Tor (originally called The Onion Router because it layers your traffic like an onion) is generally considered safe to use. The free network of servers, or “nodes,” can significantly increase a user’s privacy and anonymity online. In internal documents, the NSA has even referred to Tor as “the king of high-secure, low-latency internet anonymity.”
In this guide, we will explain how the Tor browser works, how you can make use of it and contribute to it, and the many other little things Tor enables us to do online.
Jump to…
What is Tor?
Is Tor safe?
What is Tor Browser?
How the Tor browser works
What is the Tor browser used for?
Pros and cons of using the Tor browser
How to use the Tor browser
How to stay safe while using the Tor browser
How to contribute to Tor
Alternatives to the Tor browser
Bonus: The unlikely history of Tor
What is Tor?
Tor, short for “The Onion Router” is a free, open-source software that enables anonymous communication over the internet. Similar to a VPN, you can use Tor to hide your IP address and anonymize your internet traffic. This is because Tor directs internet traffic through a worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis. This makes it difficult for anyone to track your internet activity or determine your physical location.
Tor provides access to the dark web—a part of the internet that is not accessible using normal browsers. It is often viewed negatively by the press and law enforcement agencies, due to its use to conduct illegal activity, but it has many positive benefits. Journalists and their sources rely on it to communicate securely and anonymously, without fear of government monitoring. Secure communication is essential in whistleblowing cases, providing anonymity to people “on the inside. Similarly, Tor is important for law enforcement as it allows for covert operations and investigations online. Tor currently has about two million daily users worldwide, most of them originating from the United States, Germany, and Russia.
Is it safe to use Tor?
Yes, from a privacy standpoint, Tor is safe because it anonymizes your internet activity and hides your location. This is done by routing your data through multiple servers around the world, making it hard to trace back to you. The Tor Browser and Tails (an operating system that prioritizes privacy and anonymity) are both set up to use the Tor network right from the start, which helps prevent accidental leaks of your personal information.
However, the content on the dark web can be seen as dangerous, filled with scams and marketplaces selling illegal goods. Users can also be tricked into downloading malware or revealing information about themselves.
What is Tor Browser?
Tor Browser is a web browser specifically designed for you to access the dark web or use the Tor network. The browser looks and feels like Firefox, but comes optimized for security and privacy. It has the NoScript extensions pre-installed to protect you from malicious Flash or Javascript exploits.
Here’s what else sets it apart:
- Anonymity: Tor Browser routes your web traffic through the Tor network, making it difficult to trace your internet activity back to you. This helps protect your personal privacy and freedom.
- Access to dark web: The Tor browser allows access to .onion websites, which are part of the dark web and not indexed by regular search engines.
- No tracking: It doesn’t track your browsing history and clears your cookies after each session.
- Blocks trackers: The browser automatically blocks many third-party trackers and ads that can follow you across websites.
- Fingerprint resistance: It makes all Tor browser users look identical, which makes it more challenging for you to be fingerprinted based on your browser and device information.
- Free and open source: It’s freely available for anyone to use or modify.
It’s important to note, however, that the Tor browser will not anonymize all your web traffic. This is why it is commonly run alongside a VPN. More on this below.
How the Tor browser works
Imagine the internet as a postal system. If you want to buy a book, you send a postcard to a publisher. The downside? Everyone who handles your postcard knows what you’re reading. This is similar to how the internet works—your online requests can be tracked.
To keep your request private, you could think of using a sealed envelope, representing encryption. It hides what’s inside (your online request) but still shows where it’s going and where it’s from (metadata). This is like basic encryption on the internet, indicated by a lock icon in your browser.
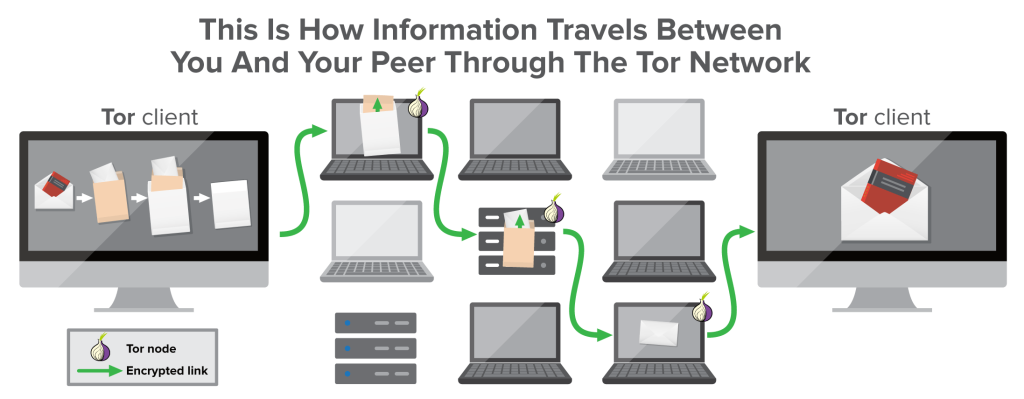
Tor’s layered security: nodes
Tor Browser takes privacy further. When you send a request, it goes through a chain of three randomly chosen nodes (servers) before reaching the destination:
- An entry node can see who you are, but not what you request or who you request it from.
- A middle node cannot see anything. It is important because it separates the exit and entry nodes from each other.
- An exit node can only see what you request, but not who you are.
What is the Tor browser used for?
Because Tor Browser allows you to browse the internet without revealing your identity or location, it’s primarily used for enhancing online privacy and security.
Here are a few examples of what Tor Browser is commonly used for:
- Anonymous browsing: It’s ideal for those who want to keep their internet activities private. Whether you’re a journalist, activist, or just a privacy-conscious individual, Tor Browser ensures that your browsing habits and location remain anonymous.
- Accessing restricted content: In countries where the internet is heavily censored, Tor Browser can bypass these restrictions. This allows users to access blocked websites and information freely.
- Secure communication: For whistleblowers or individuals needing to communicate sensitive information securely, Tor provides a platform where they can share data without the risk of being traced.
- Researching sensitive topics: Researchers or individuals exploring sensitive or controversial topics can use Tor to protect themselves from surveillance and potential backlash.
- eCommerce and cryptocurrency transactions: Some use Tor for more secure online transactions, especially when dealing with cryptocurrencies or when anonymity is a priority.
- Accessing the dark web: Tor is the gateway to the dark web, a part of the internet not indexed by traditional search engines. It’s used for both legitimate and illicit activities, ranging from free speech forums to marketplaces for illegal goods.
Pros and cons of using the Tor browser
While Tor Browser provides enhanced privacy, it’s not infallible. Here are some of its advantages and disadvantages:
| Pros of using Tor Browser | Cons of using Tor Browser |
| Enhanced privacy: Keeps your browsing private, protecting your identity and location. | Slower speed: Due to traffic being routed through multiple nodes, browsing can be slower. |
| Access to restricted content: Bypasses censorship and allows access to blocked websites. | Limited anonymity: The Tor browser will not anonymize all your web traffic, which is why it is commonly run alongside a VPN. More on this below. |
| Free and open source: Tor is free to use and its source code is open for review, enhancing trust. | Complexity for average users: Can be less user-friendly compared to mainstream browsers. |
| Improves security: Provides an extra layer of security, especially on public Wi-Fi networks. | Misuse concerns: Sometimes associated with illegal activities due to the anonymity it offers. |
| Dark web access: Enables access to .onion sites, which are not indexed by standard search engines. | Limited plugin use: To ensure privacy, the use of plugins and extensions is restricted, which can limit functionality. |
| Useful for sensitive research: Ideal for journalists, activists, and researchers working on sensitive topics. | Website compatibility issue: Some websites may not work properly or block Tor users. |
Accessing .onion sites through Tor Browser
Another potential downside of using Tor can be the risk associated with malicious exit nodes. These nodes, managed by volunteers, become a point of vulnerability if the end site lacks robust encryption, potentially exposing your data to viewing or alteration. However, this risk can be mitigated by using .onion addresses within the Tor browser, which don’t require exit nodes.
.onion domains, distinct and not part of the regular DNS, offer mutual anonymity for both the user and the site. Numerous well-known websites offer .onion versions; for instance, Facebook’s is facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion. These addresses are also useful for bypassing strict network firewalls.
Read more: What is an .onion address on Tor, and how to get one
How to use Tor browser
The Tor Browser is easy to run. In fact, it doesn’t require any installation at all and you can just run the .exe or .dmg files directly from your USB stick. This makes it possible to bring the browser into an environment where you cannot install software, such as your school or office.
1. Download the Tor Browser
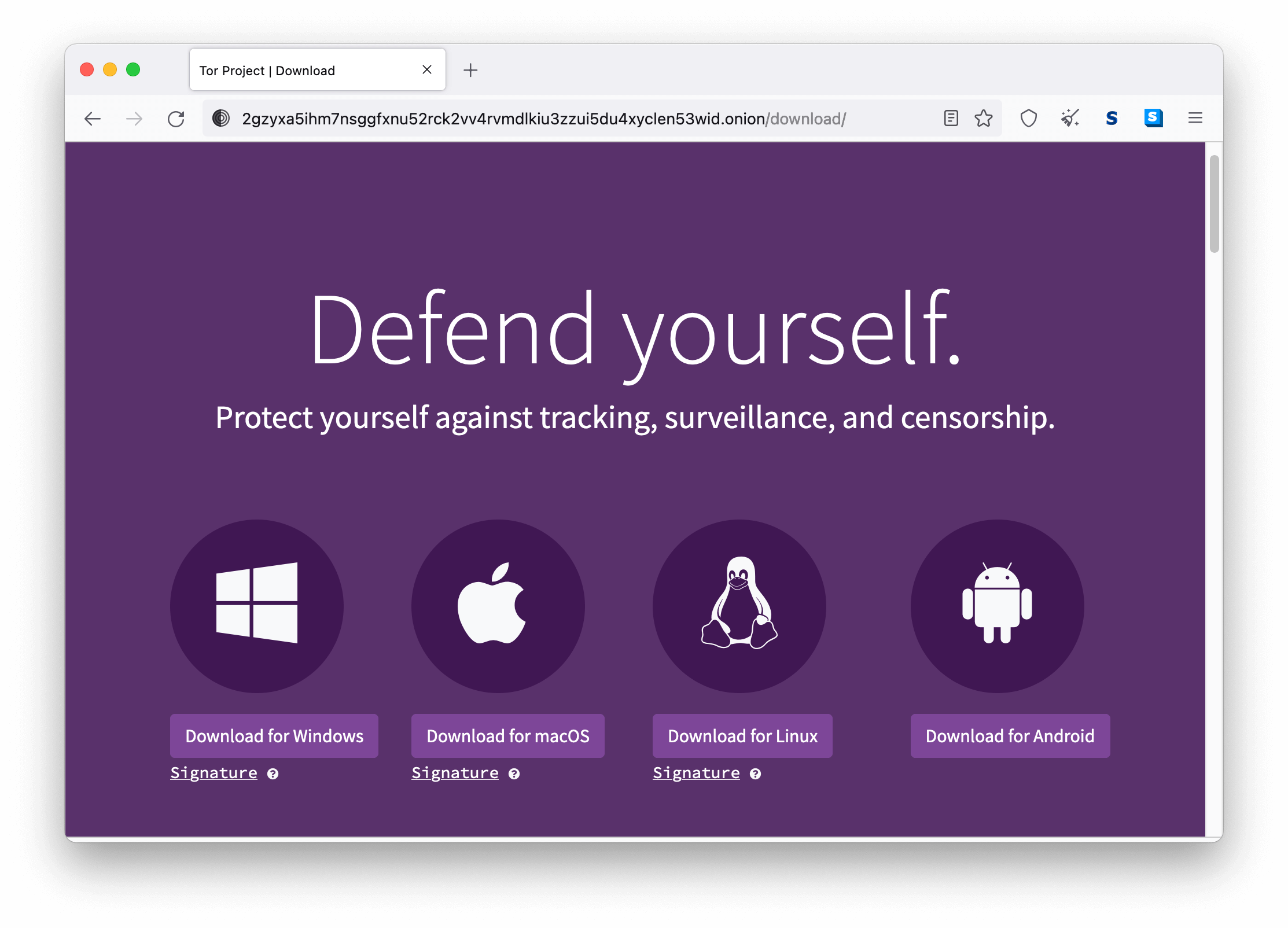
The Tor Browser is available for Windows, Mac, Linux, and Android.
Download the file and save it. Installation is quick and easy.
In Windows, double-click the .exe file and select a destination folder. This can also be a USB stick.
In Mac OS X, you have to double-click the .dmg file and drag the containing file into a separate folder, such as the application folder or USB stick.
In Linux, you have to unpack the .tar.xz file with the command below.
tar -czvf tor-browser-linux64-[…].tar.xz
On Android, you can install the app from the Google Play store or download one of several APK files from the website.
2. Start the Tor Browser
When you start the Tor Browser for the first time, you will be asked how you want to connect. If you are unsure if your network requires further configuration (mostly it doesn’t), click on continue. Otherwise, click on “configure” and answer the questions.
Pro Tip: If Tor does not connect, or if you do not want your ISP to know you are using Tor, connect to your VPN first, then open the Tor Browser.
3. Browse the web anonymously
Congratulations, you are now using Tor! You can now browse the internet anonymously. To make full use of Tor’s security features, have a look at their FAQ.
Tor Browser for Android
Android is now officially supported by the Tor Project, with multiple APK files available for download on the Tor Browser website.
Tor Browser for iOS
Tor is not officially available on iOS devices, but the Tor Project recommends iPhone and iPad users use the Onion Browser instead. Some apps, such as the Zap Bitcoin wallet also come with Tor capabilities included.
Tor Browser for Mac, Windows, and Linux
The Tor Project’s website also hosts the latest builds of Tor Browser for Mac, Windows, and Linux, along with updated release announcements, download instructions, and a guide to verifying digital signatures.
Tor Browser for Tails
Tails (The Amnesic Incognito Live System) is an operating system based on Linux that you can run from a DVD or USB stick. It comes pre-installed with the most important encryption software, like Pretty Good Privacy (PGP) and OTR. It will route all your traffic through the Tor network by default. This makes it far easier to remain truly anonymous, and it also mitigates threats of bugs or attacks.
You can easily carry it with you and it does not need to be installed on the computer you are running. Tails lets you safely and easily maintain a separate identity on your own computer or a public device.
How to stay safe while using the Tor browser
Cyber threats like surveillance, tracking, and malicious software can still pose risks when you’re using Tor Browser—especially on less secure or unregulated parts of the internet. By adopting safety practices, you can safeguard against these risks, ensuring your browsing remains private and secure.
- Keep Tor updated: Regularly update the Tor Browser to the latest version for security patches and improvements.
- Practice safe browsing: Avoid installing plugins or add-ons as they might connect to servers outside of Tor, compromising your IP address and browsing history.
- Always check for HTTPS: Ensure you’re connecting to websites using HTTPS. Traffic through exit nodes can be monitored if the destination site isn’t secured with an HTTPS lock.
- Avoid personal information: Don’t share personal details such as your real name, address, or phone number.
- Limit downloading files: Be cautious when downloading files, as they can contain malware or compromise your anonymity when opened. Even PDFs and Word documents might contain little snippets of code that could reveal your personal Internet protocol (IP) address.
- Be mindful of your digital footprint: Remember that heavy traffic on the Tor network, like running a popular dark web site, might make you more identifiable.
- Avoid torrenting over Tor: It’s not recommended to torrent through the Tor network. Modern BitTorrent clients use UDP as a protocol, which does not work over Tor. As a result, your data will either not be transmitted at all or transmitted outside of Tor, revealing your IP address in the process.
- Disable JavaScript (if feasible): Consider disabling JavaScript to prevent revealing your real IP address, though this may affect website functionality.
- Be cautious with .onion links: Only visit trusted .onion sites, as others may host harmful content.
- Avoid opening documents downloaded through Tor while online: Opening documents externally can reveal your real IP address.
- Utilize NoScript: Utilize NoScript and other secure extensions included in Tor to manage what runs on your browser.
- Be mindful of cookies and history: Tor Browser deletes cookies and history upon startup, but be cautious about triggering compromising cookies during your session.
Use a VPN when connecting to Tor Browser
Using a VPN in combination with Tor can significantly enhance your online privacy and security. When you use Tor, your internet service provider can see that you are using Tor. A VPN encrypts your internet traffic, hiding it from your internet service provider and other local snoopers. Tor, on the other hand, anonymizes your connection and makes it difficult to trace your online activities back to you. Combining these tools fortifies your digital privacy, making it an ideal setup for those who prioritize confidentiality.
There are two primary methods to use Tor and a VPN at the same time:
- VPN then Tor (recommended method): First, connect to your VPN, which encrypts your traffic. Then, use the Tor Browser. This method safeguards you from potentially malicious exit nodes on the Tor network and hides your Tor usage from your local network. It’s a straightforward approach, enhancing your privacy without overly complicating the process.
- Tor then VPN (less common): Here, you connect to the Tor network first and then to a VPN. This setup is less common and not widely recommended. It provides an additional encryption layer but doesn’t significantly enhance anonymity. Also, this method can slow down your connection more than the first method.
The level of information visible to websites and networks differs based on whether you use Tor, a VPN, or both. To decide the best solution for your needs, consider what you prioritize more—speed and simplicity or maximum privacy and security.
| Only Tor | Tor then VPN | VPN then Tor | Only VPN | |
| Local network or ISP can read your traffic | No | No | No | No |
| Local network knows your location | Yes | Yes | Yes | Yes |
| Local network or ISP sees you are a Tor user | Yes | Yes | No | N/A |
| Tor entry nodes can see your location | Yes | Yes | No | N/A |
| Tor exit nodes can read your traffic | Yes | No | Yes | N/A |
| VPN can read your traffic | N/A | Yes | No | Yes* |
| VPN knows your location | N/A | No | Yes | Yes* |
*Note: A trustworthy VPN service provider never stores any information about your traffic. You can find out if your VPN provider logs your data by reading their terms of service agreement.
How to securely share files using Tor Browser
While you shouldn’t (and often can’t) use the Tor network to hide your torrent traffic, the Tor browser provides you with one of the most convenient ways to share files with other people. It’s called OnionShare and was developed by Micah Lee. In addition to its security, it is much more convenient than sending email attachments and or using a service like Dropbox.
With Onionshare, you just select the file on your computer, and a link to it is generated. You can then share this link with the intended recipient, via any application. You and the recipient will need to keep the Tor browser open during the entire process. Sharing files using Tor ensures that the sender and recipient never know each other’s locations.
Onionshare is a truly anonymous file-sharing method. Take note, however, that anyone with the link will be able to download the file, so you should share the link in an encrypted fashion, for example with OTR (Off-The-Record).
There is also a neat option that allows you to close the server after the item has been downloaded. That way you can be absolutely certain that the item is only accessed once. If your contact received it, you can be sure no one else did.
Privacy tools for whistleblowers
SecureDrop (originally called DeadDrop) is software that makes it easier to safely leak information to the press over the Tor network. It was originally developed by Aaron Swartz and is currently being maintained by the Freedom of the Press Foundation. It has been adopted by ProPublica, The Intercept, The Guardian, even ExpressVPN.
SecureDrop runs on a server belonging to a journalist or news organization that is only reachable via Tor. The whistleblower can upload any kind of document to this server, for which they receive a code. This unique code can later be used to submit more information or communicate securely and anonymously with the journalists.
Read more: ExpressVPN’s Digital Rights Center offers support for activists and journalists
How to contribute to Tor
While the Tor network is still primarily funded by the United States government, it relies on the efforts of activists and volunteers to stay secure. Additional resources to the project will make it more balanced and less dependent on government and military support. You can help out by doing any of the following.
- Use Tor. You will get internet privacy yourself, and also help to establish the network as an important tool for everyday users.
- Join the Tor community. It’s a platform with useful resources on how you can contribute your skills.
- Become a Tor developer. It is worth major street cred to build on top of the leading anonymity network! You can help bring in whatever skill you have to increase the Tor Project’s security, documentation, and features.
- Donate to the Tor Project. The Tor project accepts PayPal, cryptocurrency, credit card, and more. There is still so much to be done!
- Support initiatives like the Library Freedom Project, which aims to place Tor relays, especially exit nodes, within public libraries.
- Run a relay. If you have extra bandwidth available, you can run a relay from home or your own server.
Alternatives to the Tor browser
Tor is not the only project attempting to make the internet a safer and more anonymous space, although it is by far the most tested and used.
Here are other projects committed to maintaining your internet privacy, security, and freedom:
- Ultrasurf is a proxy system for Windows. It is used primarily to evade censorship, although it also offers some privacy protection with the use of encryption. Like Tor, it is also largely funded by the United States government. Unlike Tor, the source code is not open.
- Freegate is another proxy system for Windows, used to evade censorship. The Freegate network is called Dynaweb and is also funded by the U.S. government.
- Java Anon Proxy is an open-source proxy network written in Java. It was developed by a group of researchers in German universities. Users should be wary of using it though. Java Anon Proxy contains a feature that allows law enforcement to issue surveillance orders for certain servers. Such features carry the risk of abuse similar to that possible on unsecured networks and call the advertised anonymity features into question.
- Astoria, a product of joint research between American and Israeli teams, is a Tor client that minimizes the risk of “timing attacks” that adversaries can use to deanonymize Tor traffic.
Bonus: The unlikely history of Tor
Tor: The early years
The United States armed forces have always relied on a vast network of spies around the globe to gather information. As this information became increasingly digital in the 1990s, the agencies realized how valuable it would be for their assets to communicate online.
No longer would spies need bulky radios, or have to decipher messages in newspapers to receive information. But the U.S. military was also aware that the way the internet was constructed posed serious threats to the identity and security of their sources. It would be very easy to detect who was communicating with servers operated by U.S. intelligence or military.
Imagine an NGO discovering one of their members frequently logs into the members-only forum of a military base, or a large corporation noticing that an employee is frequently opening up the website of a government agency. Without a global network providing anonymity, spies, police, and other government organizations wouldn’t be able to effectively communicate with their sources or carry out covert investigations.
In the mid-1990s, the U.S. Naval Research Laboratory began to work on a solution. They started to develop a way to route encrypted data through a network of computers placed all around the world. This routing method would hide both the origin and the destination of all the data. After 1997, the project was further developed by the Defense Advanced Research Projects Agency (DARPA).
But how would such a network authenticate its users? And how would such a network remain undetected? Who else could profit from being able to access the uncensored internet in an anonymous way?
Public tool instead of secret weapon
We can wildly speculate about these questions, but for historians, it is difficult to determine what debates the military and intelligence organizations involved went through, and which arguments convinced them to release the software for public use, under a free license, in 2002. The responsibility to maintain the project was handed over to the Electronic Frontier Foundation (EFF), which then handed control to The Tor Project. The majority of its funds still come from the United States government, though the government of Sweden also contributes significantly.
The reasons for the government’s involvement in the Tor Project might appear contradictory. The government wants to continue to use the Tor network to obfuscate the source of its attacks, to infiltrate civil rights movements, and to enable its spies to communicate intelligence securely and effectively. On the other hand, they gave the public a tool that would allow anyone to obfuscate the source of their attacks and hide, or information, from the government.
With and against the government
But to be able to use this tool without raising suspicion, the government needs to promote the Tor network as a liberating and empowering technology for those who want to break free from authoritarian control. They needed to not just promote it by spreading the word, but also by making the software genuinely effective and endorsed by the same people the government wishes to gather information on.
The government needed to give up power to maintain power. This complicated balance is probably also the reason the U.S. government has become both an avid supporter and forceful attacker of this technology.
Organizations like the U.S. government are not entirely homogeneous, and no doubt consist of actors who honestly try to protect civil rights, as well as those who wish to strengthen authoritarian structures.
Can a balance be struck between power and freedom?
FAQ: Tor Browser
Can Tor be hacked?
Like any system, Tor isn’t immune to vulnerabilities. The network relies on volunteers’ servers (nodes), and if a node is compromised, it could potentially be used to attack the network. Additionally, users can be vulnerable at the exit nodes of the Tor network, especially if they access non-HTTPS sites. Regular updates and following recommended security practices help mitigate these risks.
Can you be tracked on Tor?
If an attacker is able to gain control of a large portion of the network, they could perform network analysis to correlate traffic on the entry nodes with traffic on the exit nodes. The attacker could then work out who is viewing what content.
This is especially risky for operators of big and popular sites on the dark web who want to keep their location anonymous. The more traffic they attract, the easier it is for an adversary to figure out where their traffic is going.
Why does Tor have a bad reputation?
The dark web is known for hosting a large variety of illicit content. In 2011, the online marketplace “The Silk Road” gained notoriety for allowing users to offer and purchase drugs and contraband. As servers reachable through .onion domains are difficult to locate and their domains impossible to seize, the Tor network theoretically provides ideal shelter from censorship and the reach of the law.
However, most offers on the dark web, from weapons to pornography and drugs are scams created to part curious visitors from their Bitcoin.
Is it illegal to use the Tor Browser?
Using Tor is not legally distinct from using any other browser, and surfing the dark web is not different to surfing the regular internet. In some places, mainly authoritarian countries with heavy censorship, using Tor is both necessary and can be regarded as subversive.
Offering or buying narcotics on the dark web is illegal whenever it would be illegal to do so on a regular website. In most jurisdictions, browsing a site offering illegal content is not illegal, but storing (e.g., screenshotting) such content and storing it on your own device will be.
The Tor Browser is built for privacy and security, but don’t let it lower your guard. Be mindful of what information you surrender on the dark web, and do not download and install software from there.
What’s the difference between Tor and a VPN?
Tor and VPNs (both aim to enhance your online privacy, but they operate differently. Tor routes your internet traffic through a network of volunteer-operated servers, making it hard to trace the traffic back to you. This makes Tor highly effective for anonymity and bypassing censorship but can slow down your internet speed. VPNs, on the other hand, route your internet traffic through a secure, encrypted tunnel to a server operated by the VPN provider. This change in IP address helps maintain privacy and security, but VPNs do not anonymize traffic to the same extent as Tor.
For everyday internet activities, a VPN is often more practical than Tor. VPNs generally provide faster and more stable connections, making them ideal for streaming, downloading, and secure browsing. They are user-friendly and can protect all the internet traffic on your device, including applications beyond your web browser. While Tor is excellent for maximum anonymity, especially for sensitive activities, a VPN strikes a balance between privacy, security, and convenience. For users seeking a reliable VPN for daily use, consider downloading a VPN from ExpressVPN.
Is Tor Browser safer than VPN?
The safety and suitability of Tor Browser versus a VPN depend largely on your specific online needs and activities.
- Tor Browser is designed for maximum anonymity. It routes your internet traffic through multiple nodes, making it extremely difficult to trace activity back to you. This makes it highly secure for tasks where anonymity is paramount. However, this level of security can come with downsides, such as slower browsing speeds and potential vulnerabilities at exit nodes, especially if accessing non-HTTPS sites.
- VPNs, on the other hand, provide a direct, encrypted tunnel between your device and the internet. This encrypts your data, offering strong protection against eavesdropping and local network surveillance. VPNs typically offer faster speeds and a more user-friendly experience, making them suitable for everyday use like streaming, downloading, and browsing.
How can I connect to Tor when it’s blocked?
Some networks ban any kind of Tor traffic through their systems by blacklisting all known entry nodes. To get around this ban, you can connect to a bridge. A bridge functions similarly to an entry node, except that you have to obtain IP addresses manually. Using a bridge to connect to the Tor network does not have any significant drawbacks, but in many situations will not be able to circumvent Tor obstructions. For better results, first connect to your VPN, then to the Tor network.
When you are connected with a VPN, neither the sites you are visiting nor the Tor entry nodes will know your true location, though the VPN company will. However, the VPN company cannot see the content of your traffic, even if they tried to, as the traffic is encrypted between you and the Tor entry node.
Theoretically, there is also the option of connecting first to the Tor network, then tunneling a VPN through it. This makes it impossible for your VPN provider to know where you are, and ensures exit nodes can’t read or alter your traffic. This helps little with anonymity, however, which is why most VPN providers do not support this function.
Depending on whether you use Tor, VPN, or a combination of the two, sites and networks can see different information about you.

Protect your privacy with the best VPN
30-day money-back guarantee

























Comments
Excellent article top to bottom…thanks
I like the dark web
Excellent article, very high quality!
Hello dear,
Should I need to set IP address and Port No. in the Tor?If yes,how/where can I check the IP address and Port No.? For windows 10;If no,is that mean firstly make VPN connetion,then directly make Tor connect? Hope to get your kindly and detail sharing,thanks so much
Oue oue
Looking forward to using your app…
very informative article. excellent job. thank you.
Hola es muy bien