurrency that makes it very difficult for law enforcement to track them down afterwards.
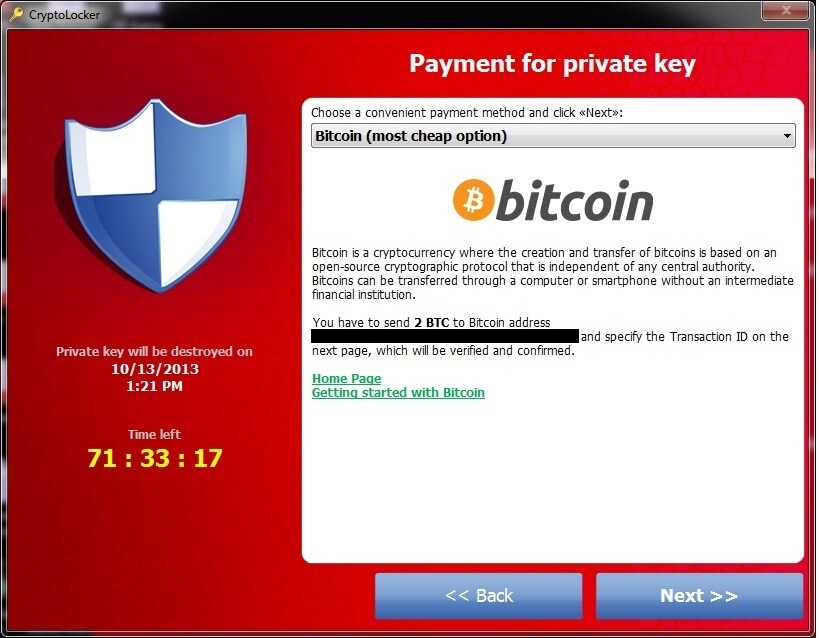
Types of ransomware: encryption vs. lock screen
Not all ransomware uses encryption. Some merely confront victims with a lock screen but don’t bother encrypting any files. This type of malware is relatively easy to remove by rebooting your device in “Safe Mode” (or similar) and uninstalling it.
Many victims of ransomware aren’t savvy enough to know whether their files have actually been encrypted. Often, attackers will put pornographic images on the lock screen and/or accuse victims of illegal activity in order to discourage them from seeking expert help. One famous example of this was WinLock, a Russian scheme in early 2010 that locked tens of thousands of victims out of their Windows desktops until they sent an expensive paid SMS, reportedly earning the attackers a total of 16 million USD.
In one ironic incident in 2013, a man received a ransomware note claiming he was under investigation by the FBI for child pornography. When he brought his infected computer to a police station to dispute the claim, police searched his computer, found actual child pornography, and arrested the man. Only later did they realize the original accusation was a virus rather than a real ransomware message.
Most victims of ransomware, however, are innocent. In fact, ransomware can prove disastrous even to people with no relationship to the infected machines. In 2020, a 78-year-old woman in Germany died after ransomware shut down emergency rooms at a hospital that might otherwise have saved her life.
Read more: Why hospitals are getting more cyberattacks
Should you pay the ransom?
Companies might want to pay the ransom not only to quickly resume their normal operations but also to avoid bad publicity surrounding their attack. Sometimes victims negotiate the ransom with attackers.
Advice varies, but the prevailing wisdom is to not pay the ransom, partly because there is no guarantee that you will ever receive the promised decryption key, and partly because it encourages the proliferation of more ransomware—both for you and for other potential victims. Moreover, even if you pay, the attackers could still sell the data they receive, adding insult to injury.
Another reason not to pay is you can attempt to remove the ransomware (more below).
Ransomware removal: How to fix ransomware
Removing ransomware is tricky. If your files are indeed encrypted with a unique public-private key pair, it is probably not possible to restore them.
However, there are still important steps you can take that may mitigate the damage:
- The first thing to do is isolate your infected device. Malware is often designed to spread to other devices via network connections, and ransomware is no exception. Remove any physically connected drives from your device, disable any wireless connections (bluetooth pairings, for example), and disconnect the device from your Wi-Fi network (you can also do this from your router settings).
- If the infected device was issued by your company, contact the IT department immediately. In fact, it’s a good idea to do so even for personal devices as there may still have been some contact between them.
- Identify the type of ransomware. You may need professional help, but this step will likely determine whether your data can be salvaged. Use another device to Google the instructions on the lock screen for help identifying the attack.
- Remove the malware. This step will depend on the type of ransomware and what kind of device was infected. In the best case scenario, you may be able to remove the program before it is finished encrypting your files. In many cases, however, there is nothing to be done. Ransomware often deletes itself after encrypting your files, to avoid leaving incriminating evidence.
- Recover your files. Again, this may not be possible depending on the encryption. Some cases of ransomware, however, have been known to use a common decryption key which may be reapplied in your case. You can find these keys and other mitigation steps by searching the name of the ransomware after you’ve identified it.
Even if there is no hope of decrypting your files, you may still be able to find old versions of them. Use another device to check your cloud storage, external hard drives, or even your email archive for specific files you may have lost in the attack.
No More Ransom is an excellent resource for victims of ransomware. You can use it to identify your attack and find decryption tools, if they are known.
How do you prevent ransomware attacks?
“An ounce of prevention is worth a pound of cure” is especially good advice when it comes to ransomware. Here are a few precautionary measures that could save you from major headaches in the future:
- Back up your files regularly, either to an external disk or to secure cloud storage. Better yet, make those backups automatic. So even if you are attacked, you can afford to give up your device and everything on it.
- Avoid suspicious links and email attachments, especially from people you don’t know. Even people you do know may have been infected themselves, so stay vigilant and trust your instincts if a message seems out of character.
- Companies need to invest in robust cybersecurity, including training their staff to stay clear of phishing emails.

Protect your privacy with the best VPN
30-day money-back guarantee



























Comments
i highly recommend you must read this you can defined what is the truly meaning of RANSOMEWARE take extra careful every piece you do my sister hospital was a victim of ransomeware but they will not give a bitcoin the hospital said they will find a way to put them in jail. And now the patients in the hospital all there records were lost will be back only if they going pay its hard to be a victim of these cybercriminals.. always keep lookout! Today i gave learned always keep your files backup that’s right Folks to be SAFE AND COVER ALL FILES.. have a nice day bye..