We all want to browse the internet without being tracked by cybercriminals, companies, and advertisers. That’s where privacy tools come in. But with so many options available, it can be hard to know which one is right for you.
Two of the most popular privacy tools are Tor and VPNs. Both offer strong encryption and can help you hide your online activity. But they have different strengths and weaknesses:
- Tor is free, open-source software that allows you to browse the internet (including the dark web) anonymously. It does this by routing your traffic through a series of volunteer-run servers, making it difficult for anyone to track your real IP address. However, Tor can be slow and unreliable, making it not great for streaming or gaming.
- VPNs encrypt your traffic and route it through a server in another location. This can help you stay private and improve your online security. VPNs are fast, so you barely notice a difference in internet speeds when you use them. However, a high-quality VPN costs money.
You can use a VPN and Tor together, but one will also suffice for strong security. So, which one should you choose? We’ll help you decide by explaining the main differences between Tor and VPNs and how they can make your online experience safer.
Jump to…
Tor vs. VPN: At a glance
What is Tor?
How does Tor work?
Is Tor safe?
Is Tor legal?
Tor: Pros and cons
What is a VPN?
How does a VPN work?
VPN: Pros and cons
VPN & Tor: Can they be used at the same time?
Verdict: Which is better, Tor or VPN?
Tor vs. VPN: At a glance
| Tor | VPN | |
| Main purpose | Anonymity | Privacy |
| How it works | Encrypts traffic and routes it through a network of volunteer-operated servers, using three hops | Encrypts traffic and routes it through a VPN server in a different location |
| Strengths | Anonymity; nearly impossible to trace; bypassing censorship; free and open-source; decentralized; access to the dark web | Secured connections; bypassing censorship; fast internet speeds; easy to use; covers all traffic from a device; rarely blocked by sites |
| Weaknesses | Slow speeds; not user-friendly; only works for Tor browser traffic (not other traffic like apps); blocked by many sites | High-quality VPNs come with a subscription fee; it’s possible for VPN providers to see your traffic; requires high trust |
What is Tor?
Tor, short for “The Onion Router,” is a free and open-source software that enables anonymous internet browsing. It achieves this by routing your online traffic through a network of volunteer-operated servers called Tor relays. These relays only know about the ones before and after them, ensuring your complete browsing history remains private.
Similar to a VPN, Tor can hide your IP address, while also providing access to the dark web—a part of the internet that’s not indexed by search engines. Dark web sites, also called onion sites, provide platforms for journalists, activists, and other people in repressive countries to communicate safely and anonymously. Whistleblowers and others who need anonymity would turn to Tor as well. It helps thwart attempts by ISPs, government agencies, and hackers to track your online activities. This is also why criminals use Tor for illegal activities, such as the sale of illegal goods and services.
However, it’s important to note that Tor is slower and less efficient than standard internet browsing. Part of the inefficiency comes from sites blocking Tor. Moreover, it only works in the Tor Browser, meaning your device’s apps and other traffic are not protected.
Learn how to set up and start using Tor
How does Tor work?
Tor operates as a layered series of proxy servers, which is why it’s called “The Onion Router.” These layers add a level of anonymity to your internet traffic by obfuscating its origin.
Three-hop routing
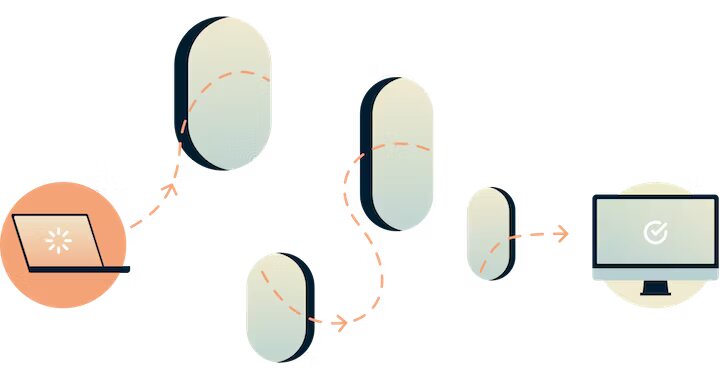
When you use Tor, your data goes through at least three different nodes or servers:
- Entry node: This is the first server your data passes through. It knows your IP address because you initiate the connection from your device.
- Middle (relay) node: The middle node acts as an intermediary between the entry and exit nodes. It ensures that the exit node does not know the source (entry node) of the traffic, adding an extra layer of anonymity.
- Exit node: The exit node is the last server your data passes through before reaching its destination. It knows the destination website but doesn’t know your identity.
Enjoy anonymity
By routing your traffic through this series of nodes, Tor effectively separates your IP address from the destination website. This makes it extremely difficult for anyone, including eavesdroppers and middlemen, to determine your identity or track your online activities.
Using the Tor Browser
To access the Tor network, users typically use the Tor Browser, which is based on Firefox but optimized for security and privacy. Unlike most other web browsers that prioritize speed, the Tor Browser is designed to protect your online anonymity and defend against various forms of tracking, such as browser fingerprinting.
Read more: Best (and worst) browsers for privacy in 2023
Is Tor safe?
Tor is generally considered safe, but it’s not 100% secure. While it’s a powerful tool for enhancing online privacy, accessing the dark web, and protecting your identity, there are some risks associated with using Tor that you should be aware of:
- Exit node risks: The final server in the Tor network chain is the exit node. While your traffic is encrypted within the Tor network, it’s decrypted at the exit node before reaching its final destination on the public internet. This means that if the exit node is operated by someone with malicious intentions, they could potentially see your unencrypted traffic and track your online activities. To mitigate this risk, it’s essential to use websites that use HTTPS encryption, as this provides an additional layer of security.
- Malware: Many people use Tor to access the dark web, and onion sites, often full of sketchy content, are particularly likely to have malicious links. It’s highly risky to click on links or download files on onion sites unless they are reputable.
- Phishing: Phishing is a common method used by cybercriminals to steal personal information. Because the activity on Onion sites is untraceable, criminals are more likely to attempt to phish your information. Stay vigilant and only enter your personal information on trusted websites.
- Traffic identifiability: If your Tor usage results in significantly high traffic, it could potentially make you identifiable among other users. While Tor is designed to provide anonymity, patterns in traffic could potentially be used to de-anonymize users.
How to stay safe while using Tor:
- Consider using a VPN in addition to Tor: A VPN can further enhance your privacy by encrypting your traffic before it enters the Tor network (more on this later).
- Practice safe browsing habits: Avoid plugins or downloads from untrusted sources, as malicious exit nodes could compromise your anonymity.
- Be cautious about the websites you visit on Tor: Especially on the dark web, as some dark websites may contain malicious content.
- Don’t give yourself away: If your goal is high anonymity, be careful not to reveal any identifying details. Hackers and criminals operating on the dark web often get caught not through technical means but because they let slip information about themselves in conversations.
Is Tor legal?
Yes, it’s completely legal to use Tor. It serves a variety of legitimate purposes, such as giving anonymity to dissidents, whistleblowers, journalists, and activists who require secure and covert communication. Additionally, many individuals use Tor to access websites censored in their respective countries—for example, certain social media platforms and news sites.
However, it’s important to understand that while Tor itself is legal, conducting illegal activities remains illegal, whether you are using Tor or not. Your actions are subject to your country’s laws.
Tor: Top 5 pros and cons
If you’re considering the use of Tor for online anonymity, it’s important to weigh its advantages and disadvantages first.
| Pros | Cons |
| 1. Provides anonymity: Tor’s complex encryption process makes it difficult for websites and other organizations to track your online activity. | 1. Slow speeds: Because your traffic is relayed through several hops, Tor can slow down your internet connection. Therefore, you’ll probably find it difficult to stream, download, or file-share when using Tor. |
| 2. Available for free: Tor is a free and open-source software, so anyone can use it. You just need to download the Tor Browser or Brave browser (which offers Tor functionality) | 2. Security challenges: Tor isn’t completely secure. It relies on volunteers to operate nodes, which may result in inconsistent security. Tor’s entry node can also reveal your IP address to your ISP, compromising anonymity. |
| 3. Can be used on any device: Tor can be used on any device that has an internet connection, including computers, smartphones, and tablets. | 3. Complex setup: Setting up and configuring Tor can be difficult for users who aren’t tech-savvy. |
| 4. Access to the dark web: Tor allows access to the dark web, enabling users to browse hidden websites. | 4. Blocking: Some network administrators block Tor, preventing you from accessing their websites. |
| 5. Decentralized: Tor operates on a decentralized, open-source network with no central monitoring or surveillance, making it difficult to shut down or intercept. | 5. Country-specific IP: Configuring connections or multiple reconnections may be needed if you want to connect a node to a country-specific IP address. |
What is a VPN?
A VPN, which stands for Virtual Private Network, is a type of technology that provides a securely encrypted internet connection for users. It creates a protected tunnel for your online data, safeguarding it from hackers, government surveillance, and ISPs. This encryption ensures that all your online activities, from website visits to file downloads, remain private and inaccessible to anyone other than the intended recipient.
A VPN also provides privacy by concealing your real IP address, replacing it with the IP address belonging to the VPN company. This shields your online identity, preventing websites and advertisers from tracking your location and online habits. Additionally, the IP change enables users to circumvent censorship and access restricted content, giving them greater online freedom.
VPNs aren’t just for individuals; businesses use them to establish secure connections for remote workers. Corporate VPNs allow geographically dispersed staff to access company resources as if they were in the same physical office, providing data security and collaborative work.
What’s the difference between a VPN and Tor?
Both provide high degrees of online privacy, but Tor offers greater anonymity. However, Tor is nowhere near as user-friendly as a VPN.
A VPN encrypts and routes all of a device’s traffic through a secure server run by the VPN company. A reputable VPN company keeps users’ online activity private by not logging that information.
Tor, on the other hand, anonymizes your browser traffic (but not other traffic on your device) by routing it through a series of volunteer-operated servers using at least three hops, making it difficult to trace your actions back to you.
How does a VPN work?
A VPN works by creating a secure and private connection between your device and a remote server. This connection is encrypted, so your data is protected from prying eyes. The VPN server acts as a proxy between your device and the internet, so the websites and services you visit only see the IP address and location of the VPN server, not your actual information.
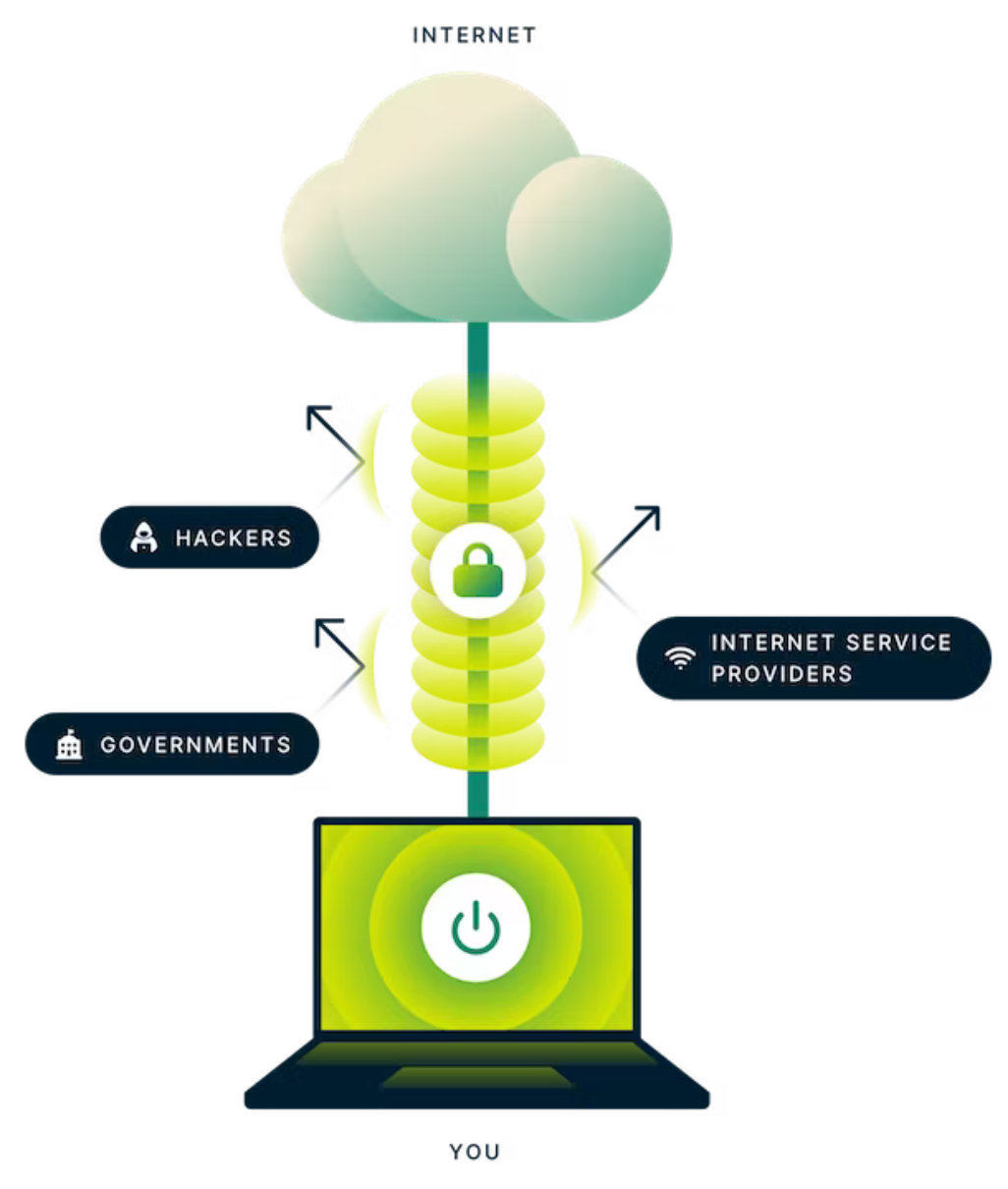
Here’s how this works:
- Establishing a secure connection: When you connect to a VPN, your device first establishes a secure encrypted tunnel to a remote server. This tunnel is created using a tunneling protocol, such as OpenVPN, ExpressVPN’s own Lightway, or L2TP/IPsec.
- Encrypting data packets: Once the secure tunnel is established, your data is encrypted before it is sent over the internet. This encryption makes it impossible for third parties, such as your ISP or hackers, to intercept and read your data. (Learn more about VPN encryption.)
- Routing through VPN server: The encrypted data is then routed through the VPN server. The VPN server acts as a proxy between your device and the internet. This means that the websites and online services you visit only see the IP address and location of the VPN server, not your actual IP address and location.
- Enhancing anonymity: The VPN server’s IP address is shared among numerous users, which further enhances your online anonymity. Even if someone were able to track your data back to the VPN server, they would not know who was responsible for the traffic based on the IP alone.
Overall, a VPN is a powerful tool that can help to protect your privacy and security online. It can be used to:
- Change your IP address and virtual location, protecting your privacy
- Encrypt your traffic, preventing unauthorized access to your data
- Unblock websites and content
- Improve your online speed and performance, if your ISP had been throttling your connection
VPN: Top 5 pros and cons
VPNs can be a great way to protect your privacy and security online, but there are also some potential drawbacks to consider—especially if you want to use a free VPN.
| Pros | Cons |
| 1. Online privacy: VPNs encrypt your data and hide your IP address, which can help to protect your online privacy. Websites and online services you access will only see the VPN company’s IP address, so they won’t be able to track your activity or know your real location. | 1. Cost: A premium VPN service typically costs money. Although there are a few free options available, these are often not privacy-focused and are mainly good for unblocking content. The cost of a VPN service will vary depending on the features, the number of devices you want to use it on, and the length of the subscription plan. |
| 2. Advanced security features: VPNs can offer a variety of advanced security features, such as encryption—which makes it much more difficult for hackers to intercept—as well as a kill switch feature that will disconnect your internet connection if the VPN connection drops. This is especially important when using public Wi-Fi networks, as these networks are often not secure and your data could be intercepted by hackers. | 2. Some VPNs collect user and connection logs: VPNs have the ability to collect user data, including your IP address, browsing history, and DNS queries. If privacy is your priority, it’s recommended that you use a premium service like ExpressVPN with a strict no-logs policy. It’s important that the company takes extensive measures to protect user privacy and has ways of validating those claims. |
| 3. Easy to use: VPNs are relatively easy to use. Most VPN services offer software for download in the form of apps. All you have to do is turn the VPN on or off to control it. | 3. VPNs are banned in some countries: VPNs are banned in some countries, such as ones with strict censorship laws. These countries view VPNs as a way to circumvent these laws, so using a VPN in places where it’s banned could result in fines. |
| 4. Can be installed on every platform: VPNs can be installed on a variety of platforms, including Windows, Mac, Linux, iOS, and Android—making them a versatile tool that can be used by people with a variety of devices. | 4. Some websites and services block VPNs: Some websites and services block VPNs in an attempt to prevent users from accessing their content from other countries, as well as to maintain their ability to collect user data. |
| 5. Protects your whole device: VPNs can be installed on a variety of platforms, including Windows, Mac, Linux, iOS, and Android. When you use a VPN, all traffic on that device is protected, including all browsing and apps. | 5. Use of processing power: VPNs add to your device’s battery use and data use. This could mean a slower internet experience and a faster-draining battery. But the best VPNs aim to mitigate these issues to only a minor effect. |
VPN and Tor: Can they be used at the same time?
Yes—not only is using Tor and a VPN together possible but it’s also recommended for maximum privacy and anonymity. However, if you value speed and simplicity, using just a VPN may be a better option.
How to use Tor and VPN at the same time
There are two methods you can use to combine Tor and VPN:
- VPN then Tor: This is the most recommended method. You would first need to connect to a VPN server and then open the Tor Browser. This way, the Tor network will be protected from malicious exit nodes. You will also not have to worry about being flagged by your home network for using Tor, as all that network will see is encrypted traffic to your VPN server.
- Tor then VPN: This method is less common and not recommended by most VPN providers. You would first connect to the Tor network and then connect to a VPN server. This method doesn’t offer as much anonymity as Tor over VPN, and it can also slow down your internet connection.
The level of information visible to sites and networks depends on whether you use Tor, a VPN, or both. To find the best solution for your needs, refer to the table below:
| Only Tor | Tor then VPN | VPN then Tor | Only VPN | |
| Local network or ISP can read your traffic | ❌ | ❌ | ❌ | ❌ |
| Local network knows your location | ✅ | ✅ | ✅ | ✅ |
| Local network or ISP sees you are a Tor user | ✅ | ✅ | ❌ | N/A |
| Tor entry nodes can see your location | ✅ | ✅ | ❌ | N/A |
| Tor exit nodes can read your traffic | ✅ | ❌ | ✅ | N/A |
| VPN can read your traffic | N/A | ✅ | ❌ | ✅* |
| VPN knows your location | N/A | ❌ | ❌ | ✅* |
*Note: A trustworthy VPN service provider never stores information about your traffic. You can find out if your VPN provider logs your data by reading their terms of service.
Verdict: Which is better, Tor or VPN?
The decision between Tor and VPN depends on your specific needs and preferences. If you’re looking for a smooth, clear-cut browsing experience with strong privacy safeguards, a VPN is the clear winner.
It’s widely available, uses advanced encryption protocols, and is a reliable way to protect your online activities. It also won’t slow down your internet connection as much as Tor. Just make sure you opt for a reputable VPN service provider like ExpressVPN.
However, if complete anonymity is what you’re after, even if it means slower speeds, we strongly recommend using Tor and a VPN together for an added layer of defense.
Summary: The key differences between Tor and VPN
| Tor | VPN | |
| Anonymity | High | Medium |
| Speed | Slow | Fast |
| Security | Medium | High |
| Cost | Free | Usually paid |
| Features | Fewer features | More features, such as kill switch and easy location changes |
FAQ: About Tor vs. VPN
Do I need Tor and a VPN?
No, you don’t need to use a VPN with Tor. Tor is a privacy-focused web browser that routes your traffic through a network of volunteer-run servers, which makes it difficult for anyone to track your online activity. However, using a VPN with Tor can add an additional layer of security by encrypting your traffic before it enters the Tor network. This can help to protect you from malicious exit nodes, which are Tor nodes that can see your real IP address.
Is Tor a VPN?
No, Tor is not a VPN. Tor, short for “The Onion Router,” is a decentralized network that routes your internet traffic through a series of volunteer-operated servers, providing anonymity. A VPN, on the other hand, creates an encrypted tunnel between your device and a remote server, offering privacy and security. While both aim to enhance online privacy, they operate on different principles and have distinct use cases.
Is Tor more anonymous than a VPN?
Yes, Tor is generally considered to be more anonymous than a VPN. This is because Tor routes your traffic through a network of volunteer-run servers, which makes it more difficult for anyone to track your real IP address. However, a VPN can also provide a high degree of anonymity, especially if it is used with a reputable provider like ExpressVPN.
Is Tor safer than a VPN?
In some ways, Tor is considered safer than a VPN. Tor is great for anonymity and has a reputation for protecting people’s identity online, and much of that stems from its use to access the dark web, which a VPN cannot provide. However, Tor is more difficult to use than a VPN. A VPN is able to significantly increase a user’s privacy and security while still providing a smooth internet experience with easy-to-use apps.
Here are some of the ways a VPN is superior to Tor:
1. Encryption: A VPN encrypts all of your traffic, including your browsing, app traffic, and file transfers. This makes it much more difficult for anyone to track your online activity. Tor only encrypts your browsing traffic, so your ISP and other third parties can still see what websites you are visiting.
2. Trusted providers: There are many reputable VPN providers that have a good track record of privacy, such as ExpressVPN. Tor is a volunteer-run project, so it’s more difficult to know who is running the network and how your data is being handled.
3. Performance: A VPN has much higher speeds compared to Tor which can significantly slow down your internet connection—especially if you are using it to download large files.
Do I need Tor if I have a VPN?
No, you don’t need Tor if you have a VPN. A VPN can already encrypt your traffic and hide your IP address, which are the main things that Tor does. So, if you are already using a VPN, there is no need to use Tor as well.
However, there are some cases where using Tor with a VPN can be beneficial, such as:
1. Concerns about anonymity: Tor is good for protecting your anonymity, so using Tor with a VPN can add an extra layer of protection. This is particularly relevant if you don’t fully trust your VPN service to not log and store your online activity.
2. Accessing the dark web: If you intend to access onion websites on the dark web, you’ll need to use Tor. While a VPN provides encryption, it doesn’t grant access to these specific domains.
Does the Tor browser hide your IP?
Yes, the Tor browser hides your IP address by routing your traffic through a series of volunteer-run servers called Tor relays. This makes it difficult for anyone to track your online activity, including your ISP, government agencies, and websites you visit.
It does this by using a technique called onion routing. Onion routing encrypts your traffic multiple times and routes it through a series of Tor relays. Each relay only knows the IP address of the relay before it and the relay after it. This makes it difficult to trace your traffic back to your original IP address.
What are the critical differences between Tor and VPN?
There are four key differences between Tor and VPN:
1. Routing your traffic: Tor routes your traffic through a network of volunteer-run servers, while a VPN routes your traffic through a server owned by the VPN provider.
2. Security and privacy: A VPN encrypts all the traffic coming from your device, whereas Tor only protects what you do in the Tor Browser.
3. Speed: VPNs are faster than Tor because they do not encrypt your traffic as many times. This can make a big difference in the speed of your internet connection, especially if you are streaming or downloading large files.
4. Cost: Tor is free to use, whereas high-quality VPNs typically come with a price tag. However, there are also free VPNs available, but they may not be as secure or reliable as paid VPNs.

Take back control of your privacy
30-day money-back guarantee